I solved a few questions, but couldn't solve the others -_-|
modbus#
The question provided a modbus.pcapng traffic file.
![]()
Open it with Wireshark, analyze the packets, and search for 666c. The hex decoding of 666c is the hexadecimal encoding of the flag. Export the packet analysis results as plain text.

Use grep to extract characters.

Remove the preceding "Data: 2400" and the repeated characters at the end, resulting in:
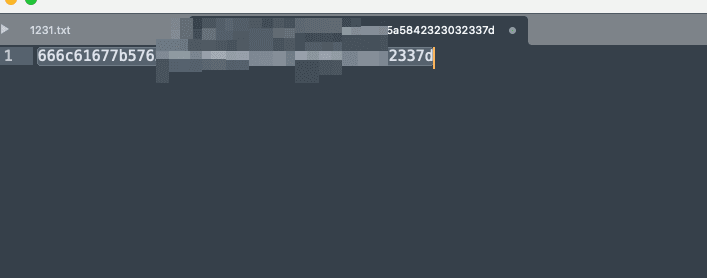
Decode the hex to obtain:

s7error#
The question provides a hint.

According to the hint, it is speculated that S7Error needs to find the packet with an error, and the hint suggests that a resource exception is needed. Therefore, find the packet with the resource exception error code.
Use Wireshark to filter out packets with err code not equal to 0x00 (no error):
((s7comm) && (s7comm.header.rosctr == 3)) && (s7comm.header.errcod != 0x00)

The error code is 0x83.

Therefore, it is speculated that the number is in the line 213056, so the flag is:
flag{213056}
The Secret of the Project#
When opened, it is a PNG image. Use LSB steganography. Open it with Stegsolve to obtain a compressed file. Extract it to get the cmp file. Open the cmp file with GX Works2.

Install GX Works2. It requires version 7.0 or above.
After installation, restore the project.

After successful restoration, the flag is located at the traffic light.

Malicious Instruction#
Open with IDA and decompile using F5.

ASCII encoding.

Encrypted Project#
Likon
Install the demo version.
Requires version 7.1, as version 7.2 cannot restore the project.
Click on "Restore" and select the PCZ file.
Import successful.
Click on "Development".
The software prompts that it cannot be opened due to encryption and that there may be a problem with the software installation. I have downloaded 3 or 4 versions of this software, but it still doesn't work.
Reference: Writeup written by a great person.