Scene Description
Alonzo discovered some strange files on his computer and notified the newly formed SOC team. After assessing the situation, it was believed that a Kerberoasting attack might have occurred on the network. Your task is to confirm these findings by analyzing the provided evidence. The information you have includes: 1. Security logs from the domain controller 2. PowerShell operation logs from the affected workstation 3. Prefetch files from the affected workstation
The attached content includes the domain controller's logs, PowerShell logs, and prefetch files.
Task 1 Analyze the domain controller security logs. Can you confirm the exact date and time of the Kerberoasting activity?
The event IDs for Kerberoasting are 4768 and 4769, where 4769 indicates a requested Kerberos ticket, and 4768 indicates a Kerberos TGS request.
The following image searches for 4769, with Ticket Encryption Type being 0x17, while the others are 0x12.
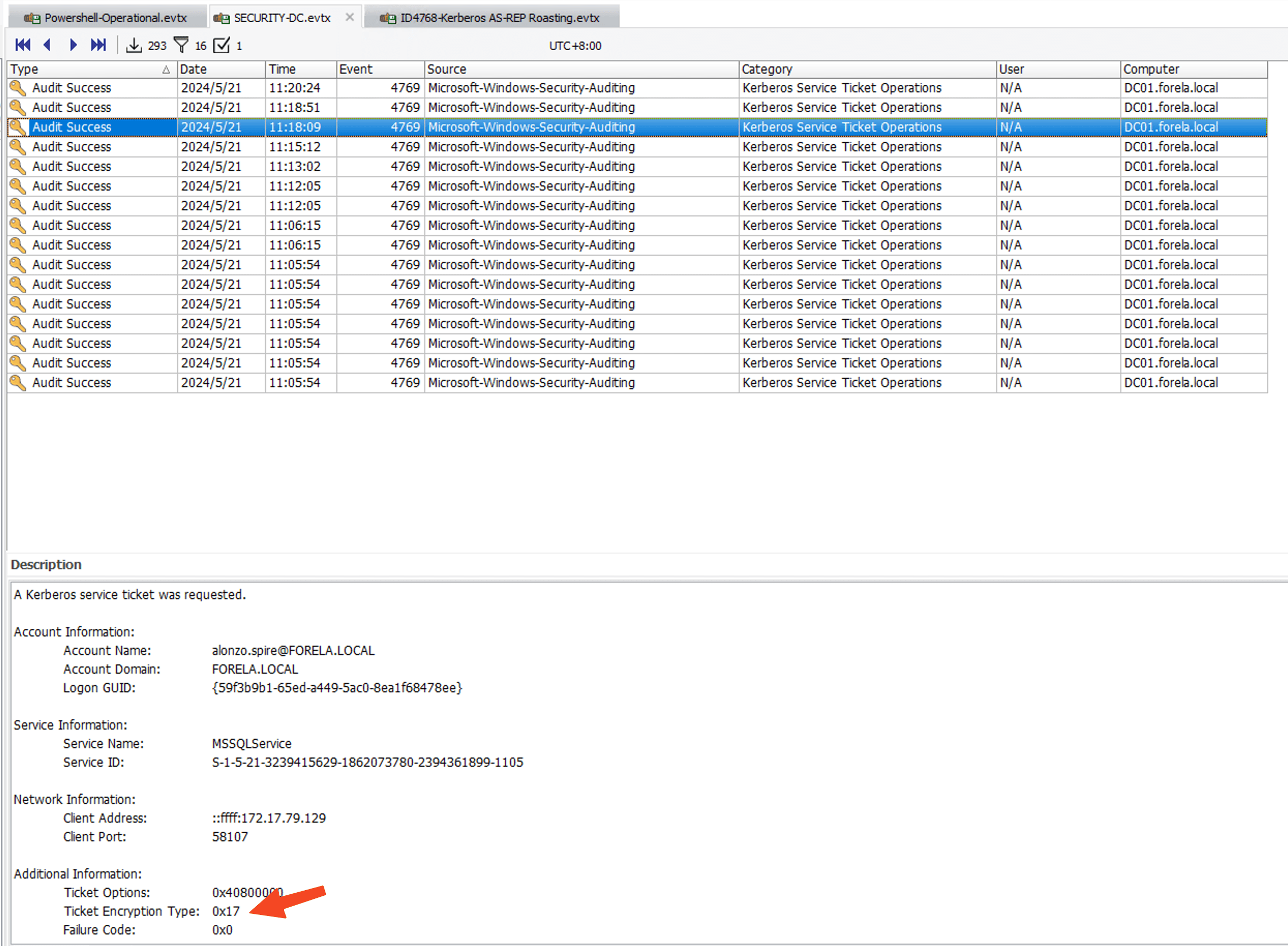
Note the time zone: 2024-05-21 03:18:09
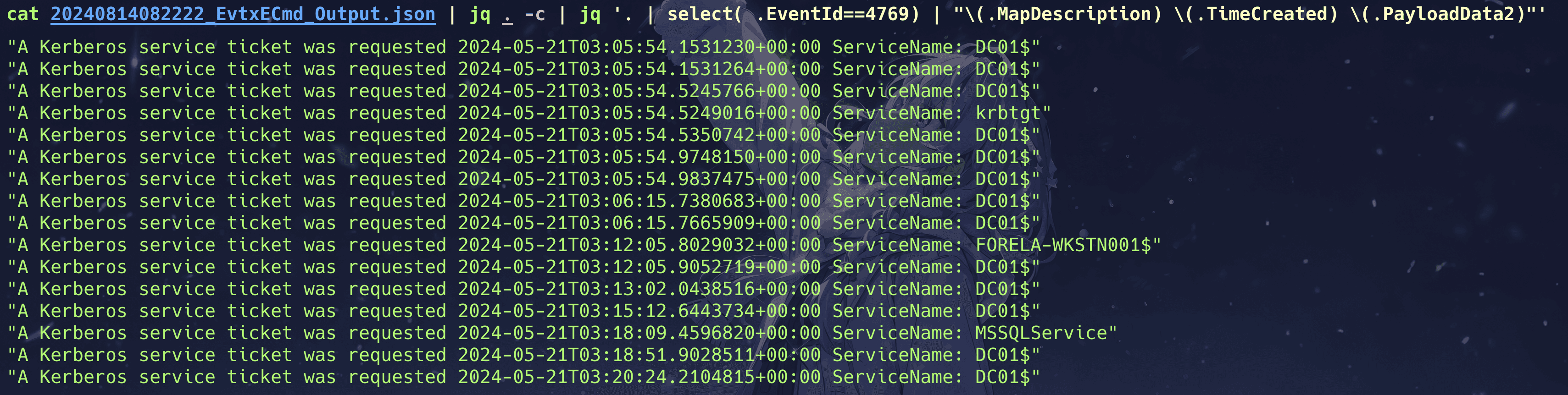
Task 2 What is the name of the targeted service?
By using EvtxECmd to extract the evtx logs, and then filtering with jq for EventID 4769, as follows:
cat 20240814082222_EvtxECmd_Output.json | jq . -c | jq '. | select( .EventId==4769) | "\(.MapDescription) \(.TimeCreated) \(.PayloadData2)"'
It can be determined that there is a MSSQLService.
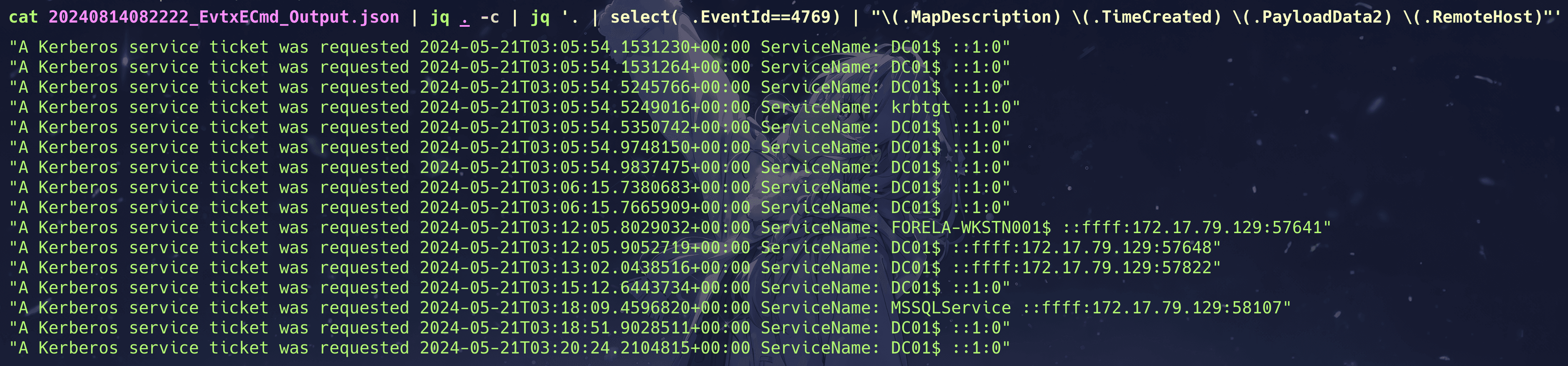
Task 3 It is very important to determine which workstation this activity occurred on. What is the IP address of this workstation?
cat 20240814082222_EvtxECmd_Output.json | jq . -c | jq '. | select( .EventId==4769) | "\(.MapDescription) \(.TimeCreated) \(.PayloadData2) \(.RemoteHost)"'
172.17.79.129
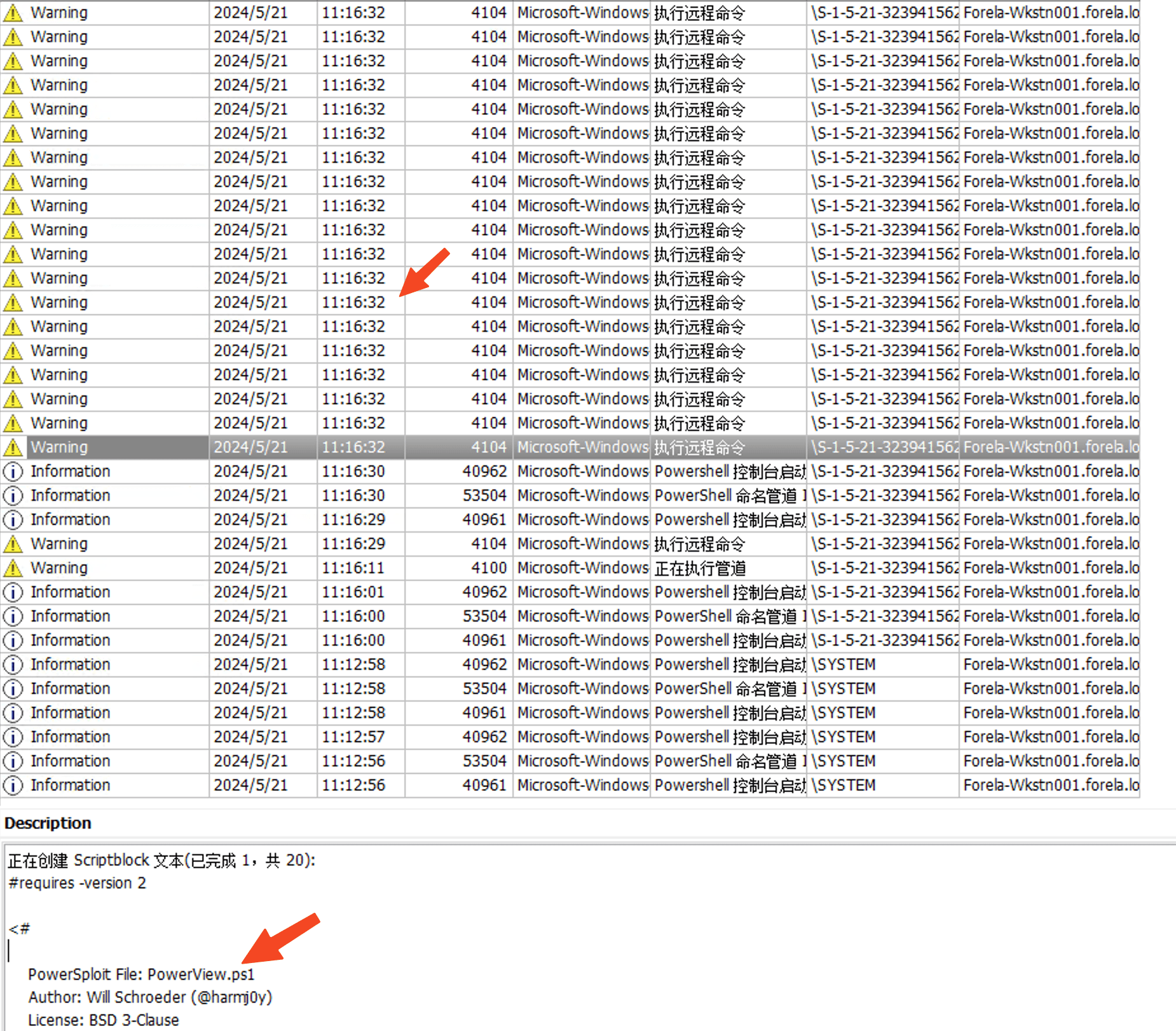
Task 4 Now that we have identified the workstation, to gain deeper insight into how this activity occurred on the device, we provide you with preliminary analysis including PowerShell logs and prefetch files. What is the name of the file used to enumerate Active Directory objects, which may have been used to discover accounts vulnerable to Kerberoasting attacks on the network?
powerview.ps1
Task 5 When was this script executed?
2024-05-21 03:16:32
Task 6 What is the full path of the tool used to execute the actual Kerberoasting attack?
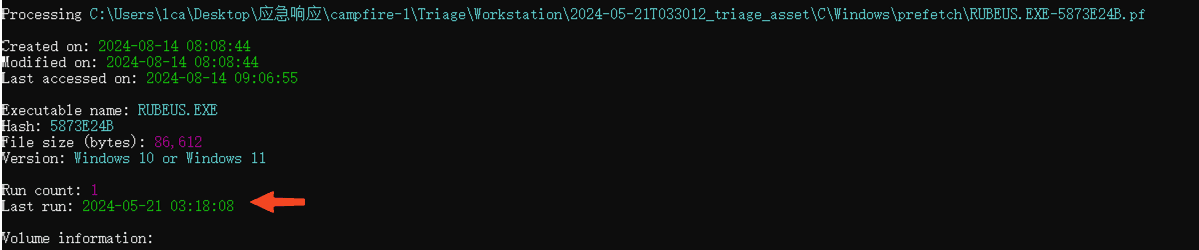
Analyze the RUBEUS.EXE-5873E24B.pf file.
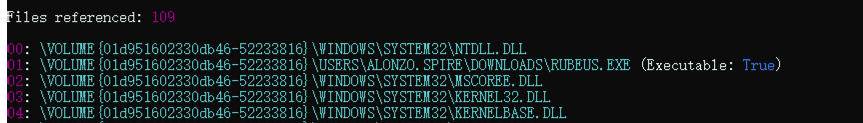
C:\Users\alonzo.spire\Downloads\Rubeus.exe
Task 7 When was the tool executed to dump the credentials?
Check the runtime of the RUBEUS.EXE-5873E24B.pf file.
2024-05-21 03:18:08