0x01 Target Categories#
The basic environment set up can generally be divided into three categories.
-
An environment where the source code is provided, and you need to set it up yourself. The environment can also be built using Docker through a Dockerfile, uploaded to Docker Hub for reuse. The builds for Java and PHP are relatively simple, while building with Docker for ASP/X is less common. Besides Docker, PHP can also be set up using integrated environments like PHPStudy.
-
Docker-based environments, which refer to integrated environments with CVE numbers, such as Vulfocus, Vulhub, etc. These environments have already been set up by others, and we just need to pull them down using Docker.
-
VMware virtual machine target environments, which often involve post-exploitation phases, such as internal network penetration and domain penetration, like the GOAD target.
0x02 Tools#
To do a good job, one must first sharpen their tools.
- Windows (Docker Desktop), Mac (Orb)
- PHPStudy (https://www.xp.cn/download.html)
- CTFd
- GZCTF
If you want to integrate your own built environment or provide practice for colleagues within the company, you can set up a CTF platform, such as CTFd and GZCTF. CTFd combined with the Whale plugin can achieve dynamic flags and add Docker-based environments.
To add targets in CTFd, you can find them on Docker Hub, such as the target environment of Vulfocus.
0x03 PHP Environment#
-
DVWA
-
PHP Code Audit Segmented Explanation
-
Pikachu is a web application system with vulnerabilities, containing common web security vulnerabilities.
- pikachu, can be deployed via Docker
- Online Pikachu-like target: Yuanlong Sec Team Official Vulnerability Target
-
File Upload Target
-
Web Vulnerability Target
webug- Docker setup:
docker pull area39/webug
-
SQL Injection Target
-
XXE Vulnerability Target
-
The official website of Burp Suite official website also provides many web vulnerabilities, all of which are mainstream vulnerabilities.
-
PHP Deserialization Target
-
SSRF Vulnerability Target
-
Electric Rat Target System
-
Learning Target for PHP Command Execution Vulnerabilities
-
PHP Deserialization Docker Environment
https://github.com/mcc0624/php_ser_Class
Docker setup
docker pull mcc0624/ser:1.8
docker run -p 8002:80 -d mcc0624/ser:1.8
0x04 ASP/X Environment#
The ASP environment requires setting up an IIS environment, and you can also use the Super Small Tornado AspWebServer vulnerability environment. The databases paired with ASP are Access and SQL Server, so if you need to use a database, you also need to install it.
0x05 JSP Environment#
- JAVA Vulnerability Target (Vulnerability Environment For Java)
- Java Vulnerability Target
- RASP Testing Target
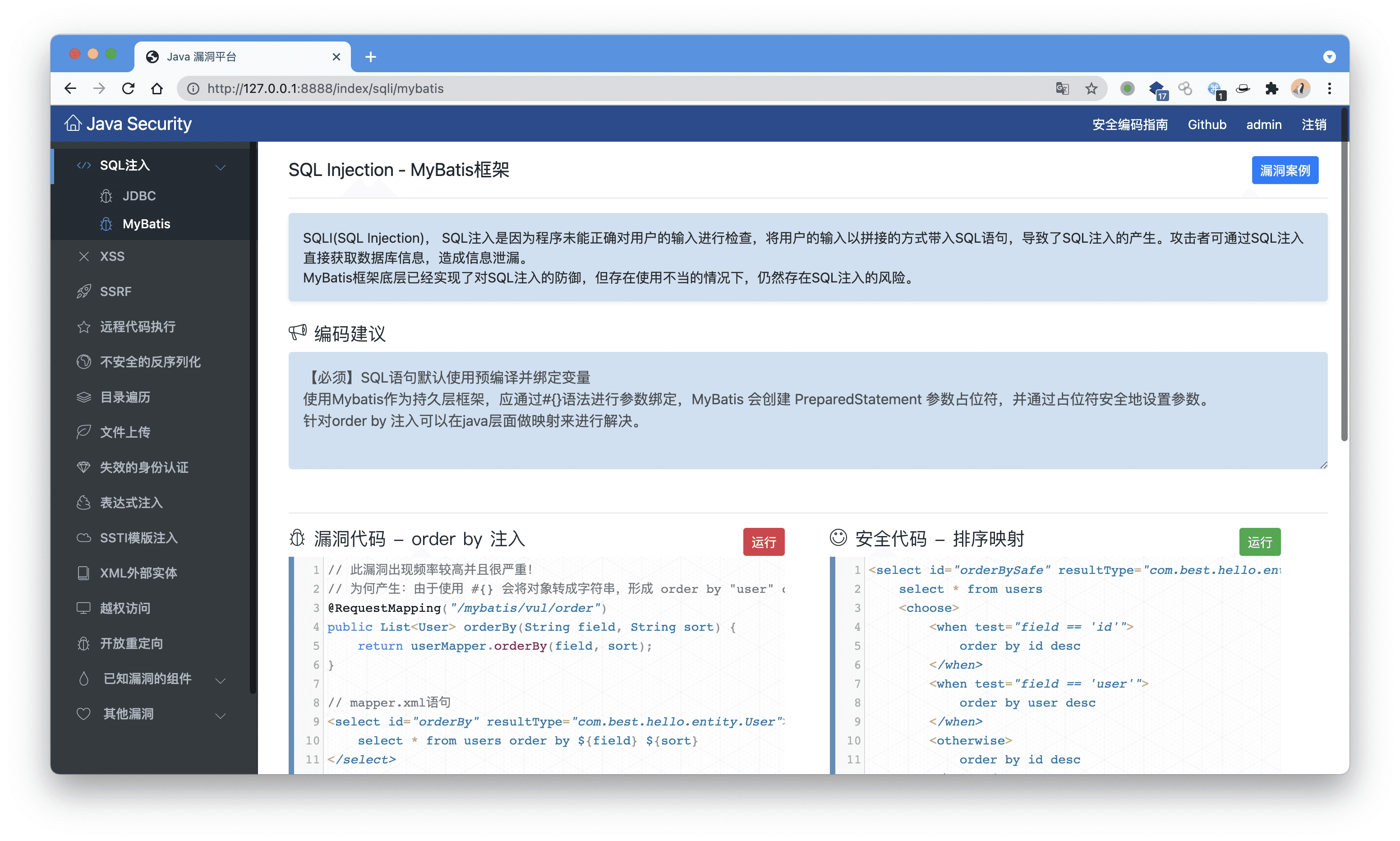
- Java Security, Secure Coding, and Code Audit
- WebLogic Target
- Struts2 Vulnerability Environment
- FastJson All Versions Docker Vulnerability Environment
0x06 Logic Vulnerability Target#
Logic vulnerability target environment installation:
# Install Django and Faker
python -m pip install Django
pip3 install faker
# Initialize Database
First run python manage.py runserver, then access the interface http://127.0.0.1:8000/init_data to initialize the database, and later access http://127.0.0.1:8000/.
A Docker environment was created:
docker pull liangchenga/ljldsec:latest
0x07 Docker Environment#
Using Docker to quickly set up various vulnerability targets, currently, 17 targets can be set up with one click.

The above platform can directly use Docker to set up vulnerability environments with one click.
Vulfocus is a vulnerability integration platform that allows you to use Docker images of vulnerability environments right out of the box. Some vulnerability environments from Vulhub are also available in Vulfocus, so they will not be explained one by one.
docker pull vulfocus/vulfocus:latest
docker run -d -p 80:80 -v /var/run/docker.sock:/var/run/docker.sock -e VUL_IP=x.x.x.x (local IP) vulfocus/vulfocus
# Username and Password: admin/admin
- iwebsec
- docker pull iwebsec/iwebsec
0x08 Virtual Machines#
For virtual machine vulnerability environments, let's first introduce several online websites that do not require downloads.
The quality of these websites is quite high, and there are some that you can try yourself, Websites/Platforms to learn to hack.
Virtual machine targets usually require you to download VMware or VirtualBox OVA format virtual images, and then import them into the virtual machine to run.
There are many virtual machine targets in Vulnhub, with the goal of obtaining flags.
Note: After importing the virtual machine, you first need to obtain the target machine's IP address. Usually, the target machine gets its IP via DHCP, so you will need to use Nmap to scan your current subnet. If there are too many IPs in the subnet, it can be difficult to identify, and if using VMware, there may be cases where you cannot obtain an IP. It is recommended to use VirtualBox for practicing Vulnhub targets. If it is Linux, after importing, enter the password modification mode (press 'e' during boot), change the password, and first obtain the IP.
In addition to Vulnhub targets, there are also some team-built target environments, such as:
- Hongri Security's ATT&CK Practical Series.

- Windows/Linux Local Privilege Escalation Experiment, which includes knowledge points related to privilege escalation.

0x09 Others#
seed-labs: Experimental code and reports involved in network attack and defense courses.