
SSH Port Forwarding#
During the process of lateral movement in a network, if the target machine is a Linux server, you can use SSH to perform network proxy operations, with dynamic forwarding being the most commonly used method.
There are three types of port forwarding modes in SSH:
-
Local forwarding (-L parameter)
-
Remote forwarding (-R parameter)
-
Dynamic forwarding (-D parameter)
-
Attacker machine: The machine used by the attacker
-
Target machine: The machine that the attacker needs to access, which cannot be accessed directly
Local Forwarding#
Local forwarding, as the name suggests, forwards the local host port to the remote host port through the target host port.
Local forwarding is specified using the -L parameter, with the format: ssh -L [attacker machine IP]::: @
Consider the following scenario:
The attacker controls a Linux server (target machine) through the attacker machine and obtains the account password. There is also a target machine that is located within the internal network and cannot be accessed directly by the attacker machine. The topology is similar to the diagram below.
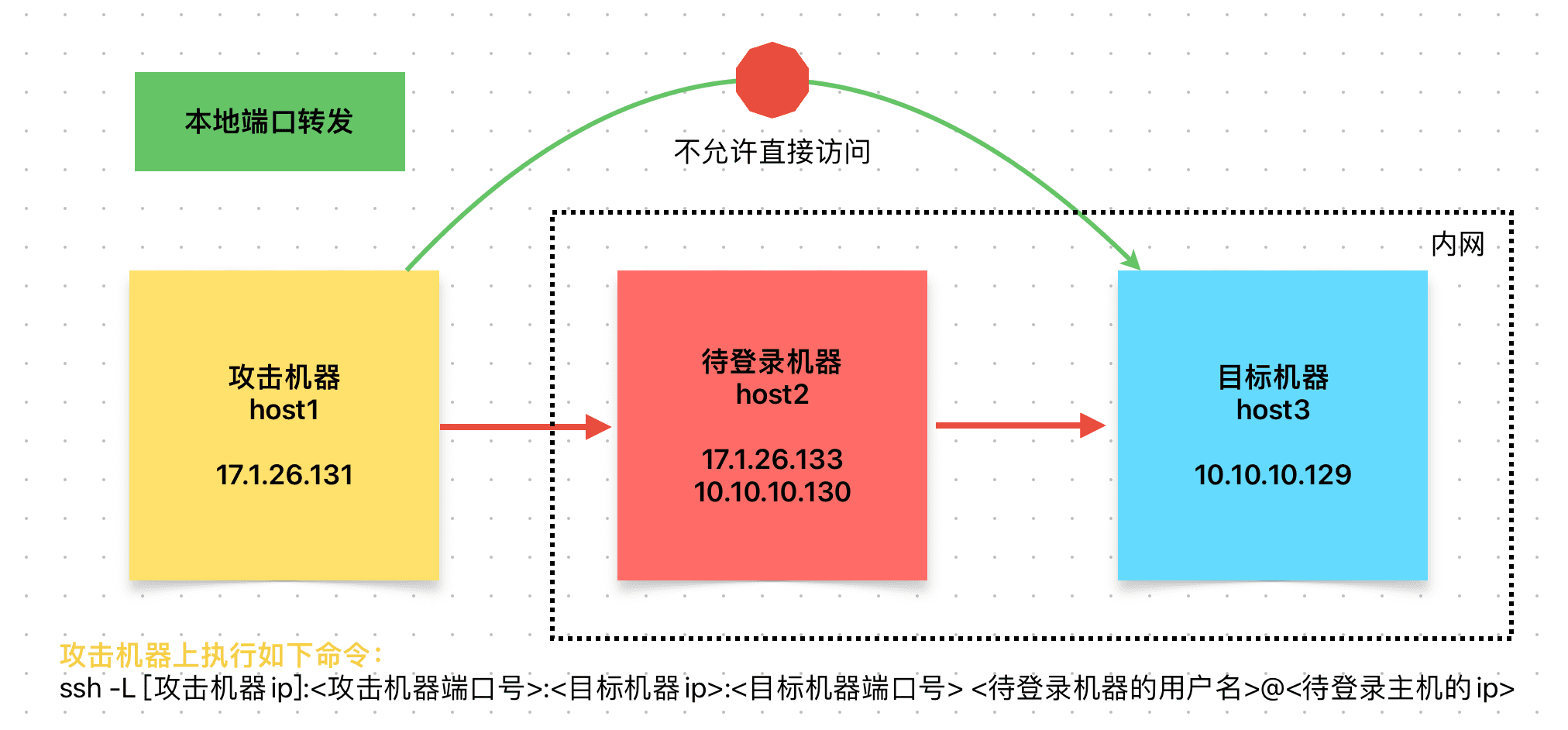
In this case, how can host1 access host3?
It can only be done through host2 for forwarding. host2 acts as an intermediary, transmitting encrypted data between host1 and host3.
Suppose host3 has a web service running on port 80, and host1 needs to access this web service. The following steps can be taken to achieve local port forwarding by connecting to host2 via SSH on host1.
Steps on host1
ssh -L 0.0.0.0:8888:10.10.10.129:80 [email protected]
- The attacker machine IP is optional and can also be written as follows:
ssh -L 8888:10.10.10.129:80 [email protected]
This command maps port 80 of the target machine to port 8888 of the attacker machine. At this point, the attacker can access port 8888 locally to access port 80 of the target machine.
Remote Port Forwarding#
Consider the following scenario, which is not common in penetration testing: host1 does not allow direct access to host3, host2 can access host3, but host1 cannot access host2, and host2 can access host1. In this case, remote port forwarding is used.

Steps on host2
ssh -R 0.0.0.0:8888:10.10.10.129:80 [email protected]
Alternatively, it can be written as
ssh -R 8888:10.10.10.129:80 [email protected]
This command maps port 80 of the target machine (host3) to port 8888 of the login machine (host2). At this point, the attacker can access port 8888 locally to access port 80 of the target machine (host3).
Dynamic Port Forwarding#
Dynamic forwarding is specified using the -D parameter.
Format: -D [local host:]local host port
Compared to the previous two methods, dynamic forwarding does not require specifying the remote host and its port, and data transmission is done through the SOCKS protocol.
Consider the following scenario:
The attacker controls a Linux server (target machine) through the attacker machine and obtains the account password. There is also a target machine that is located within the internal network and cannot be accessed directly by the attacker machine. The topology is similar to the diagram below.

Steps on the attacker machine (host1)
ssh -D 127.0.0.1:8888 [email protected]
It can also be written as
ssh -D 8888 [email protected]
This command creates a SOCKS proxy, and all data packets sent through this SOCKS proxy will be forwarded through host2.
How to use it?
- In the Firefox browser, set the SOCKS5 proxy to 127.0.0.1:8888, and then the browser can access any IP within the network where
host2is located. - If it is a regular command-line application, use proxychains-ng. The command can be referenced as follows:
brew install proxychains-ng
Edit the configuration file
vim /usr/local/etc/proxychains.conf # Add the configuration "socks5 127.0.0.1 8888" under the ProxyList section
Access the target network
proxychains-ng wget http://10.10.10.129 # Add proxychains-ng before other command-line commands
Common parameters for building SSH tunnels:
-C: Compresses the transmission to improve speed.
-f: Runs the data transmission in the background.
-N: Establishes a silent connection.
-g: Allows remote hosts to connect to local ports for forwarding.
-L: Local port forwarding.
-R: Remote port forwarding.
-D: Dynamic forwarding, i.e., SOCKS proxy.
-p: Specifies the SSH connection port.
Experimental Environment Setup#
Environment Configuration#
- Attacker machine
- 17.1.26.131

- Login machine
- 17.1.26.133
- 10.10.10.130

- Target machine
- 10.10.10.129

Local Port Forwarding#
Execute the following command on the attacker machine (host1):
ssh -L 8888:10.10.10.129:80 [email protected]

Check the port status on the attacker machine (host1) to see that port 8888 is being listened to.

Open a browser on the local host and access port 8888 to see if it can be accessed successfully. Access http://127.0.0.1:8888/123.asp.

Remote Forwarding#
The environment is the same as before, and the command parameters are as follows. Enter the following command on the login machine (host2):
ssh -R 8888:10.10.10.129:80 [email protected]

Go back to the local host and check if the port is open with netstat -tnlp. It shows that port 8888 is open.

At the same time, open a browser and access http://127.0.0.1:8888/123.asp to see if it can be accessed successfully.

Dynamic Forwarding#
The environment is the same as before, and the command parameters are as follows. Execute the following command on the attacker machine (host1) and enter the SSH login password:
ssh [email protected] -D 55555

Check the port status on the attacker machine (host1).

Set the browser SOCKS proxy on the attacker machine (host1).

Access http://10.10.10.129/123.asp directly in the browser on the attacker machine (host1).

References#
https://jeremyxu2010.github.io/2018/12/ssh 的三种端口转发 /
https://www.ruanyifeng.com/blog/2011/12/ssh_port_forwarding.html
https://reznok.com/ssh-tunneling-magic/
Images from